Misc
这次比赛排名在25,还可以。
[VNCTF 2021]Check_In
签到
打开题目底下就是
vnctf{Have_a_good_time!}
[VNCTF 2021]Questionnaire
问卷,做完就给
比赛时候没做这个问卷,导致排名往后掉了几名
vnctf{See_you_next_time}
[VNCTF 2021]冰冰好像藏着秘密
解压出来得到一个png图片,

文件名是FFT我们搜索一下
搜到博里叶变换,我们继续搜一下博里叶变换脚本
因为之前的附件可能存在问题,并没有跑出来,群里出题人重新发了一个附件才解出来的
参考文献:
https://blog.csdn.net/yemeinanhai/article/details/109550549?spm=1001.2014.3001.5501
import numpy as np
import cv2 as cv
from matplotlib import pyplot as plt
img = cv.imread('1.bmp', 0)
f = np.fft.fft2(img)
logf = 20*np.log(np.abs(f))
plt.imshow(logf, 'gray')
plt.show()
得到flag
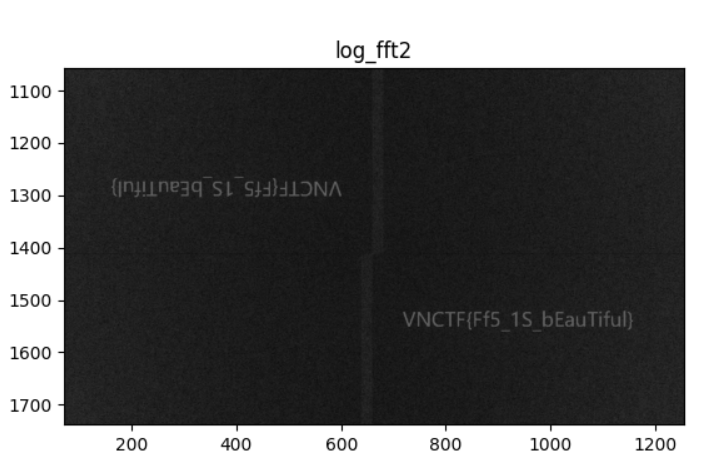
VNCTF{Ff5_1S_bEauTiful}
[VNCTF 2021]Do_you_like_Rhythm_Doctor
我们下载附件,发现文件后缀不对,改成zip
打开发现里面有两个文件
解压一下,
图片没有什么隐写,应该,反正我没找到
我们根据题目,搜了一下节奏医生,找到了编辑器,下载下来并打开文件
之前失败的步骤不写了,
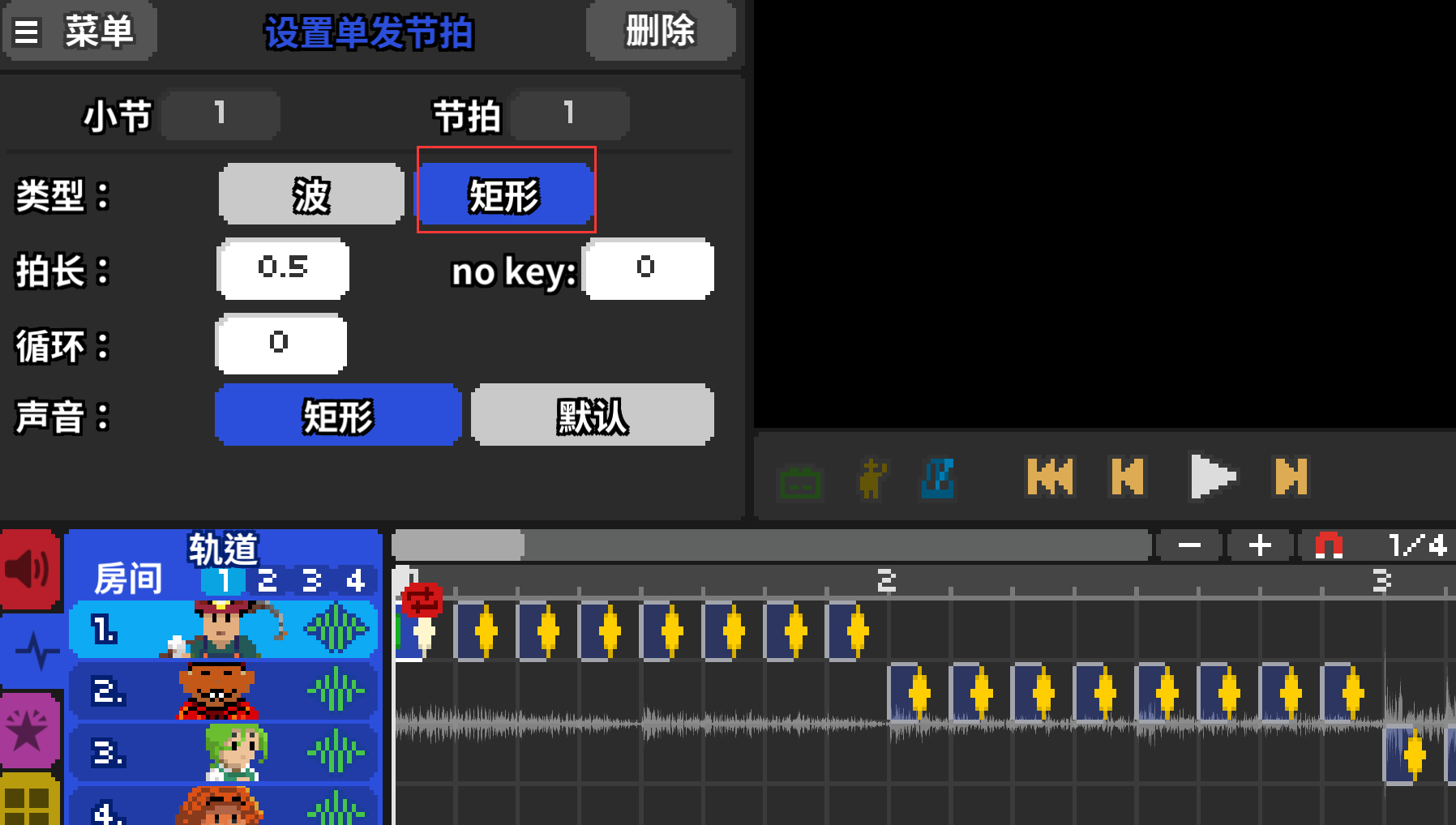
我们看到第一个节拍是矩形
第二个是波形
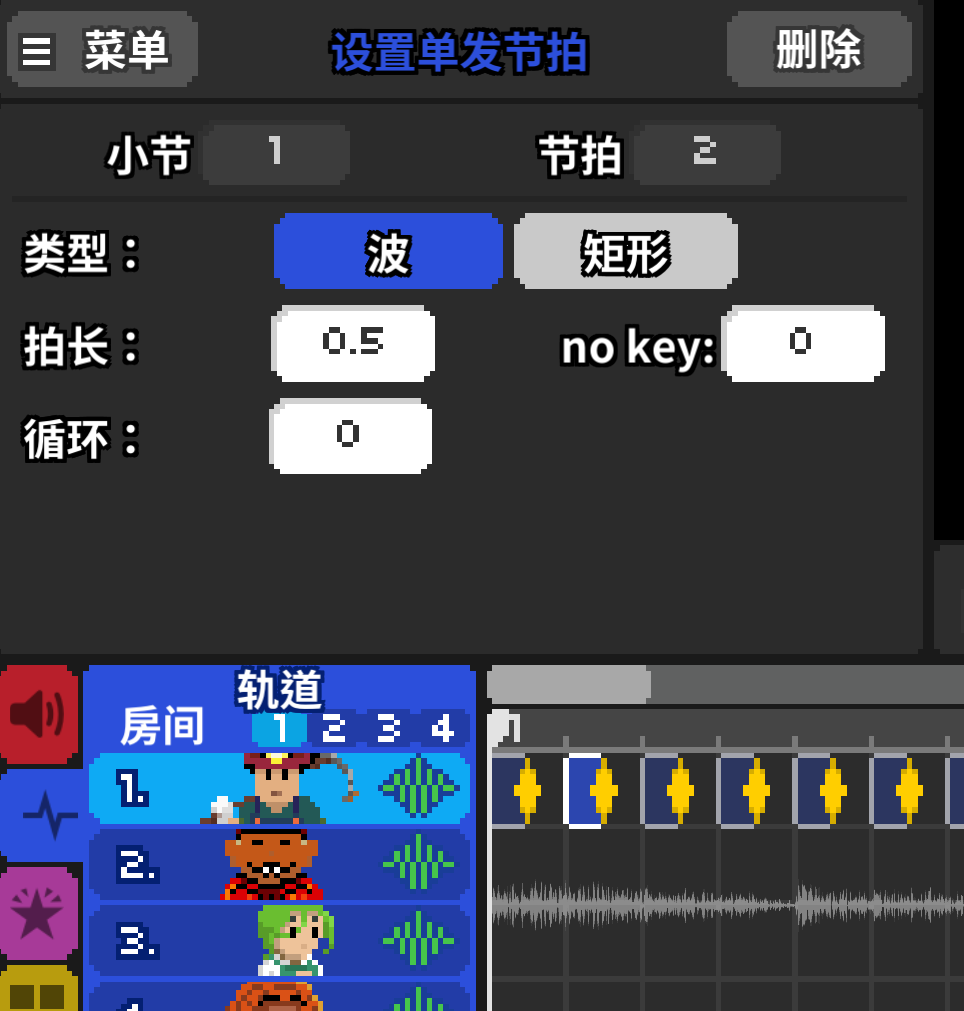
而且节拍正好是8个一组,我们猜测是二进制,并且矩形是零,波形是1,然后一行一行的进行
不要问为什么矩形是0,波形是1,试出来的
得到以下内容,
01100110 01101100 01100001 01100111 1111011
01010111 00110011 00110001 01100011 01101111
01101101 01100101 01011111 01010110 00100110
01001110 01011111 01000011 01010100 01000110 01111101
需要注意的是,在这四行结尾紧凑的那四段节拍,解密出来都是},所以这里我只加了一个
转换一下即可
flag{W31come_V&N_CTF}
[VNCTF 2021]interesting_fishing
题目
crazyman_army是某安全公司的研究人员
这天他的其邮箱里发现了一封奇怪的邮件
你能帮助他找到其隐藏的信息吗
附件是第一部分的flag
图片是第二部分的flag
最后flag为 第一部分+第二部分(vnctf{*})
我们可以看到附件是第一部分,图片是第二部分
解压附件给了两个文件
我们查看注释一下
# 并无卵用
crazyman_army是某安全公司的研究人员
这天他的其邮箱里发现了一封奇怪的邮件
你能帮助他找到其隐藏的信息吗
注意:
附件是第一部分的flag
图片是第二部分的flag
最后flag为 第一部分+第二部分
hint:powershell解码后的字符可能存在不可读的情况 那并不是解码错误
我们先将bin改为eml后缀
然后,我们用工具foxemil打开这个附件。会得到一个图片和一个压缩包
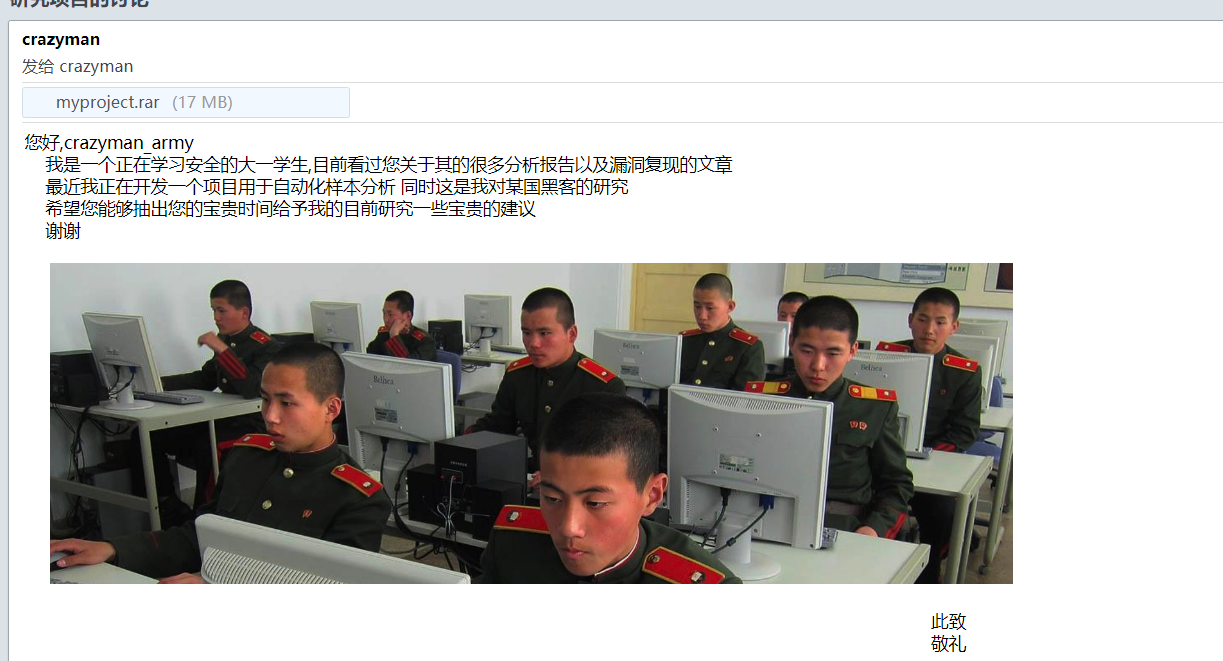
这两个文件都给扒下来
之前解题失败步骤不重复。
图片用OurSecret打开
根据文件名称,猜测是Secret
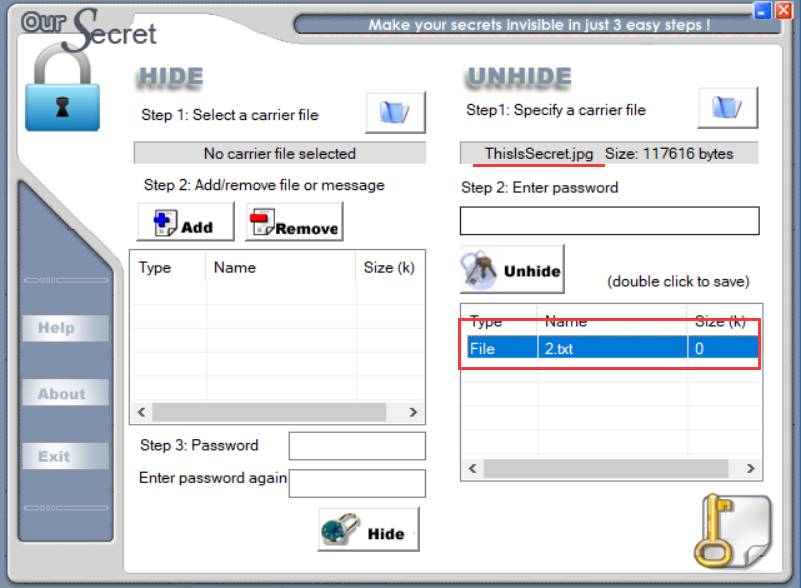
打开文件会得到后半部分flag
我们在查看压缩包
将文件解压出来,因为没有提示,我们挨个文件看
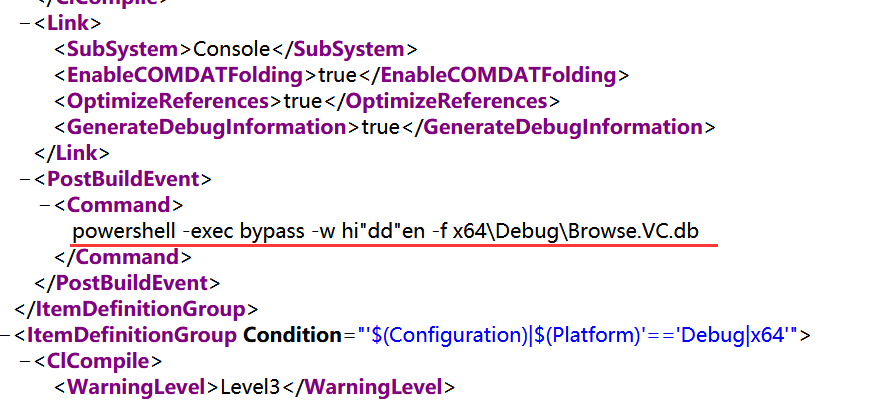
被我们找到了这个文件,我们发现文件中并没有该文件,我们返回rar中查找一下
发现在一下路径中有Browse.VC.db
myprojectgiveyourflaggiveyourflagx64Debug
继续返回文件中查看,发现就是没有,我们单独将这个文件解压出来,解压出来发现还是没有这个文件。
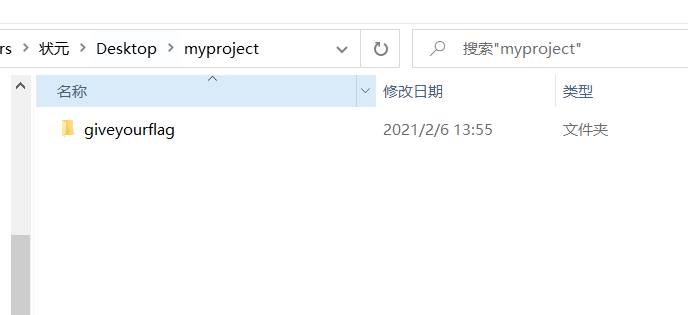
我们猜测进行了文件隐藏。
找到文件夹选项,把红线标记处取消勾选
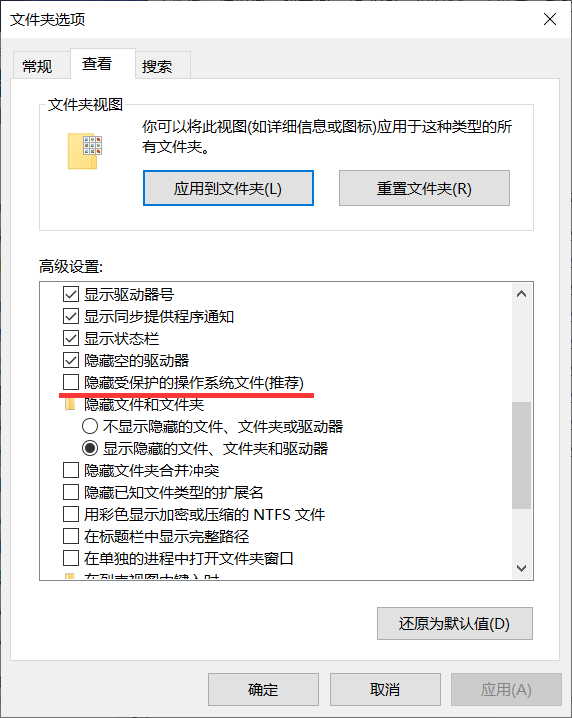
会发现目录下多出一个文件
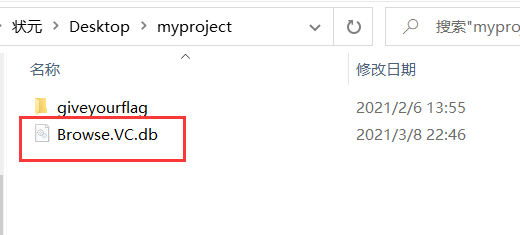
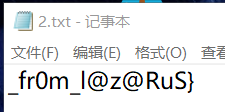
用记事本打开
得到以下信息
$encodestring = "XAB1AC0ANgA1ADQAMwAyAD8AXAB1AC0ANgA1ADQAMgAwAD8AXAB1AC0ANgA1ADQAMgAwAD8AXAB1AC0ANgA1ADQAMgA0AD8AXAB1AC0ANgA1ADQAMgAxAD8AXAB1AC0ANgA1ADQANwA4AD8AXAB1AC0ANgA1ADQAOAA5AD8AXAB1AC0ANgA1ADQAOAA5AD8AXAB1AC0ANgA1ADQAMQA4AD8AXAB1AC0ANgA1ADQAMgA2AD8AXAB1AC0ANgA1ADQAMwA3AD8AXAB1AC0ANgA1ADQAMgAwAD8AXAB1AC0ANgA1ADQAMwA0AD8AXAB1AC0ANgA1ADQAOQAxAD8AXAB1AC0ANgA1ADQAOAA2AD8AXAB1AC0ANgA1ADQAOAA3AD8AXAB1AC0ANgA1ADQAOAA1AD8AXAB1AC0ANgA1ADQAOQAxAD8AXAB1AC0ANgA1ADQAOAA3AD8AXAB1AC0ANgA1ADQAOAA2AD8AXAB1AC0ANgA1ADQAOAAzAD8AXAB1AC0ANgA1ADQAOAAxAD8AXAB1AC0ANgA1ADQAOAA4AD8AXAB1AC0ANgA1ADQAOAAyAD8AXAB1AC0ANgA1ADQAOAA3AD8AXAB1AC0ANgA1ADQAOAA3AD8AXAB1AC0ANgA1ADQAOAA2AD8AXAB1AC0ANgA1ADQAOAA1AD8AXAB1AC0ANgA1ADQAOQAwAD8AXAB1AC0ANgA1ADQAMwA3AD8AXAB1AC0ANgA1ADQAMgA1AD8AXAB1AC0ANgA1ADQAMgAxAD8AXAB1AC0ANgA1ADQAOQAwAD8AXAB1AC0ANgA1ADQAMwA5AD8AXAB1AC0ANgA1ADQAMgA0AD8AXAB1AC0ANgA1ADQAOQAxAD8AXAB1AC0ANgA1ADQAMgA2AD8AXAB1AC0ANgA1ADQAMwA5AD8AXAB1AC0ANgA1ADQAMgA2AD8AXAB1AC0ANgA1ADQAMwAwAD8AXAB1AC0ANgA1ADQAMwAxAD8AXAB1AC0ANgA1ADQAMgA2AD8AXAB1AC0ANgA1ADQAMwAzAD8AXAB1AC0ANgA1ADQAOQAwAD8AXAB1AC0ANgA1ADQAMgA3AD8AXAB1AC0ANgA1ADQAMQA1AD8AXAB1AC0ANgA1ADQAMgAzAD8AXAB1AC0ANgA1ADQAMwA3AD8AXAB1AC0ANgA1ADQAMgA4AD8AXAB1AC0ANgA1ADQAMgA1AD8AXAB1AC0ANgA1ADQAMQA5AD8AXAB1AC0ANgA1ADQAMwA2AD8AXAB1AC0ANgA1ADQAOQAwAD8AXAB1AC0ANgA1ADQAMwA3AD8AXAB1AC0ANgA1ADQAMgA1AD8AXAB1AC0ANgA1ADQAMgA3AD8AXAB1AC0ANgA1ADQAOAA5AD8AXAB1AC0ANgA1ADQANQA2AD8AXAB1AC0ANgA1ADQAMQA1AD8AXAB1AC0ANgA1ADQAMgA1AD8AXAB1AC0ANgA1ADQAMgA2AD8AXAB1AC0ANgA1ADQAMwAzAD8AXAB1AC0ANgA1ADQAMQA1AD8AXAB1AC0ANgA1ADQAMwA5AD8AXAB1AC0ANgA1ADQAMgA2AD8AXAB1AC0ANgA1ADQAMwAzAD8AXAB1AC0ANgA1ADQAOQA5AD8AXAB1AC0ANgA1ADQAOAA2AD8AXAB1AC0ANgA1ADQAOAA4AD8AXAB1AC0ANgA1ADQAMgAxAD8AXAB1AC0ANgA1ADQAMgAwAD8AXAB1AC0ANgA1ADQAMgA1AD8AXAB1AC0ANgA1ADQAMgAyAD8AXAB1AC0ANgA1ADQAMwA1AD8AXAB1AC0ANgA1ADQAMgAxAD8AXAB1AC0ANgA1ADQAOQA5AD8AXAB1AC0ANgA1ADQAOAA2AD8AXAB1AC0ANgA1ADQAOAA4AD8AXAB1AC0ANgA1ADQAMgA4AD8AXAB1AC0ANgA1ADQAMgA1AD8AXAB1AC0ANgA1ADQAMQA3AD8AXAB1AC0ANgA1ADQAOQA5AD8AXAB1AC0ANgA1ADQAOAA2AD8AXAB1AC0ANgA1ADQAOAA4AD8AXAB1AC0ANgA1ADQAMgA1AD8AXAB1AC0ANgA1ADQAMgA2AD8AXAB1AC0ANgA1ADQAOQA5AD8AXAB1AC0ANgA1ADQAOAA2AD8AXAB1AC0ANgA1ADQAOAA4AD8AXAB1AC0ANgA1ADQAMwA0AD8AXAB1AC0ANgA1ADQAMgA1AD8AXAB1AC0ANgA1ADQAMgAyAD8AXAB1AC0ANgA1ADQAMwA1AD8AXAB1AC0ANgA1ADQAMwAxAD8AXAB1AC0ANgA1ADQAMwAzAD8AXAB1AC0ANgA1ADQAMgA2AD8AXAB1AC0ANgA1ADQAOQA5AD8AXAB1AC0ANgA1ADQAOAA2AD8AXAB1AC0ANgA1ADQAOAA4AD8AXAB1AC0ANgA1ADQAMwAzAD8AXAB1AC0ANgA1ADQAMgA1AD8AXAB1AC0ANgA1ADQAMgA1AD8AXAB1AC0ANgA1ADQAMwA2AD8AXAB1AC0ANgA1ADQAMgAxAD8AXAB1AC0ANgA1ADQAOQA5AD8AXAB1AC0ANgA1ADQAOAA2AD8AXAB1AC0ANgA1ADQAOAA4AD8AXAB1AC0ANgA1ADQAMwA5AD8AXAB1AC0ANgA1ADQAMgA3AD8AXAB1AC0ANgA1ADQAMwAxAD8AXAB1AC0ANgA1ADQAMwA2AD8AXAB1AC0ANgA1ADQAOQA5AD8AXAB1AC0ANgA1ADQAOAA2AD8AXAB1AC0ANgA1ADQAOAA4AD8AXAB1AC0ANgA1ADQANQA4AD8AXAB1AC0ANgA1ADQAMgA1AD8AXAB1AC0ANgA1ADQAMgAyAD8AXAB1AC0ANgA1ADQAMgAwAD8AXAB1AC0ANgA1ADQAMwAyAD8AXAB1AC0ANgA1ADQAOQA5AD8AXAB1AC0ANgA1ADQAOAA2AD8AXAB1AC0ANgA1ADQAOAA4AD8AXAB1AC0ANgA1ADQANgAxAD8AXAB1AC0ANgA1ADQAMgA1AD8AXAB1AC0ANgA1ADQAMgAyAD8AXAB1AC0ANgA1ADQAMwA1AD8AXAB1AC0ANgA1ADQAMwA5AD8AXAB1AC0ANgA1ADQAMgA2AD8AXAB1AC0ANgA1ADQAOQA5AD8AXAB1AC0ANgA1ADQAOAA2AD8AXAB1AC0ANgA1ADQAOAA4AD8AXAB1AC0ANgA1ADQANgA5AD8AXAB1AC0ANgA1ADQANQA3AD8AXAB1AC0ANgA1ADQANQAwAD8AXAB1AC0ANgA1ADQANgAzAD8AXAB1AC0ANgA1ADQANgA4AD8AXAB1AC0ANgA1ADQAOQAxAD8AXAB1AC0ANgA1ADQAOAA3AD8AXAB1AC0ANgA1ADQANwA5AD8AXAB1AC0ANgA1ADQAOQA5AD8AXAB1AC0ANgA1ADQAOAA2AD8AXAB1AC0ANgA1ADQAOAA4AD8AXAB1AC0ANgA1ADQAMgA0AD8AXAB1AC0ANgA1ADQAMwA5AD8AXAB1AC0ANgA1ADQAMgAyAD8AXAB1AC0ANgA1ADQAMwA5AD8AXAB1AC0ANgA1ADQAMgA2AD8AXAB1AC0ANgA1ADQAMgA1AD8AXAB1AC0ANgA1ADQAMwAxAD8AXAB1AC0ANgA1ADQAMwA5AD8AXAB1AC0ANgA1ADQAOQAwAD8AXAB1AC0ANgA1ADQAMgAyAD8AXAB1AC0ANgA1ADQAMwA5AD8AXAB1AC0ANgA1ADQAMgAyAD8A"
$bytes = [System.Convert]::FromBase64String($string);
$decoded = [System.Text.Encoding]::UTF8.GetString($bytes);
echo $decoded
将中间部分内容进行base64解密
得到以下内容
u-65432?u-65420?u-65420?u-65424?u-65421?u-65478?u-65489?u-65489?u-65418?u-65426?u-65437?u-65420?u-65434?u-65491?u-65486?u-65487?u-65485?u-65491?u-65487?u-65486?u-65483?u-65481?u-65488?u-65482?u-65487?u-65487?u-65486?u-65485?u-65490?u-65437?u-65425?u-65421?u-65490?u-65439?u-65424?u-65491?u-65426?u-65439?u-65426?u-65430?u-65431?u-65426?u-65433?u-65490?u-65427?u-65415?u-65423?u-65437?u-65428?u-65425?u-65419?u-65436?u-65490?u-65437?u-65425?u-65427?u-65489?u-65456?u-65415?u-65425?u-65426?u-65433?u-65415?u-65439?u-65426?u-65433?u-65499?u-65486?u-65488?u-65421?u-65420?u-65425?u-65422?u-65435?u-65421?u-65499?u-65486?u-65488?u-65428?u-65425?u-65417?u-65499?u-65486?u-65488?u-65425?u-65426?u-65499?u-65486?u-65488?u-65434?u-65425?u-65422?u-65435?u-65431?u-65433?u-65426?u-65499?u-65486?u-65488?u-65433?u-65425?u-65425?u-65436?u-65421?u-65499?u-65486?u-65488?u-65439?u-65427?u-65431?u-65436?u-65499?u-65486?u-65488?u-65458?u-65425?u-65422?u-65420?u-65432?u-65499?u-65486?u-65488?u-65461?u-65425?u-65422?u-65435?u-65439?u-65426?u-65499?u-65486?u-65488?u-65469?u-65457?u-65450?u-65463?u-65468?u-65491?u-65487?u-65479?u-65499?u-65486?u-65488?u-65424?u-65439?u-65422?u-65439?u-65426?u-65425?u-65431?u-65439?u-65490?u-65422?u-65439?u-65422?
RTF格式
用65536减去之后,进行数据转换,获得网址
https://vnctf-213-1257061123.cos.ap-nanjing-myqcloud.com/Pyongyang%20stores%20low%20on%20foreign%20goods%20amid%20North%20Korean%20COVID-19%20paranoia.rar
下载下来
提示密码是四位数
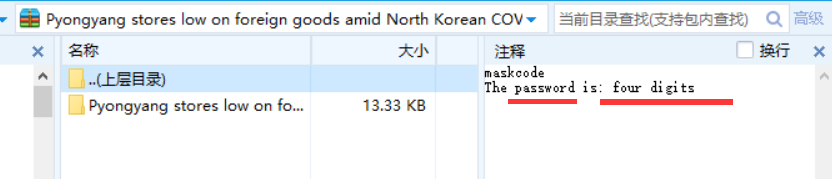
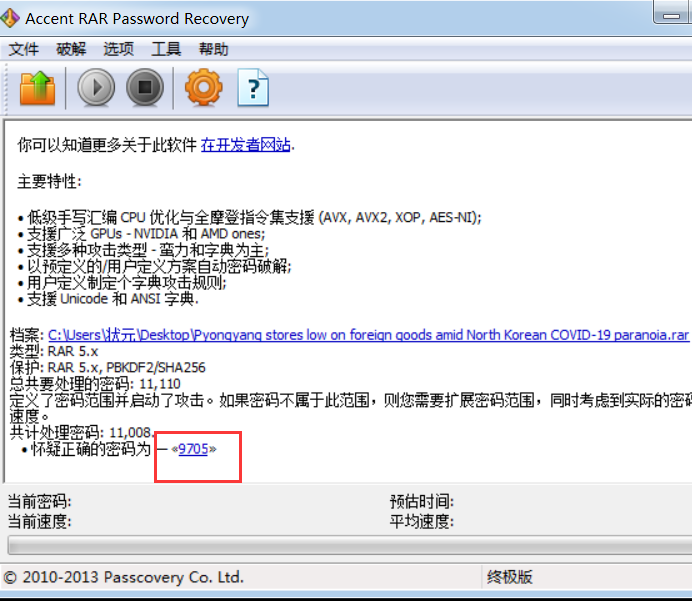
我们进行RAR爆破,使用工具Accent RAR Password Recovery
得到密码9705
解压出来word文件
打开得到以下内容
Pyongyang stores low on foreign goods amid North Korean COVID-19 paranoia
Amid an ongoing, full-scale border lockdown against COVID-19, North Korea on Tuesday warned its citizens against relying on imported foreign goods — calling the habit a dangerous “disease” that could spread the virus from abroad.
Pyongyang’s warning against bringing in foreign goods is not just empty words, either: On Monday, sources told VOA that supermarkets and shops in Pyongyang have lacked foreign-sourced staples for months, including coffee, cocoa and chocolate. This appears to be out of paranoia that foreign goods could carry traces of COVID-19 — which is possible, according to the United Nations, though not the most common way the virus has been transmitted worldwide.
Sources also told VOA that there’s currently no evidence that food items are coming across the border from China, with only locally produced items available on Pyongyang store shelves.
INTENSE BORDER CONTROL
Tuesday’s state-run Rodong Sinmun newspaper cautioned against the country’s long-standing “importation fever” (수입병), which comes as the North continues a strict border control. The DPRK even set up “shoot on sight” zones along its border with China for fear that travelers could carry the virus. Meanwhile, the country is operating under the contested premise that items, air and even yellow dust pollution could carry COVID-19 across borders.
“The most entangling issue today on [the DPRK] demon
有点难受,看不懂
我们将文件放到winhex中发现文件是zip文件头
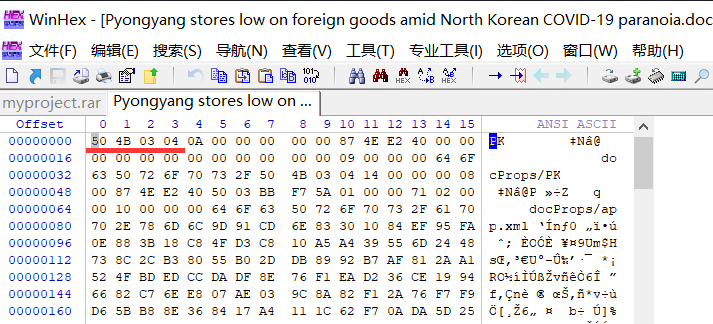
改一下后缀,解压
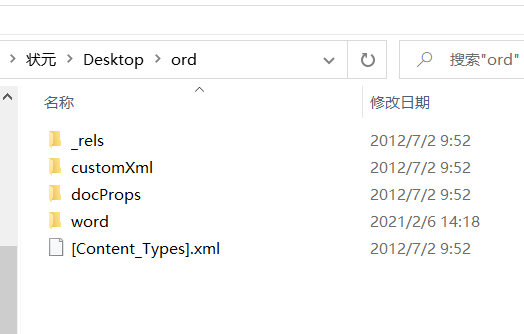
经过尝试进入word目录找到,hideinfo.xml
放到winhex查看一下
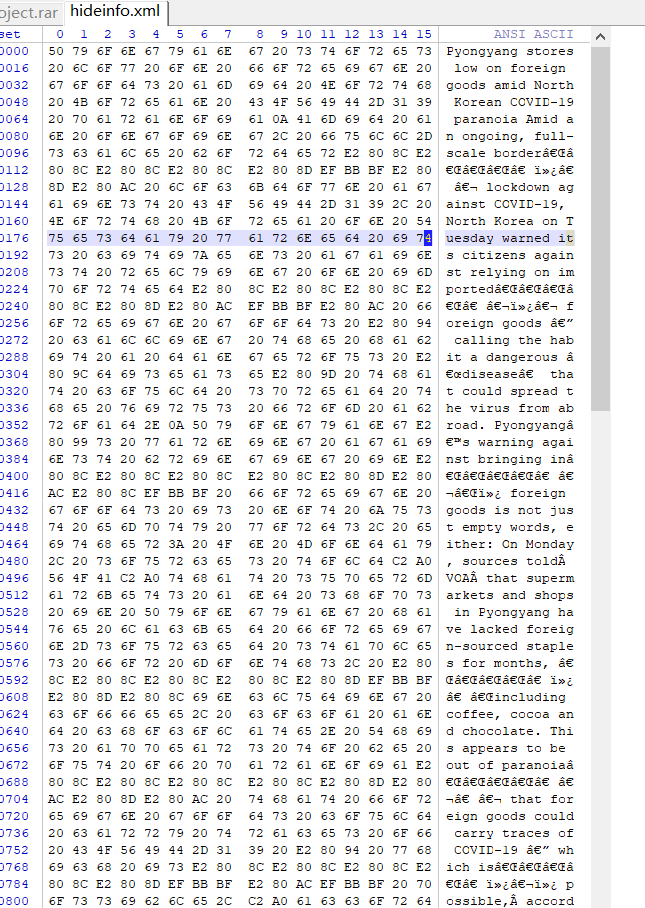
发现是零宽隐写
用记事本打开,得到以下内容
Pyongyang stores low on foreign goods amid North Korean COVID-19 paranoia
Amid an ongoing, full-scale border lockdown against COVID-19, North Korea on Tuesday warned its citizens against relying on imported foreign goods — calling the habit a dangerous “disease” that could spread the virus from abroad.
Pyongyang’s warning against bringing in foreign goods is not just empty words, either: On Monday, sources told VOA that supermarkets and shops in Pyongyang have lacked foreign-sourced staples for months, including coffee, cocoa and chocolate. This appears to be out of paranoia that foreign goods could carry traces of COVID-19 — which is possible, according to the United Nations, though not the most common way the virus has been transmitted worldwide.
Sources also told VOA that there’s currently no evidence that food items are coming across the border from China, with only locally produced items available on Pyongyang store shelves.
INTENSE BORDER CONTROL
Tuesday’s state-run Rodong Sinmun newspaper cautioned against the country’s long-standing “importation fever” (수입병), which comes as the North continues a strict border control. The DPRK even set up “shoot on sight” zones along its border with China for fear that travelers could carry the virus. Meanwhile, the country is operating under the contested premise that items, air and even yellow dust pollution could carry COVID-19 across borders.
“The most entangling issue today on [the DPRK] demon
零宽隐写
[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-VipUW8VY-1615891305446)(VNCTF2021.assets/image-20210316181154455.png)]
vncWthfe{APre T_1Sa_mc0 M1nGI?_fr0m_l@z@RuS}
Web
[VNCTF 2021]Ez_game
JS泄露
F12一下可以看到game.js等三个js文件
我们查看一下,发现game.js开头是实例化,玩家信息我们在页面Ctrl+Shift+F搜索一下
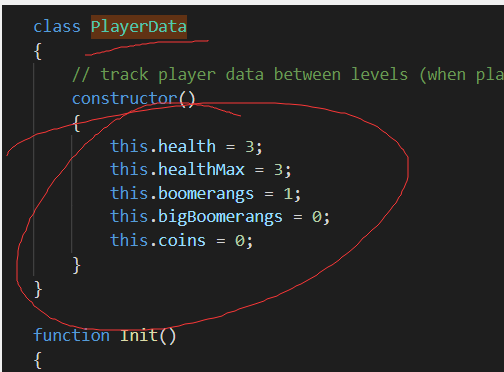
更改一下参数,改为999999即可,改的太大,会卡死

然后F12在控制台跳一下关NextLevel(),一直跳就得到了flag。
一开始是跳到第九关然后打死的。后面才知道这个方法
如果一直跳关的话,也可以不改上面参数
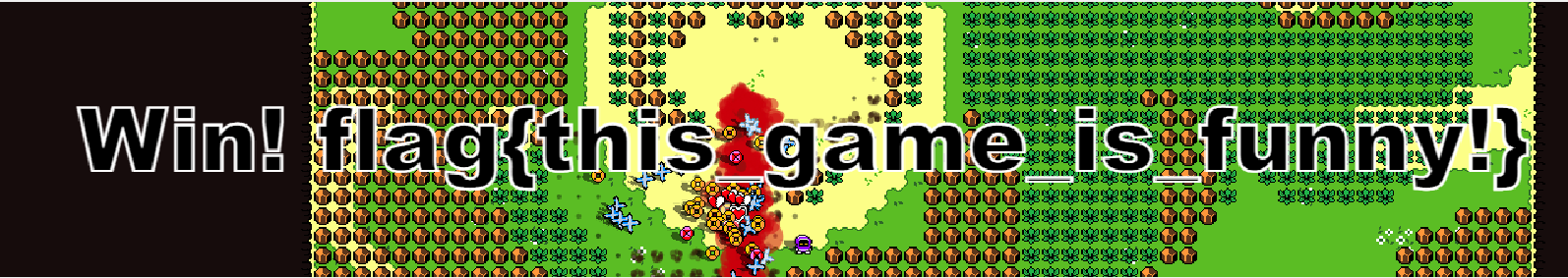
flag{this_game_is_funny!}
最后
以上就是执着帆布鞋最近收集整理的关于VNCTF2021 misc wp的全部内容,更多相关VNCTF2021内容请搜索靠谱客的其他文章。








发表评论 取消回复