写下这篇文章的目的是为了方便理解 Towards Scaling Blockchain Systems via Sharding这篇文章
针对几种failure model
Crash failure
Fail-Stop failure
Omission failure
Arbitrary failure: 文章主要是针对这种模型,也就是拜占庭模型
Abstract
作者在摘要中提出传统拜占庭容错共识算法受制于1/3的容错能力,In this paper, we investigate how minimal trusted abstractions can push through these hard limits in practical ways. We propose Attested Append-Only Memory(A2M), a trusted system facility that is small, easy to implement and easy to verify formally
A2M provides the programming abstraction of a trusted log, which leads to protocol designs immune to equivocation
这里的equivocation指的是验证人发出两个互相冲突的消息,也就是所谓的拜占庭节点。
本文提出使用A2M改进了拜占庭副本复制状态机,生成了基于PBFT的A2M协议,Safety: linearizable。 Liveness: 1/2
1 Introduction
介绍了目前分布式系统越来越关注拜占庭问题,而不是简单的fail-stop failure等。
介绍了目前分布式共识算法要保证liveness和safety这两项指标,目前节点的safety保证是满足linearizability基础上,而liveness表示的是最终可以正确处理客户端请求,即所有节点产生一个一致性结果。根据一致性的强弱可以分为:Sequential Consistency Linearizable Consistency Causal Consistency PRAM Consistency这三种模型的一致性从强到弱排列,有些算法提升了容错能力,但是采用了低于Linearizable Consistency的模型
作者提出本文的目标,提升系统容错能力。通过的手段是Our focus here is on small-footprint trusted primitives that have simple interfaces, are broadly applicable, and can be implemented easily and cost effectively.作者提出基于A2M这个trusted log abstraction进行这项工作,其目的主要是限制equivocation的发生。
第二部分介绍了trusted abstraction;第三部分详细介绍了A2M。 Next, we delve deeper into our second contribution: specific system designs for replicated state machines and shared storage that use A2M to improve their fault tolerance, in the context of agreement-based replicated state machines (Section 4) and other centralized and distributed protocols (Section 5).
- A2M-PBFT-E :将容错能力从1/3提升到2/3。
- A2M-PBFT-EA:将容错能力提升到1/2,导致其只需两倍(2-fold replication)容错复制即可(传统的是三重(3-fold replication)容错复制(PBFT的pre-prepare、prepare、commit三个阶段的副本复制过程))(这里不知道自己理解的正确吗,欢迎指正交流)
- A2M-Storage:is an A2M-enabled single-server storage service similar to SUNDR (reference:J. Li, M. Krohn, D. Mazières, and D. Shasha. Secure untrusted data repository (SUNDR). In Proc. of OSDI, 2004.)
2 Motivation
讲了一些基础性的内容,方便对后面内容的理解。
讲了Equivocation中的两种攻击模型:Forking Attack(图1)Consistency-violation(图2)
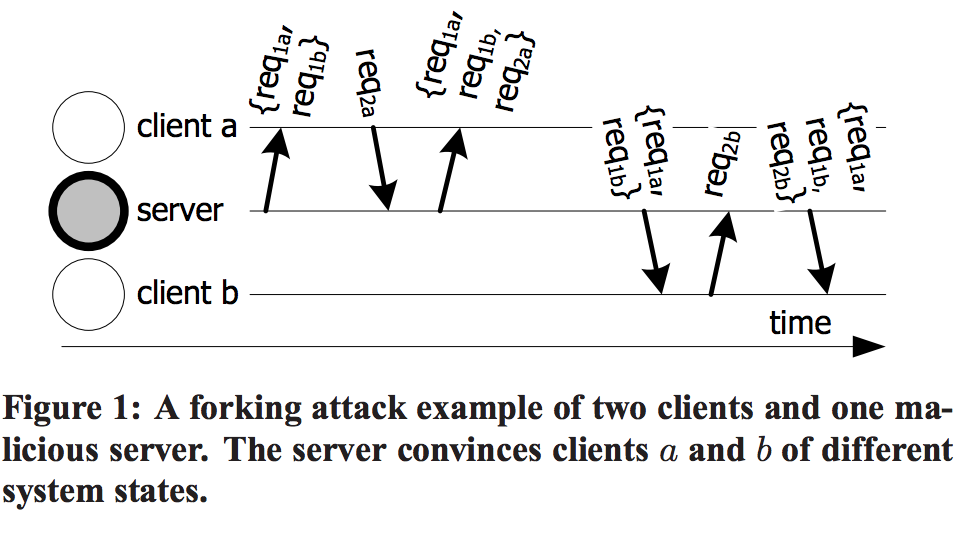
A faulty server can mount a forking attack [26] by concealing
operations, which causes the system’s state to diverge into multiple possibilities for different clients解释这个拜占庭行为,因为server是个拜占庭节点,其受到req2a之后将其删除,继续将删除req2a之后的消息转发给client b,这就是所谓的forking attack,啊也就是多副本攻击。这一种模型文章也给出了Servers Equivocating to Client,顾名思义,理解起来也十分容易。
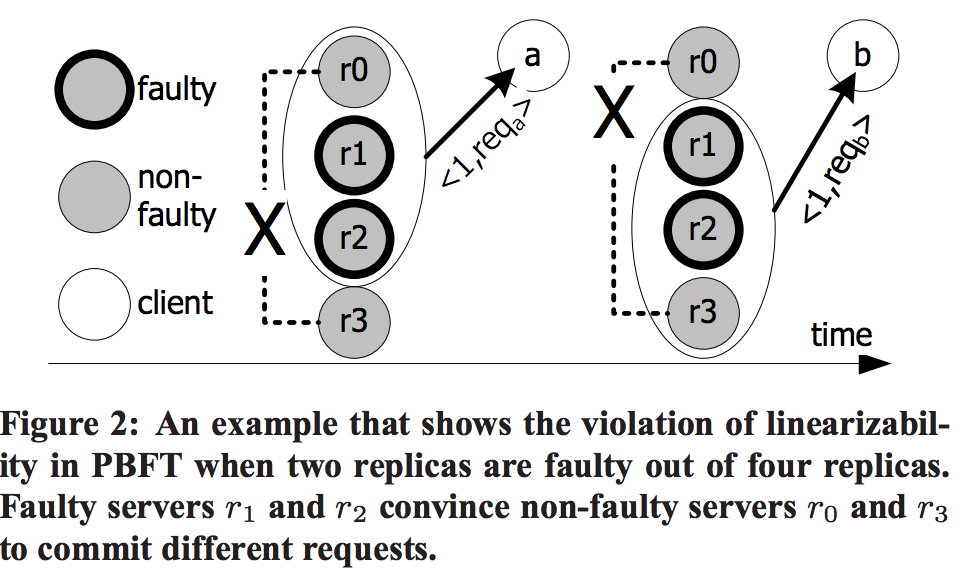
To illustrate, consider N = 4; replicas r1 and r2 are faulty, and
non-faulty replicas r0 and r3 cannot temporarily communicate with
each other (Figure 2).
针对linearizability的PBFT为例,是不能容忍超过(N-1)/3是拜占庭节点的情况。
3 Attested Append-Only Memory(A2M)
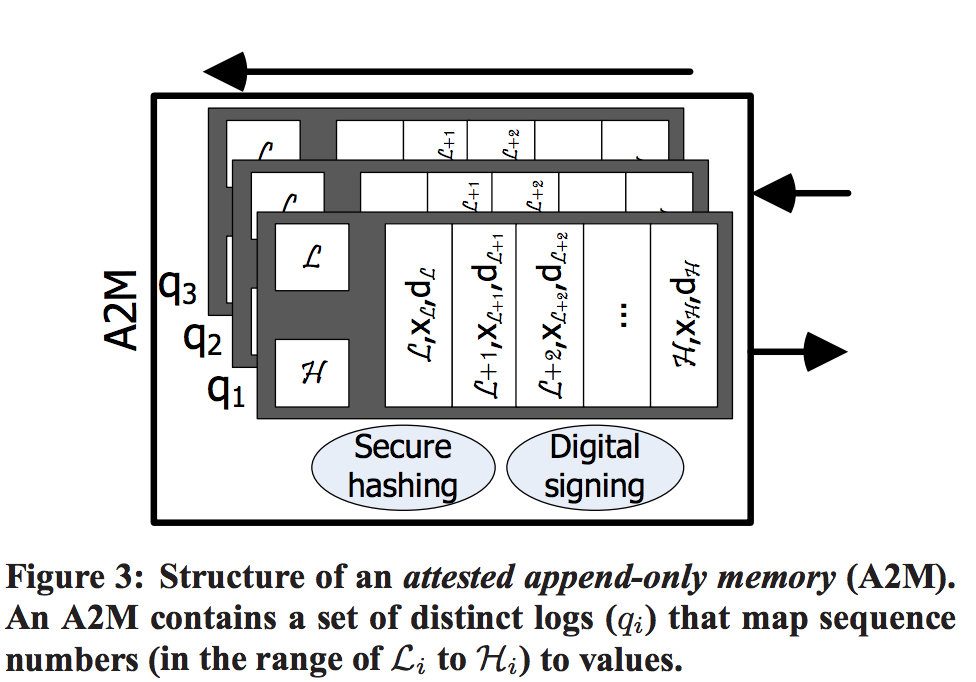
A2M的原理是Here we describe an attested append-only memory (A2M), a simple attestation-based abstraction that, when trusted, can remove the
ability of adversarial replicas to equivocate without detection.
A2M的目的是an A2M equips a host with a set of trusted, undeniable, ordered logs (illustrated in Figure 3).
介绍了几个method:append,lookup,end,truncate,advance
An A2M log offers methods to append values, to lookup values within the log or to obtain the end of the log, as well as to truncate and to advance the log suffix stored in memory. There are no methods to replace values that have already been assigned.
append过程描述: append(q,x) 表示将value x添加到q为唯一标识的log序列中,同时将highest assigned sequence number H自增1,computes the cumulative digest dH = h(H || x || dH−1), where d0 = 0 这里应该表示的是qi-1结束(如Figure2),进入qi,需要进行重新计算。
lookup过程描述:
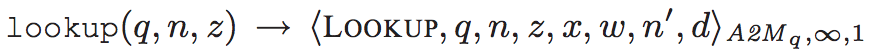
通过log唯一标识q,sequence number n以及为了freshness(标识当前查找数据的状态,分为UNASSIGNED,FORGOTTEN ,SKIPPED ‘and’ ASSIGNED四种状态)的z进行查找,返回一个LOOKUP认证。根据w的四种状态阐述四种可能的LOOKUP认证结果:
- w=UNASSIGNED:未分配状态,sequence number n没有被分配(即n>H(the range of L to H)),令n’=H
- w=FORGOTTEN:n<L,表明已经完成了分配,令n’=L
- w=SKIPPED:在这种状态下,通过advance方法跳过了n位置的插槽(slot),意思应该是 本来可以在某个位置插入,有一个对应的slot,但是通过advance方法将其跳过了
- w=ASSIGNED:在这种状态下,通过append或者advance方法,将值填到对应位置,即slot,x and d are the assigned log value and digest when
w is ASSIGNED) and 0 otherwise.
end过程描述: end(q,z)类似于lookup过程,但是与lookup过程不同的是,end返回的是当前q下的最后一条log,即position为H的log。
truncate过程描述: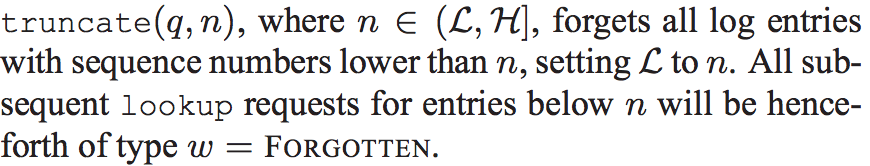
这个过程表示q定位到position,然后对这个片内的log进行处理,将所有slot低于n(也就是L)的sequence number设置为FORGOTTEN状态。
advance过程描述
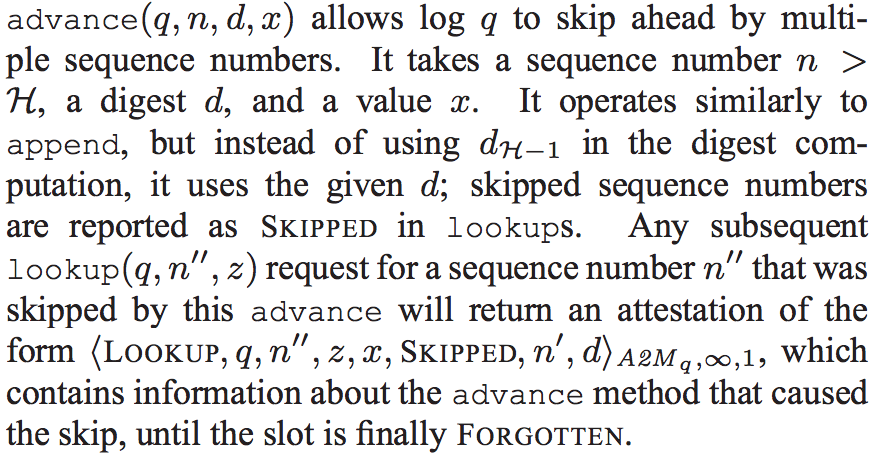
这个过程表示log q可以跳过多个sequence number,然后通过指定到某个sequence number的lookup来实现跳转,具体执行过程与lookup一致。在执行过程结束时w=FORGOTTEN,表示已经完成了分配。
As far as a verifier is concerned, the A2M authentication key and log identifier are part of the untrusted component’s identity不可信任组件、验证者、授权密钥和日志标识符的关系。Therefore, a particular A2M-enabled component is allowed to use only its associated A2M
以下谈一下对整个过程的理解
append将不信任组件的内容添加到指定position的log的slot中。lookup根据返回的LOOKUP对不可信任组件进行检查,最后在通过end检查是否被成功的附件。而advance针对的是某一部分缺少日志的情况。
Our contribution is a novel division of functionality between trusted and untrusted components, not a specific implementation of it这里提出了作者的贡献。
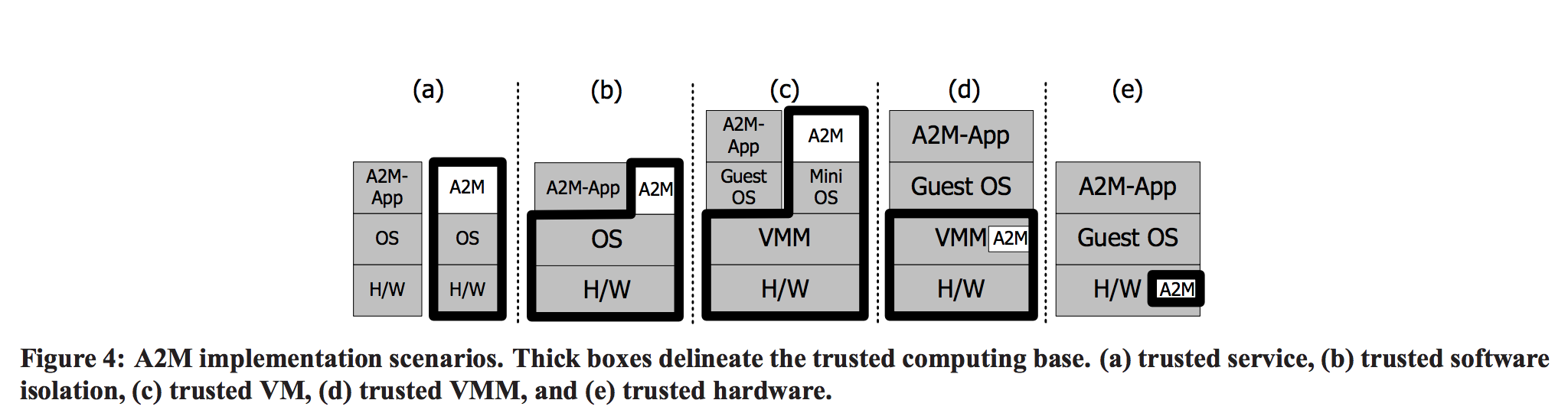
几种可信组件(trusted component)的展示。这一部分对应《Towards Scaling Blockchain Systems via Sharding》中的TEE硬件环境
A2M STATE MACHINE REPLICATION PROTOCOLS
采用A2M将PBFT中 (N-1)/3的safety和 2(N-1)/3的liveness保证提升到 (N-1)/2的liveness和safety。
然后文章描述了PBFT的整个过程,包括request、pre-prepare、prepare、commit、reply过程以及checkpoint和view-change过程。
下面介绍A2M-PBFT-E
*In this section, we describe A2M-PBFT-E, a simple extension of PBFT that uses A2M logs to protect the execution portion of PBFT (hence the “E” suffix of the acronym); that is, it ensures that replicas cannot equivocate about their locally computed results for a particular requested client operation when replying to that or any other client (Figure 5(b)). As before, we consider a population R of N replicas.*介绍了A2M-PBFT-E的原理,两种协议的主要不同是:在client interaction和checkpoint两方面的不同,it packages the regular PBFT reply message and the attestation into a single message, which it sends back to the client.(未完待续)
最后
以上就是文静香水最近收集整理的关于Attested Append-Only Memory: Making Adversaries Stick to their WordAbstract1 Introduction2 Motivation3 Attested Append-Only Memory(A2M)A2M STATE MACHINE REPLICATION PROTOCOLS的全部内容,更多相关Attested内容请搜索靠谱客的其他文章。








发表评论 取消回复