我是靠谱客的博主 俊逸溪流,这篇文章主要介绍HSCTF2021 rebaigeiRSA2^11baigeiXorAstarEstarSFMC_pyReverse-Fighting,现在分享给大家,希望可以做个参考。
baigeiRSA
import libnum
from Crypto.Util import number
from secret import flag
size = 128
e = 65537
p = number.getPrime(size)
q = number.getPrime(size)
n = p*q
m = libnum.s2n(flag)
c = pow(m, e, n)
print('n = %d' % n)
print('c = %d' % c)
真白给
直接写
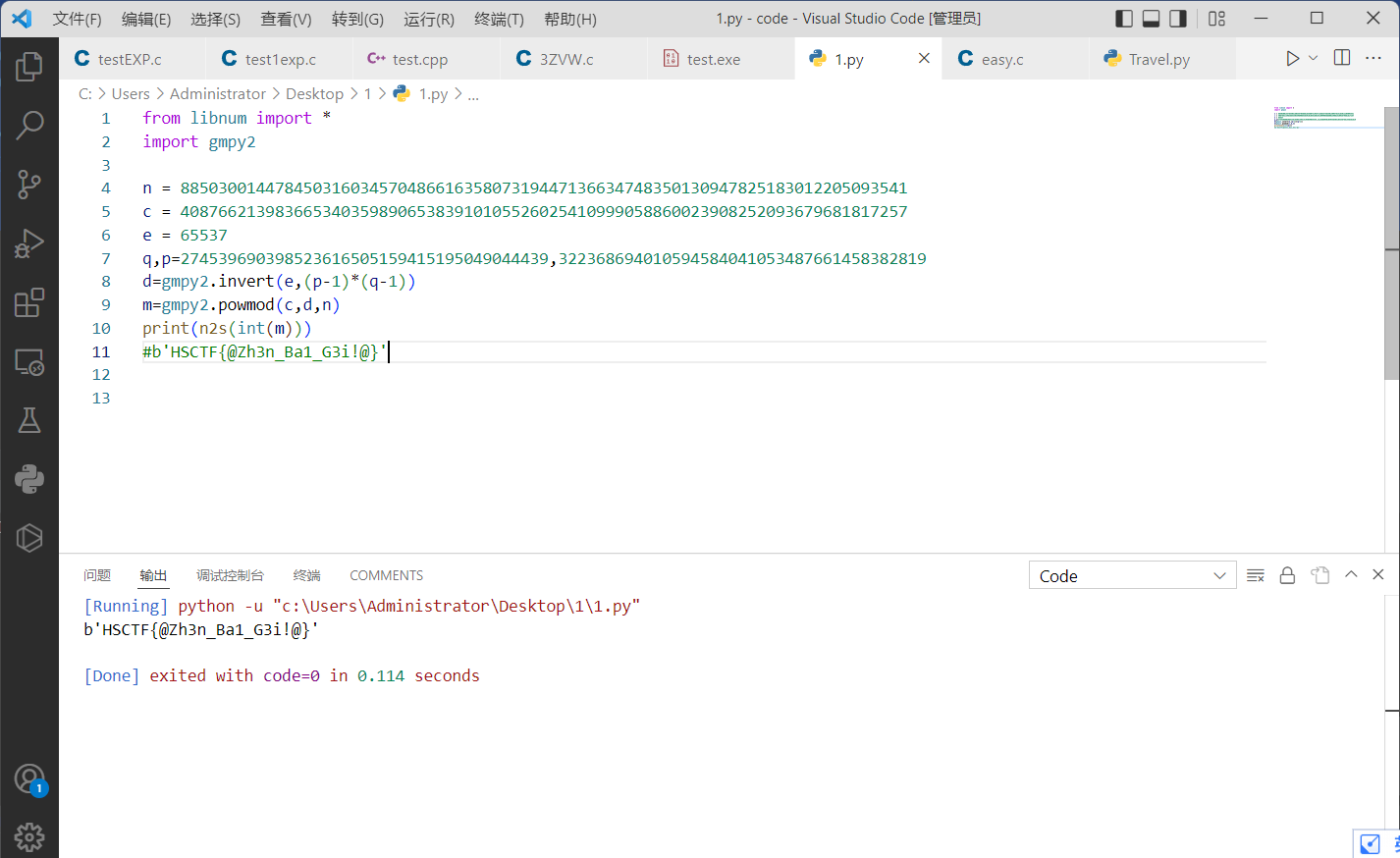
from libnum import *
import gmpy2
n = 88503001447845031603457048661635807319447136634748350130947825183012205093541
c = 40876621398366534035989065383910105526025410999058860023908252093679681817257
e = 65537
q,p=274539690398523616505159415195049044439,322368694010594584041053487661458382819
d=gmpy2.invert(e,(p-1)*(q-1))
m=gmpy2.powmod(c,d,n)
print(n2s(int(m)))
#b'HSCTF{@Zh3n_Ba1_G3i!@}'
2^11
貌似是一个游戏

用IDA打开
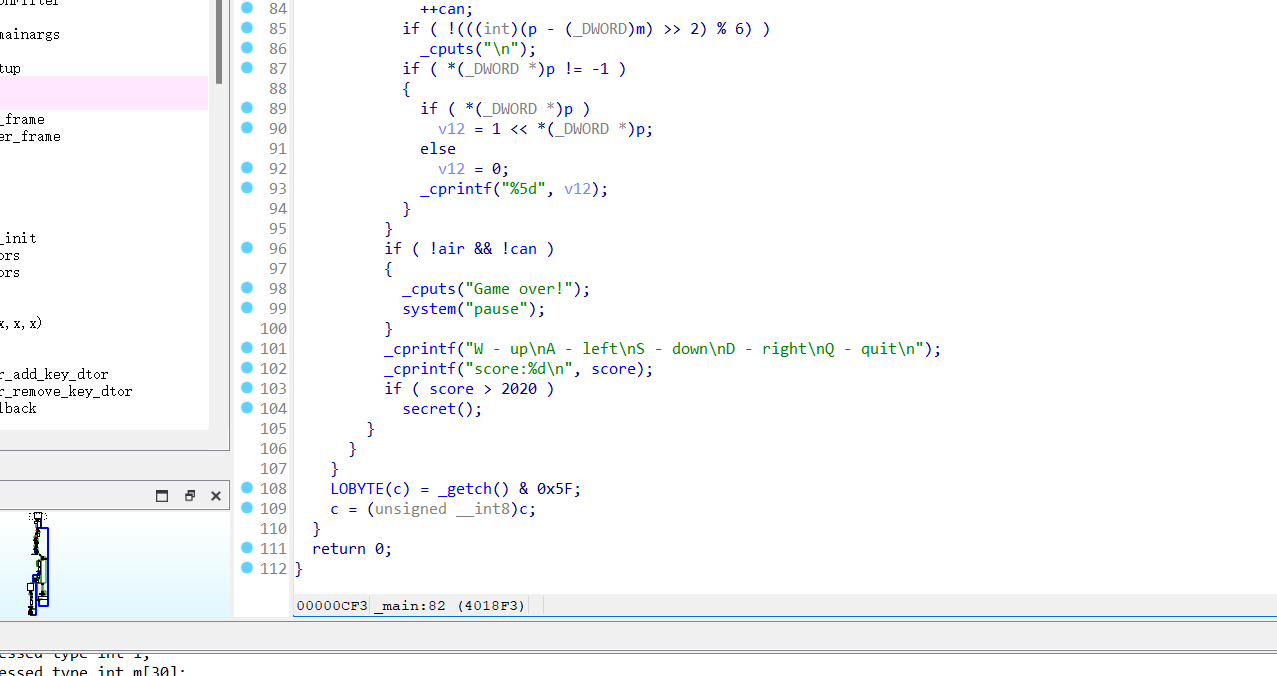
貌似分要过2020
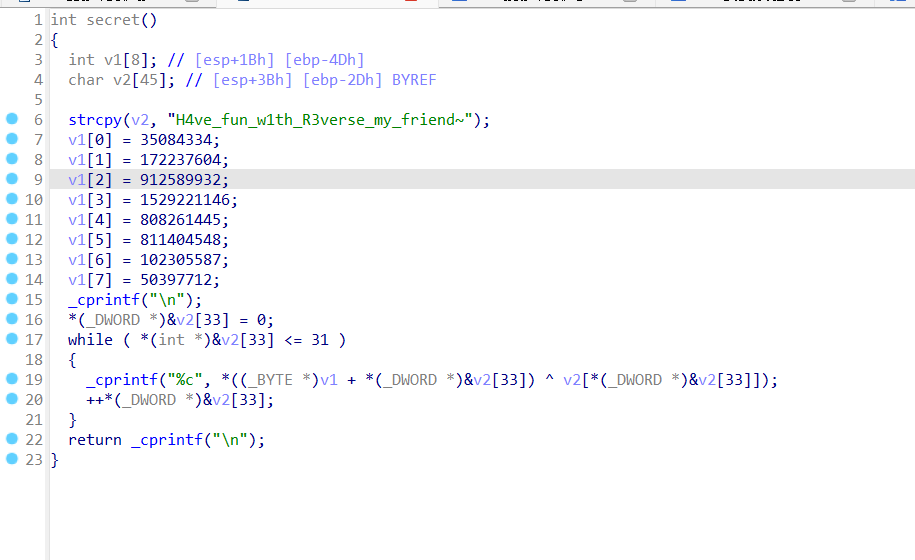
直接逆向
EXP
#include<string.h>
#include<stdio.h>
#include<windows.h>
int main(){
int v1[8]; // [esp+1Bh] [ebp-4Dh]
char v2[45]; // [esp+3Bh] [ebp-2Dh] BYREF
strcpy(v2, "H4ve_fun_w1th_R3verse_my_friend~");
v1[0] = 35084334;
v1[1] = 172237604;
v1[2] = 912589932;
v1[3] = 1529221146;
v1[4] = 808261445;
v1[5] = 811404548;
v1[6] = 102305587;
v1[7] = 50397712;
int i;
for(i = 0;i<=31;++i){
printf("%C",*((BYTE *)v1 + i) ^ v2[i]);
}
return 0;
}
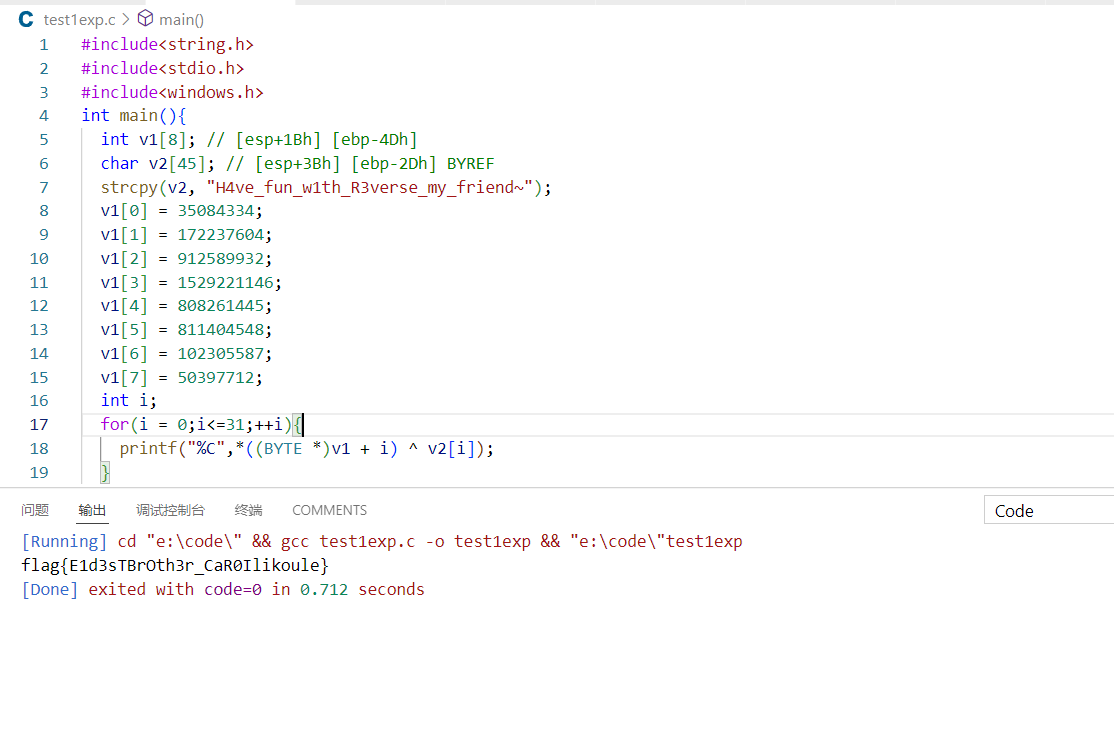
baigeiXor
ELF文件,直接弄
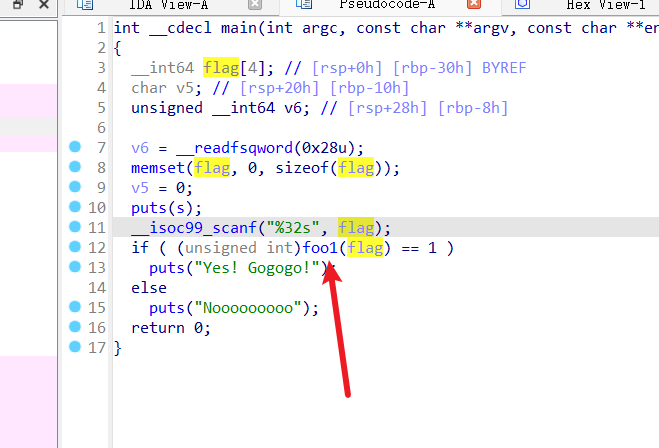
有个加密函数
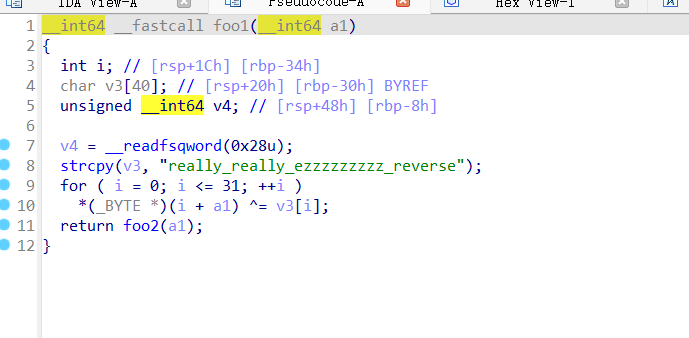
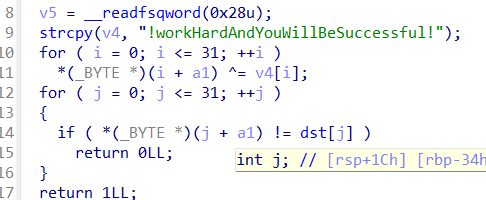
找到密文存放位置
直接逆向EXP
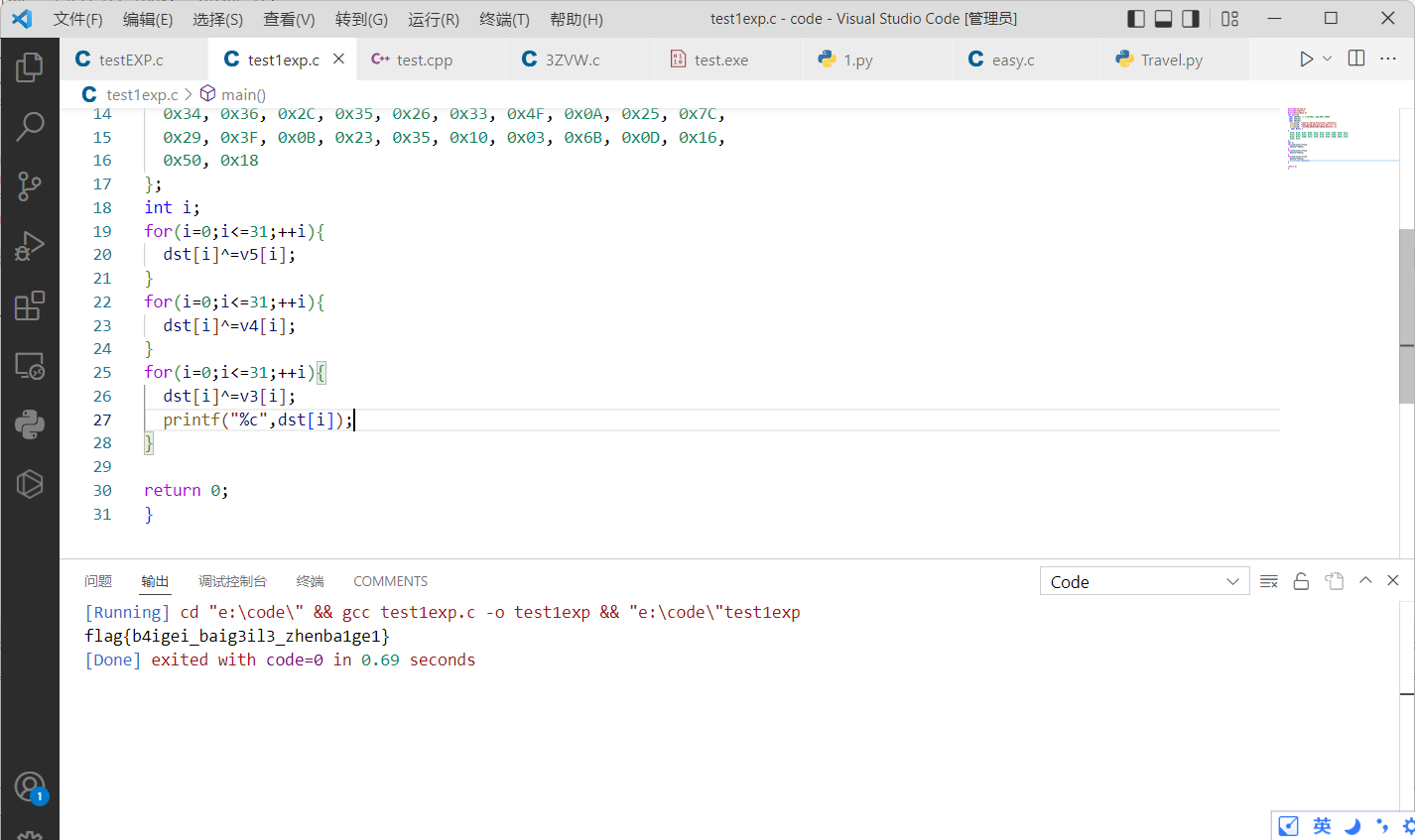
#include<string.h>
#include<stdio.h>
#include<windows.h>
int main(){
char v3[40]; // [rsp+20h] [rbp-30h] BYREF
char v4[40];
char v5[40];
strcpy(v3, "really_really_ezzzzzzzzz_reverse");
strcpy(v4, "keep_going_and_you_will_get_it~!");
strcpy(v5, "!workHardAndYouWillBeSuccessful!");
char dst[] =
{
0x5E, 0x1B, 0x0A, 0x09, 0x23, 0x34, 0x65, 0x00, 0x08, 0x22,
0x34, 0x36, 0x2C, 0x35, 0x26, 0x33, 0x4F, 0x0A, 0x25, 0x7C,
0x29, 0x3F, 0x0B, 0x23, 0x35, 0x10, 0x03, 0x6B, 0x0D, 0x16,
0x50, 0x18
};
int i;
for(i=0;i<=31;++i){
dst[i]^=v5[i];
}
for(i=0;i<=31;++i){
dst[i]^=v4[i];
}
for(i=0;i<=31;++i){
dst[i]^=v3[i];
printf("%c",dst[i]);
}
return 0;
}
AstarEstarS
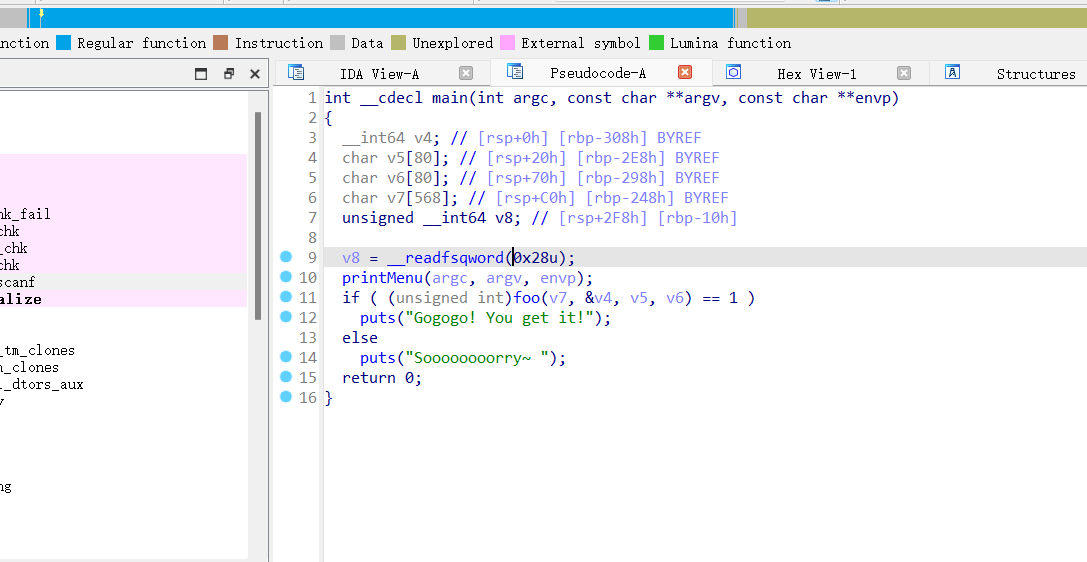
进入关键函数
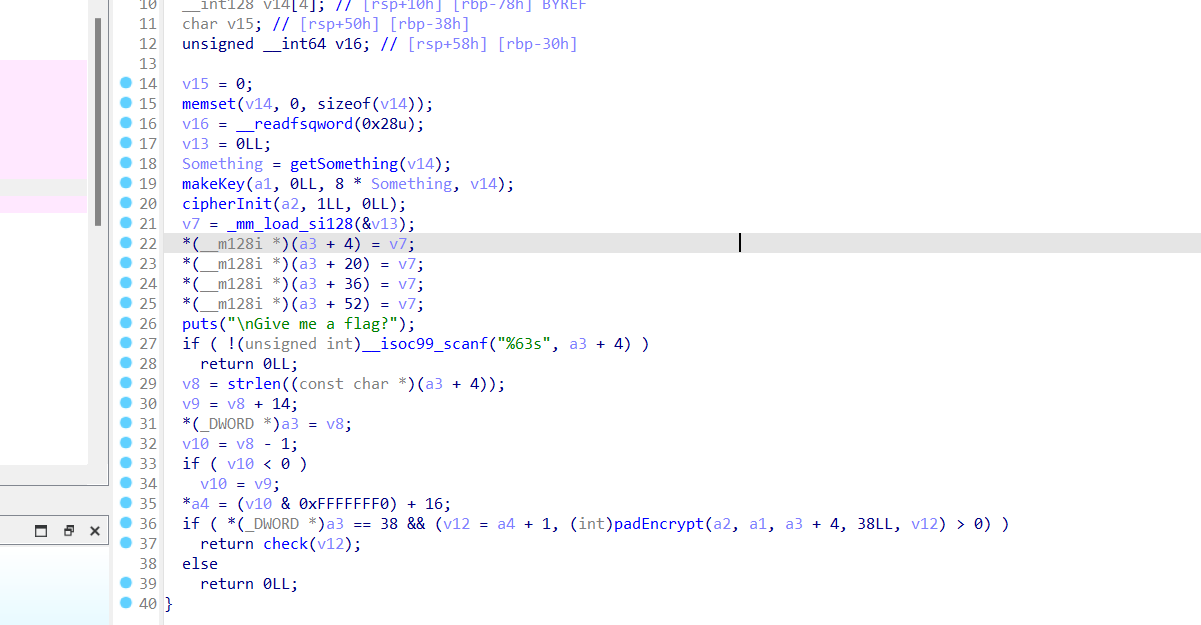
接着分析
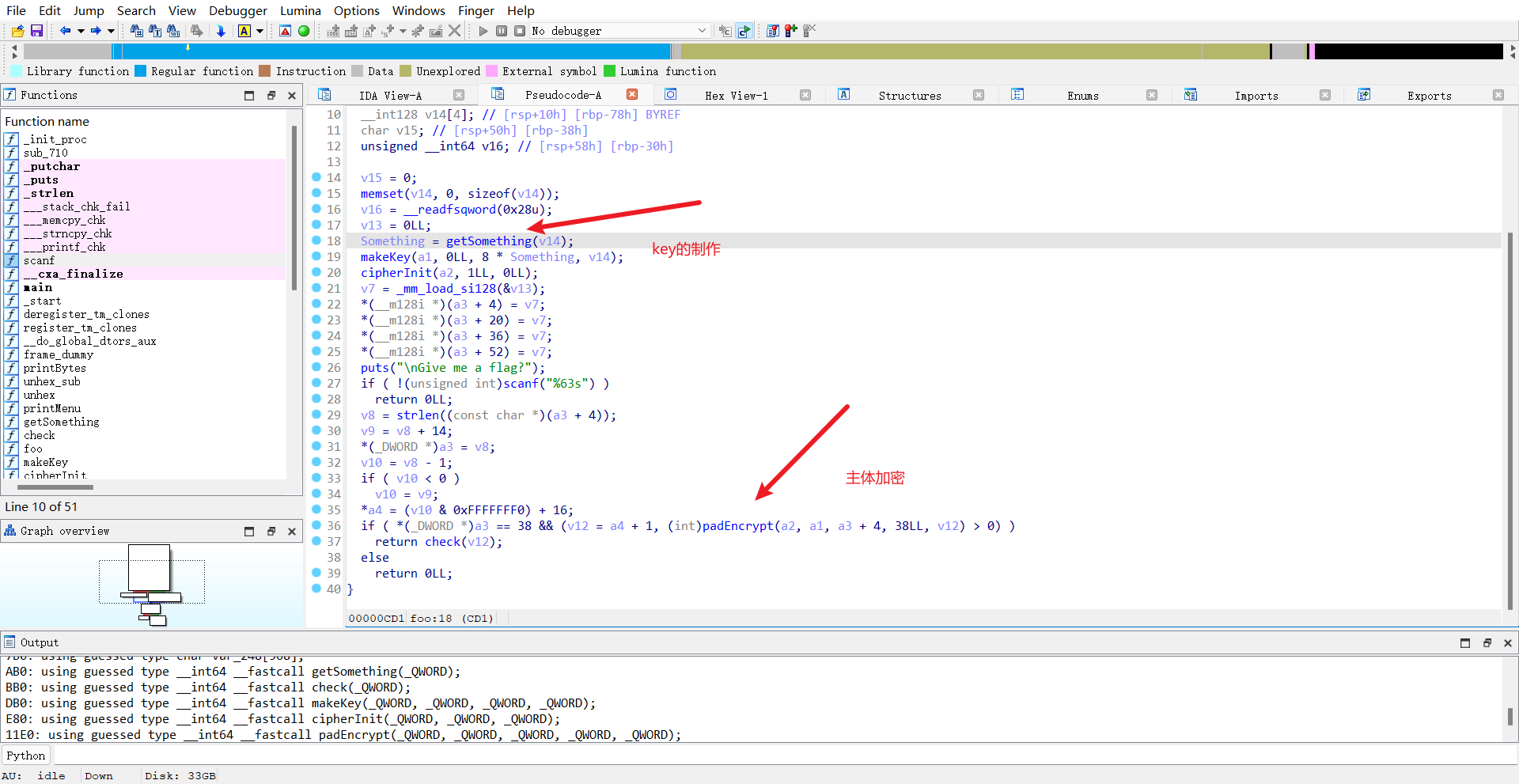
key貌似
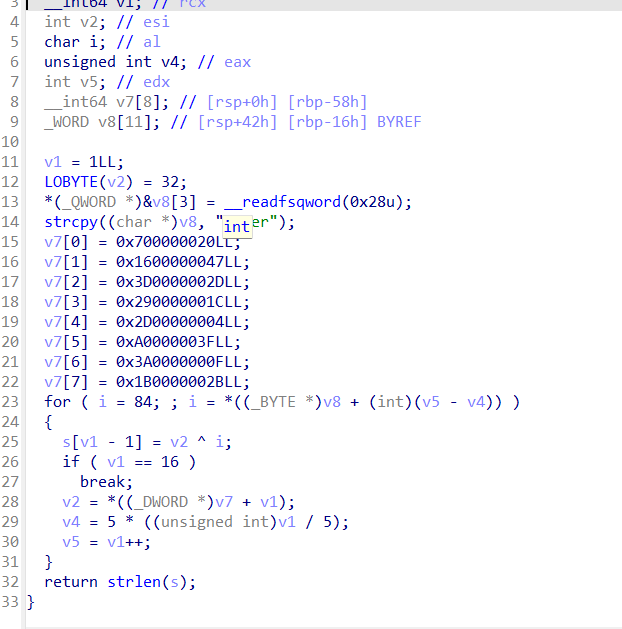
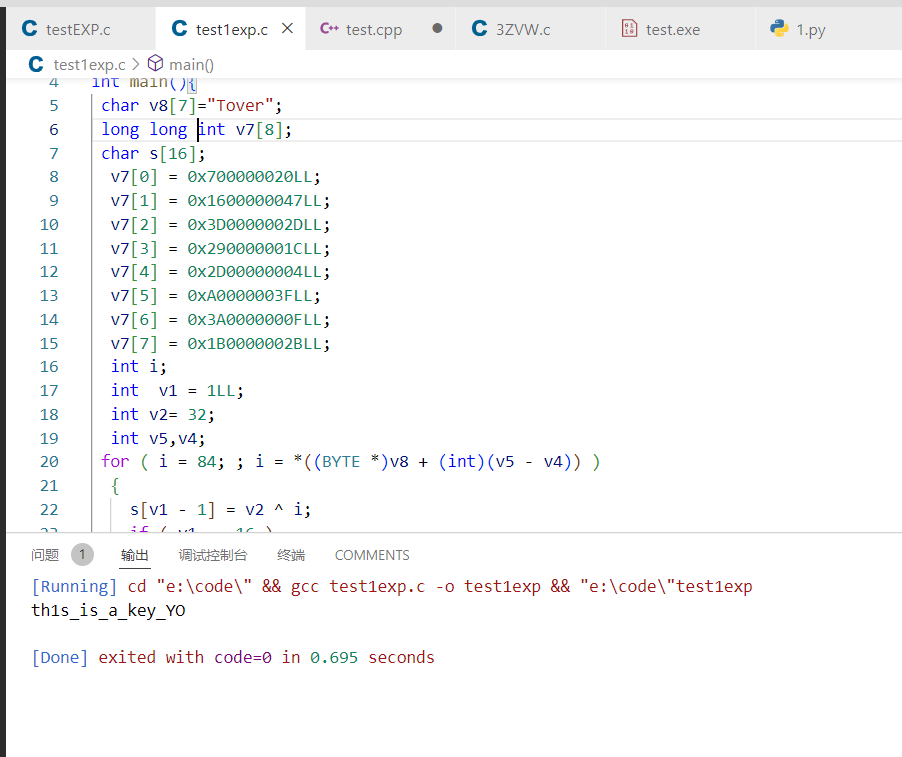
key拿到,动调应该也可以
#include<string.h>
#include<stdio.h>
#include<windows.h>
int main(){
char v8[7]="Tover";
long long int v7[8];
char s[16];
v7[0] = 0x700000020LL;
v7[1] = 0x1600000047LL;
v7[2] = 0x3D0000002DLL;
v7[3] = 0x290000001CLL;
v7[4] = 0x2D00000004LL;
v7[5] = 0xA0000003FLL;
v7[6] = 0x3A0000000FLL;
v7[7] = 0x1B0000002BLL;
int i;
int v1 = 1LL;
int v2= 32;
int v5,v4;
for ( i = 84; ; i = *((BYTE *)v8 + (int)(v5 - v4)) )
{
s[v1 - 1] = v2 ^ i;
if ( v1 == 16 )
break;
v2 = *((DWORD *)v7 + v1);
v4 = 5 * ((unsigned int)v1 / 5);
v5 = v1++;
}
puts(s);
}
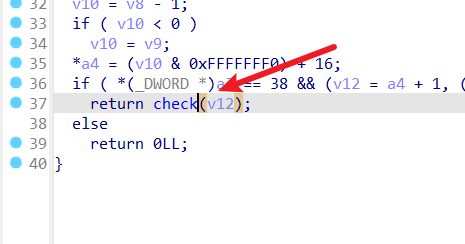
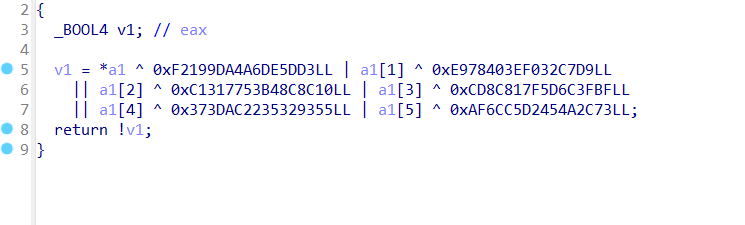
所以取后八位
直接逆向
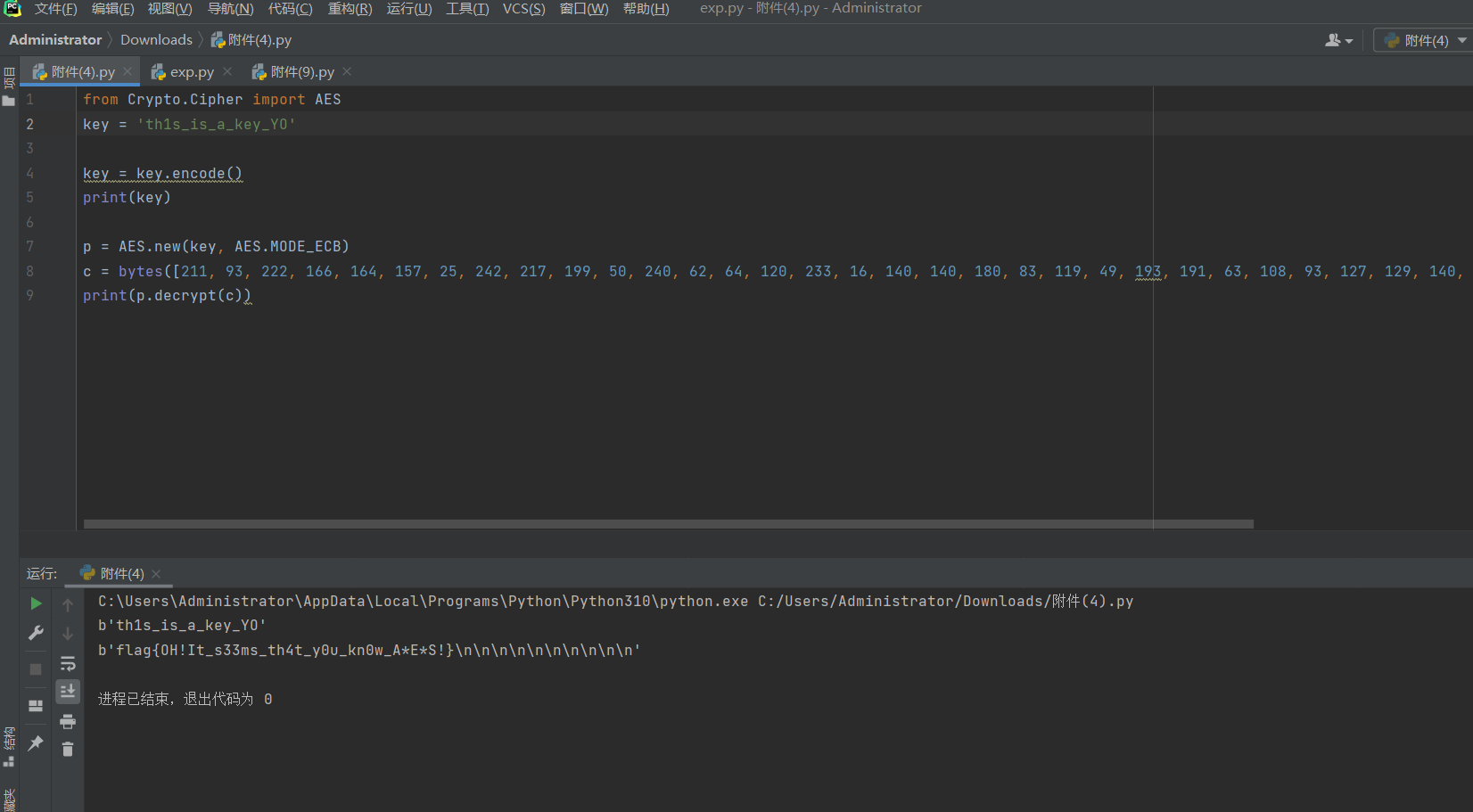
from Crypto.Cipher import AES
key = 'th1s_is_a_key_YO'
key = key.encode()
print(key)
p = AES.new(key, AES.MODE_ECB)
c = bytes([211, 93, 222, 166, 164, 157, 25, 242, 217, 199, 50, 240, 62, 64, 120, 233, 16, 140, 140, 180, 83, 119, 49, 193, 191, 63, 108, 93, 127, 129, 140, 205, 85, 147, 50, 53, 34, 172, 61, 55, 115, 44, 74, 69, 210, 197, 108, 175])
print(p.decrypt(c))
b'flag{OH!It_s33ms_th4t_y0u_kn0w_A*E*S!}
FMC_py
python文件打包
PS E:BaiduNetdiskDownloadctf工具箱逆向工程winlinuxpython打包逆向> python pyinstxtractor.py FMC_py.exe
[+] Processing FMC_py.exe
[+] Pyinstaller version: 2.1+
[+] Python version: 308
[+] Length of package: 7275694 bytes
[+] Found 70 files in CArchive
[+] Beginning extraction...please standby
[+] Possible entry point: pyiboot01_bootstrap.pyc
[+] Possible entry point: pyi_rth_pkgutil.pyc
[+] Possible entry point: pyi_rth_multiprocessing.pyc
[+] Possible entry point: pyi_rth_inspect.pyc
[+] Possible entry point: FMC.pyc
[+] Found 222 files in PYZ archive
[+] Successfully extracted pyinstaller archive: FMC_py.exe
前16位拿struct的进行还原
PS E:BaiduNetdiskDownloadctf工具箱逆向工程winlinuxpython打包逆向> uncompyle6.exe FMC.pyc
# uncompyle6 version 3.8.0
# Python bytecode 3.8.0 (3413)
# Decompiled from: Python 3.8.5 (tags/v3.8.5:580fbb0, Jul 20 2020, 15:57:54) [MSC v.1924 64 bit (AMD64)]
# Embedded file name: FMC.py
# Compiled at: 1995-09-28 00:18:56
# Size of source mod 2**32: 272 bytes
Instruction context:
L. 71 82 LOAD_FAST 'encrypted'
-> 84 RETURN_VALUE
class FMC(object):
MorseCode = {'!':'-.-.--', '"':'.-..-.', "'":'.----.', '(':'-.--.', ')':'-.--.-',
',':'--..--', '-':'-....-', '.':'.-.-.-', '0':'-----',
'1':'.----', '2':'..---', '3':'...--', '4':'....-',
'5':'.....', '6':'-....', '7':'--...', '8':'---..',
'9':'----.', ':':'---...', ';':'-.-.-.', '=':'-...-',
'?':'..--..', '@':'.--.-.', 'A':'.-', 'B':'-...',
'C':'-.-.', 'D':'-..', 'E':'.', 'F':'..-.', 'G':'--.',
'H':'....', 'I':'..', 'J':'.---', 'K':'-.-', 'L':'.-..',
'M':'--', 'N':'-.', 'O':'---', 'P':'.--.', 'Q':'--.-',
'R':'.-.', 'S':'...', 'T':'-', 'U':'..-', 'V':'...-',
'W':'.--', 'X':'-..-', 'Y':'-.--', 'Z':'--..'}
CipherSequence = '.....-..x.-..--.-x.x..x-.xx-..-.--.x--.-----x-x.-x--xxx..x.-x.xx-.x--x-xxx.xx-'
def toMorse(self, src: str) -> str:
result = ''
preced_by_letter = False
preced_by_space = False
for letter in src.upper():
if letter in self.MorseCode:
if preced_by_letter:
result += 'x'
else:
if preced_by_space:
result += 'xx'
result += self.MorseCode[letter]
preced_by_letter = True
preced_by_space = False
else:
if letter == ' ':
preced_by_space = True
preced_by_letter = False
if len(result) != 0:
result += 'xx'
return result
def createKey(self, keyphrase: str='') -> str:
upper_letters = 'ABCDEFGHIJKLMNOPQRSTUVWXYZ'
result = ''
for letter in keyphrase.upper():
if letter in upper_letters and letter not in result:
result += letter
for letter in upper_letters:
if letter not in result:
result += letter
assert len(result) == 26
return result
def morseToKey(self, mcmsg: str, key: str) -> str:
assert len(key) == 26
if len(mcmsg) >= 3:
care_about = mcmsg[0:3]
for index in range(len(self.CipherSequence) // 3):
if care_about == self.CipherSequence[index * 3:index * 3 + 3]:
return key[index]
return ''
def FMCEncrypt(self = None, src = None, keyphrase = None):
mcmsg = self.toMorse(src)
key = self.createKey(keyphrase)
encrypted = ''
counter = 0
val = self.morseToKey(mcmsg[counter * 3:], key)
counter += 1
if val != '':
encrypted += val
continue
return encrypted
if __name__ == '__main__':
flag = input('Give me a sentence?n')
key = 'ToverCrackRSA'
f = FMC()
dst = f.FMCEncrypt(flag, key)
if dst == 'BKTAOJOJRJTALTKTCBVTVHFBKTCTCTVRITVBOUVDKGARLTCHVGVTIHFHITIOITCBUFOITC':
print('Congratulations! Here is your flag: flag{' + flag.lower() + '}')
else:
print('Think more?')
?,我直接懵逼。这直接就字节码了?还分析错误。拿个网站反编译试试
class FMC(object):
MorseCode = {
'!': '-.-.--',
'"': '.-..-.',
"'": '.----.',
'(': '-.--.',
')': '-.--.-',
',': '--..--',
'-': '-....-',
'.': '.-.-.-',
'0': '-----',
'1': '.----',
'2': '..---',
'3': '...--',
'4': '....-',
'5': '.....',
'6': '-....',
'7': '--...',
'8': '---..',
'9': '----.',
':': '---...',
';': '-.-.-.',
'=': '-...-',
'?': '..--..',
'@': '.--.-.',
'A': '.-',
'B': '-...',
'C': '-.-.',
'D': '-..',
'E': '.',
'F': '..-.',
'G': '--.',
'H': '....',
'I': '..',
'J': '.---',
'K': '-.-',
'L': '.-..',
'M': '--',
'N': '-.',
'O': '---',
'P': '.--.',
'Q': '--.-',
'R': '.-.',
'S': '...',
'T': '-',
'U': '..-',
'V': '...-',
'W': '.--',
'X': '-..-',
'Y': '-.--',
'Z': '--..' }
CipherSequence = '.....-..x.-..--.-x.x..x-.xx-..-.--.x--.-----x-x.-x--xxx..x.-x.xx-.x--x-xxx.xx-'
def toMorse(self = None, src = None):
result = ''
preced_by_letter = False
preced_by_space = False
for letter in src.upper():
result += 'x'
if preced_by_space:
result += 'xx'
result += self.MorseCode[letter]
preced_by_letter = True
preced_by_space = False
continue
if letter == ' ':
preced_by_space = True
preced_by_letter = False
continue
if len(result) != 0:
result += 'xx'
return result
def createKey(self = None, keyphrase = None):
upper_letters = 'ABCDEFGHIJKLMNOPQRSTUVWXYZ'
result = ''
if not len(result) == 26:
raise AssertionError
def morseToKey(self = None, mcmsg = None, key = None):
if not len(key) == 26:
raise AssertionError
if None(mcmsg) >= 3:
care_about = mcmsg[0:3]
return ''
def FMCEncrypt(self = None, src = None, keyphrase = None):
mcmsg = self.toMorse(src)
key = self.createKey(keyphrase)
encrypted = ''
counter = 0
val = self.morseToKey(mcmsg[counter * 3:], key)
counter += 1
if val != '':
encrypted += val
continue
return encrypted
if __name__ == '__main__':
flag = input('Give me a sentence?n')
key = 'ToverCrackRSA'
f = FMC()
dst = f.FMCEncrypt(flag, key)
if dst == 'BKTAOJOJRJTALTKTCBVTVHFBKTCTCTVRITVBOUVDKGARLTCHVGVTIHFHITIOITCBUFOITC':
print('Congratulations! Here is your flag: flag{' + flag.lower() + '}')
else:
print('Think more?')
这回好了点,直接进行分析。仔细看也有问题
强行分析不了,应该是我电脑环境的问题,呜呜呜,这次放了。
Reverse-Fighting
寄了,不会分析
心累今天就这样吧,看了看后面的题好复杂TOC
最后
以上就是俊逸溪流最近收集整理的关于HSCTF2021 rebaigeiRSA2^11baigeiXorAstarEstarSFMC_pyReverse-Fighting的全部内容,更多相关HSCTF2021内容请搜索靠谱客的其他文章。
本图文内容来源于网友提供,作为学习参考使用,或来自网络收集整理,版权属于原作者所有。








发表评论 取消回复