k8s的单节点部署——etcd数据库
- 一、概述
- 二、K8S单节点部署
- 部署etcd数据库
- master操作
- 1、下载证书制作工具
- 2、下载cfssl官方包
- 3、定义ca证书
- 4、实现证书签名
- 5、生产证书,生成ca-key.pem ca.pem
- 6、指定etcd三个节点之间的通信验证
- 7、生成etcd证书
- 8、etcd 二进制包下载
- 9、把下载的安装包拉到centos7中
- 10、进入卡住状态等待其他节点加入
- 11、拷贝证书和脚本去其他节点
- 在node01节点修改
- 在node02节点修改
- 在master上操作
- 在node1和node2上操作
- 检查群集状态(master)
一、概述
官网地址:https://github.com/kubernetes/kubernetes/releases?after=v1.13.1
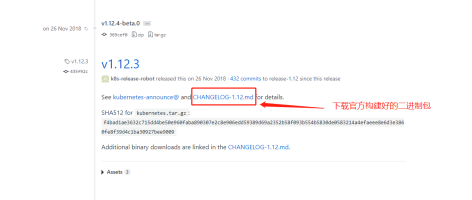
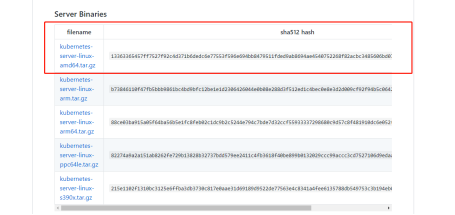
二、K8S单节点部署
| 主机 | IP地址 | 安装服务 |
|---|---|---|
| Master | 192.168.28.10/24 | kube-apiserver kube-controller-manager kube-scheduler etcd |
| Node01 | 192.168.28.20/24 | kubelet kube-proxy docker flannel etcd |
| Node02 | 192.168.28.30/24 | kubelet kube-proxy docker flannel etcd |
部署etcd数据库
master操作
[root@localhost ~]# mkdir k8s
[root@localhost ~]# cd k8s/
[root@localhost k8s]# ls //从宿主机拖进来
etcd-cert.sh etcd.sh
[root@localhost k8s]# mkdir etcd-cert
[root@localhost k8s]# mv etcd-cert.sh etcd-cert
1、下载证书制作工具
[root@localhost k8s]# vim cfssl.sh
curl -L https://pkg.cfssl.org/R1.2/cfssl_linux-amd64 -o /usr/local/bin/cfssl
curl -L https://pkg.cfssl.org/R1.2/cfssljson_linux-amd64 -o /usr/local/bin/cfssljson
curl -L https://pkg.cfssl.org/R1.2/cfssl-certinfo_linux-amd64 -o /usr/local/bin/cfssl-certinfo
chmod +x /usr/local/bin/cfssl /usr/local/bin/cfssljson /usr/local/bin/cfssl-certinfo
2、下载cfssl官方包
[root@localhost k8s]# bash cfssl.sh
[root@localhost k8s]# ls /usr/local/bin/
cfssl cfssl-certinfo cfssljson
3、定义ca证书
cat > ca-config.json <<EOF
{
"signing":
"default": {
"expiry": "87600h"
},
"profiles": {
"www": {
"expiry": "87600h",
"usages": [
"signing",
"key encipherment",
"server auth",
"client auth"
]
}
}
}
}
EOF
4、实现证书签名
cat > ca-csr.json <<EOF
{
"CN": "etcd CA",
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"L": "Beijing",
"ST": "Beijing"
}
]
}
EOF
5、生产证书,生成ca-key.pem ca.pem
cfssl gencert -initca ca-csr.json | cfssljson -bare ca -
2021/04/12 11:35:25 [INFO] generating a new CA key and certificate from CSR
2021/04/12 11:35:25 [INFO] generate received request
2021/04/12 11:35:25 [INFO] received CSR
2021/04/12 11:35:25 [INFO] generating key: rsa-2048
2021/04/12 11:35:26 [INFO] encoded CSR
2021/04/12 11:35:26 [INFO] signed certificate with serial number 53043242530170211717181627042690149476393389144
6、指定etcd三个节点之间的通信验证
cat > server-csr.json <<EOF
{
"CN": "etcd",
"hosts": [
"192.168.28.10",
"192.168.28.20",
"192.168.28.30"
],
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"L": "BeiJing",
"ST": "BeiJing"
}
]
}
EOF
7、生成etcd证书
cfssl gencert -ca=ca.pem -ca-key=ca-key.pem -config=ca-config.json -profile=www server-csr.json | cfssljson -bare server
2021/04/12 12:05:25 [INFO] generate received request
2021/04/12 12:05:25 [INFO] received CSR
2021/04/12 12:05:25 [INFO] generating key: rsa-2048
2021/04/12 12:05:25 [INFO] encoded CSR
2021/04/12 12:05:25 [INFO] signed certificate with serial number 202782620910318985225034109831178600652439985681
2021/04/12 12:05:25 [WARNING] This certificate lacks a "hosts" field. This makes it unsuitable for
websites. For more information see the Baseline Requirements for the Issuance and Management
of Publicly-Trusted Certificates, v.1.1.6, from the CA/Browser Forum (https://cabforum.org);
specifically, section 10.2.3 ("Information Requirements").
8、etcd 二进制包下载
ETCD 二进制包地址:https://github.com/etcd-io/etcd/releases
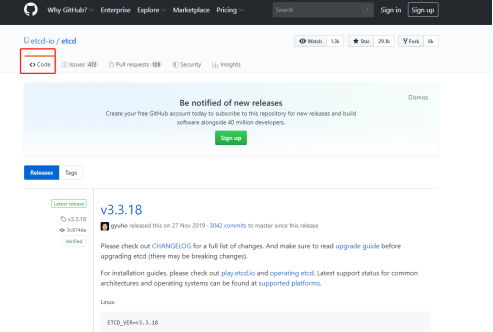
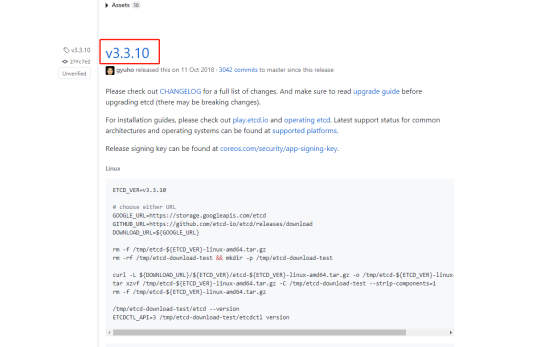
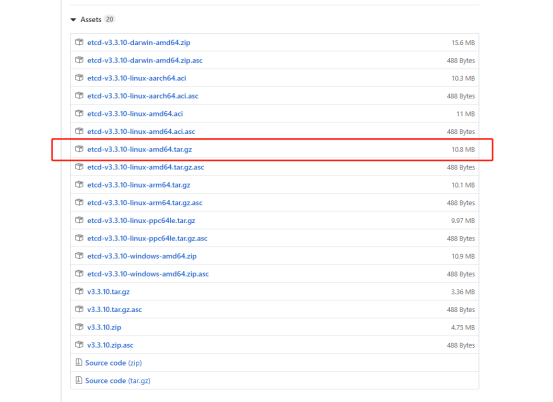
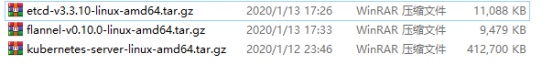
9、把下载的安装包拉到centos7中
[root@localhost etcd-cert]# ls
ca-config.json etcd-cert.sh server-csr.json
ca.csr etcd-v3.3.10-linux-amd64.tar.gz server-key.pem
ca-csr.json flannel-v0.10.0-linux-amd64.tar.gz server.pem
ca-key.pem kubernetes-server-linux-amd64.tar.gz
ca.pem server.csr
[root@localhost etcd-cert]# mv *.tar.gz ../
[root@localhost k8s]# ls
cfssl.sh etcd.sh flannel-v0.10.0-linux-amd64.tar.gz
etcd-cert etcd-v3.3.10-linux-amd64.tar.gz kubernetes-server-linux-amd64.tar.gz
//解压
[root@localhost k8s]# tar zxvf etcd-v3.3.10-linux-amd64.tar.gz
[root@localhost k8s]# ls etcd-v3.3.10-linux-amd64
Documentation etcd etcdctl README-etcdctl.md README.md READMEv2-etcdctl.md
[root@localhost k8s]# mkdir /opt/etcd/{cfg,bin,ssl} -p //配置文件,命令文件,证书
[root@localhost k8s]# mv etcd-v3.3.10-linux-amd64/etcd etcd-v3.3.10-linux-amd64/etcdctl /opt/etcd/bin/
[root@localhost k8s]# cp etcd-cert/*.pem /opt/etcd/ssl/ //证书拷贝
10、进入卡住状态等待其他节点加入
[root@localhost k8s]# bash etcd.sh etcd01 192.168.28.10 etcd02=https://192.168.28.20:2380,etcd03=https://192.168.28.30:2380
//使用另外一个会话打开,会发现etcd进程已经开启
[root@localhost ~]# ps -ef | grep etcd
11、拷贝证书和脚本去其他节点
[root@localhost k8s]# scp -r /opt/etcd/ root@192.168.28.20:/opt/
[root@localhost k8s]# scp -r /opt/etcd/ root@192.168.28.30:/opt
//启动脚本拷贝其他节点
[root@localhost k8s]# scp /usr/lib/systemd/system/etcd.service [root@192.168.28.20:/usr/lib/systemd/system/](mailto:root@192.168.195.129:/usr/lib/systemd/system/)
[root@localhost k8s]# scp /usr/lib/systemd/system/etcd.service [root@192.168.28.30:/usr/lib/systemd/system/](mailto:root@192.168.195.130:/usr/lib/systemd/system/)
在node01节点修改
[root@localhost ~]# vim /opt/etcd/cfg/etcd
#[Member]
ETCD_NAME="etcd02"
ETCD_DATA_DIR="/var/lib/etcd/default.etcd"
ETCD_LISTEN_PEER_URLS="https://192.168.28.20:2380"
ETCD_LISTEN_CLIENT_URLS="https://192.168.28.20:2379"
#[Clustering]
ETCD_INITIAL_ADVERTISE_PEER_URLS="https://192.168.28.20:2380"
ETCD_ADVERTISE_CLIENT_URLS="https://192.168.28.20:2379"
ETCD_INITIAL_CLUSTER="etcd01=https://192.168.28.10:2380,etcd02=https://192.168.28.20:2380,etcd03=https://192.168.28.30:2380"
ETCD_INITIAL_CLUSTER_TOKEN="etcd-cluster"
ETCD_INITIAL_CLUSTER_STATE="new"
在node02节点修改
[root@localhost ~]# vim /opt/etcd/cfg/etcd
#[Member]
ETCD_NAME="etcd03"
ETCD_DATA_DIR="/var/lib/etcd/default.etcd"
ETCD_LISTEN_PEER_URLS="https://192.168.28.30:2380"
ETCD_LISTEN_CLIENT_URLS="https://192.168.28.30:2379"
#[Clustering]
ETCD_INITIAL_ADVERTISE_PEER_URLS="https://192.168.28.30:2380"
ETCD_ADVERTISE_CLIENT_URLS="https://192.168.28.30:2379"
ETCD_INITIAL_CLUSTER="etcd01=https://192.168.28.10:2380,etcd02=https://192.168.28.20:2380,etcd03=https://192.168.28.30:2380"
ETCD_INITIAL_CLUSTER_TOKEN="etcd-cluster"
ETCD_INITIAL_CLUSTER_STATE="new"
在master上操作
[root@localhost k8s]# bash etcd.sh etcd01 192.168.28.10 etcd02=https://192.168.28.20:2380,etcd03=https://192.168.28.30:2380
在node1和node2上操作
[root@localhost ssl]# systemctl start etcd
[root@localhost ssl]# systemctl status etcd
[root@localhost ssl]# systemctl enabled etcd
检查群集状态(master)
[root@master etcd-cert]# /opt/etcd/bin/etcdctl --ca-file=ca.pem --cert-file=server.pem --key-file=server-key.pem --endpoints="https://192.168.28.10:2379,https://192.168.28.20:2379,https://192.168.28.30:2379" cluster-health
member 3be905e4d5795c7c is healthy: got healthy result from https://192.168.28.30:2379
member 4843a272efdf2a43 is healthy: got healthy result from https://192.168.28.10:2379
member 4b65f5b534c1a575 is healthy: got healthy result from https://192.168.28.20:2379
cluster is healthy
注意:在启动node节点的etcd服务时,即systemctl start etcd,一定要先在master节点上执行bash etcd.sh etcd01 192.168.28.10 etcd02=https://192.168.28.20:2380,etcd03=https://192.168.28.30:2380,再启动etcd服务,具体原因我也不清楚,但是在做了好几遍的实验,只有在先执行该命令后,再启动服务,etcd服务才能启动,不然会卡死!
有知道原因的小伙伴们,可以留言告知一下原因!感谢!!希望你们看了会有帮助!
最后
以上就是默默枫叶最近收集整理的关于k8s的单节点部署etcd数据库一、概述二、K8S单节点部署的全部内容,更多相关k8s内容请搜索靠谱客的其他文章。
本图文内容来源于网友提供,作为学习参考使用,或来自网络收集整理,版权属于原作者所有。








发表评论 取消回复