一.拓扑图
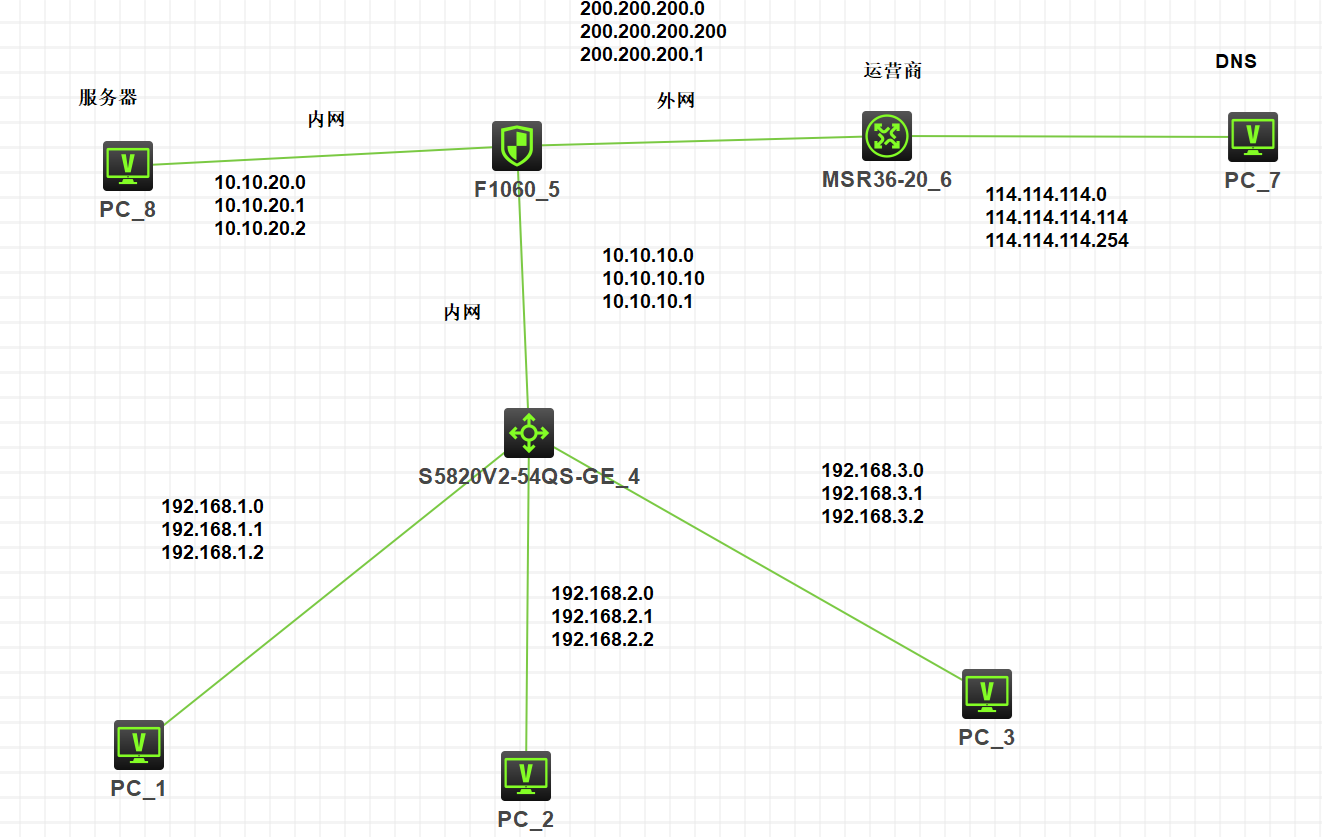
要求pc1能够访问到DNS服务器,能够访问到内网服务器
,实现地址转换,内网访问到外网
二.配置
[L1]dis cu
version 7.1.075, Alpha 7571
sysname L1
lldp global enable
vlan 1
Vlan 2
vlan 10
vlan 20
vlan 30
stp global enable
interface NULL0
interface Vlan-interface2
ip address 10.10.10.10 255.255.255.0
interface Vlan-interface10
ip address 192.168.1.1 255.255.255.0
interface Vlan-interface20
ip address 192.168.2.1 255.255.255.0
interface Vlan-interface30
ip address 192.168.3.1 255.255.255.0
interface GigabitEthernet1/0/1
port link-mode bridge
port access vlan 10
combo enable fiber
interface GigabitEthernet1/0/2
port link-mode bridge
port access vlan 20
combo enable fiber
interface GigabitEthernet1/0/3
port link-mode bridge
port access vlan 30
combo enable fiber
interface GigabitEthernet1/0/4
port link-mode bridge
port access vlan 2
combo enable fiber
[H3C]dis cu
version 7.1.064, Alpha 7164
sysname H3C
context Admin id 1
telnet server enable
irf mac-address persistent timer
irf auto-update enable
undo irf link-delay
irf member 1 priority 1
nat address-group 1
address 200.200.200.1 200.200.200.1
nat address-group 2
address 114.114.114.114 114.114.114.114
address 200.200.200.200 200.200.200.200
nat address-group 3
address 10.10.20.1 10.10.20.1
nat address-group 4
address 10.10.20.2 10.10.20.2
nat static inbound 200.200.200.1 10.10.10.1
nat static outbound 10.10.10.1 200.200.200.1
xbar load-single
password-recovery enable
lpu-type f-series
vlan 1
interface NULL0
interface GigabitEthernet1/0/0
port link-mode route
combo enable copper
ip address 10.10.10.1 255.255.255.0
interface GigabitEthernet1/0/1
port link-mode route
combo enable copper
ip address 10.10.20.1 255.255.255.0
nat inbound 2000 address-group 4 no-pat reversible
nat outbound 2000 address-group 3
interface GigabitEthernet1/0/2
port link-mode route
combo enable copper
ip address 200.200.200.1 255.255.255.0
nat inbound 2000 address-group 2 no-pat reversible
nat outbound address-group 1
nat static enable
security-zone name Local
security-zone name Trust
import interface GigabitEthernet1/0/0
security-zone name DMZ
import interface GigabitEthernet1/0/1
security-zone name Untrust
import interface GigabitEthernet1/0/2
security-zone name Management
zone-pair security source DMZ destination Local
packet-filter 2000
zone-pair security source DMZ destination Trust
packet-filter 2000
zone-pair security source Local destination DMZ
packet-filter 2000
zone-pair security source Local destination Trust
packet-filter 2000
zone-pair security source Trust destination DMZ
packet-filter 2000
zone-pair security source Trust destination Local
packet-filter 2000
zone-pair security source Trust destination Untrust
packet-filter 2000
zone-pair security source Untrust destination Local
packet-filter 2000
ip route-static 10.10.20.0 24 10.10.20.2
ip route-static 10.10.20.2 32 GigabitEthernet1/0/1 10.10.20.1
ip route-static 114.114.114.0 24 200.200.200.200
ip route-static 192.168.0.0 22 10.10.10.10
ip route-static 200.200.200.1 32 GigabitEthernet1/0/2 200.200.200.200
undo info-center enable
acl basic 2000
rule 0 permit
rule 5 permit source 10.10.10.0 0.0.0.255
service-type telnet terminal http
authorization-attribute user-role level-3
authorization-attribute user-role network-admin
authorization-attribute user-role network-operator
ip http enable
ip https enable
Return
要实现以上配置,要有清晰的思路
首先所有的设备按照图给分配ip地址,然后三层交换机要配vlan虚接口 放地址,再配置缺省路由
接着就是要对防火墙进行配置
在防火墙中,先对安全域的划分,一般内网都是trust,外网是untrust,服务器是DMZ区域
接着就是对安全策略的配置
然后进行nat配置,再进行静态路由配置
三。结果
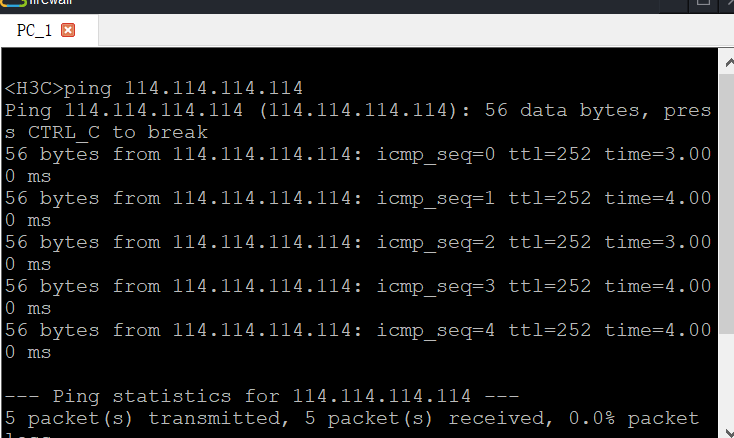
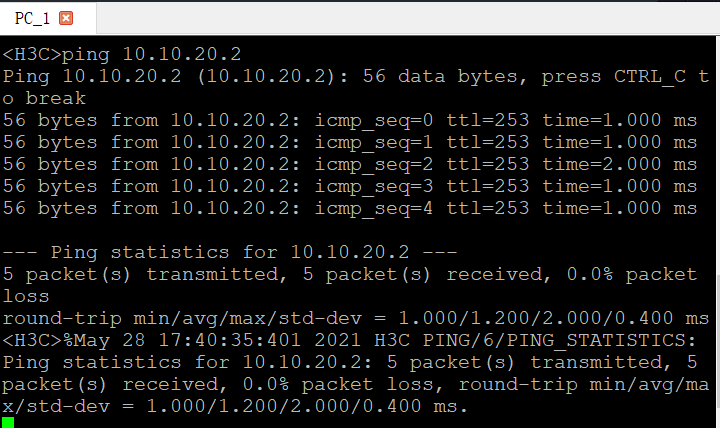
最后
以上就是愤怒纸飞机最近收集整理的关于防火墙综合配置的全部内容,更多相关防火墙综合配置内容请搜索靠谱客的其他文章。








发表评论 取消回复