微软产品团队和安全团队正在积极的调查本次事件,以下是截止到目前的最新信息:
- 在微软产品方面,目前尚未发现有产品受到本次漏洞的影响,包括(Azure Application Gateway, Azure Front Door, Azure WAF, Azure App Service (Windows and Linux), Azure App Service for Containers, Azure Functions),我们仍在持续调查中,如果有更新的信息会第一时间进行通知。
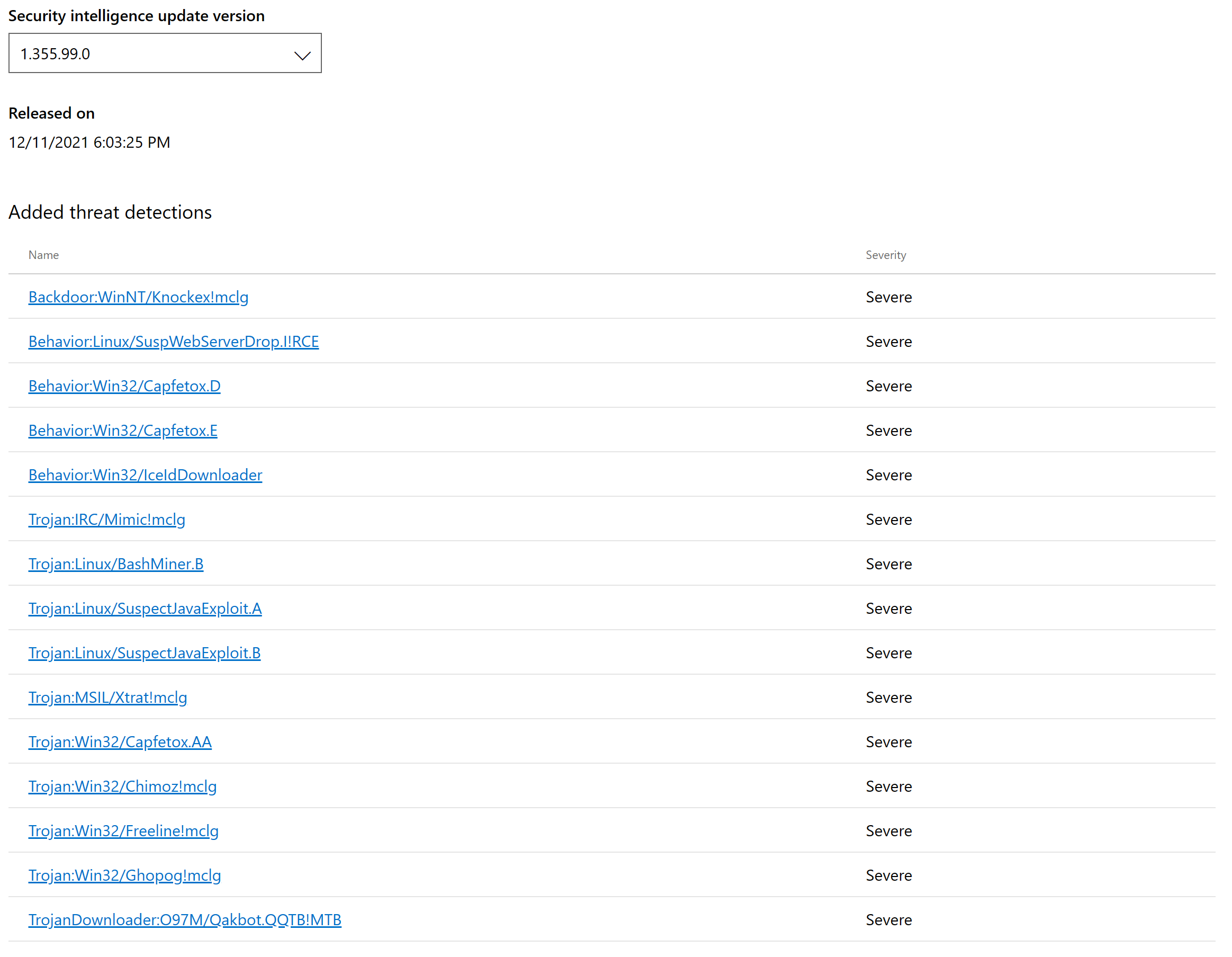
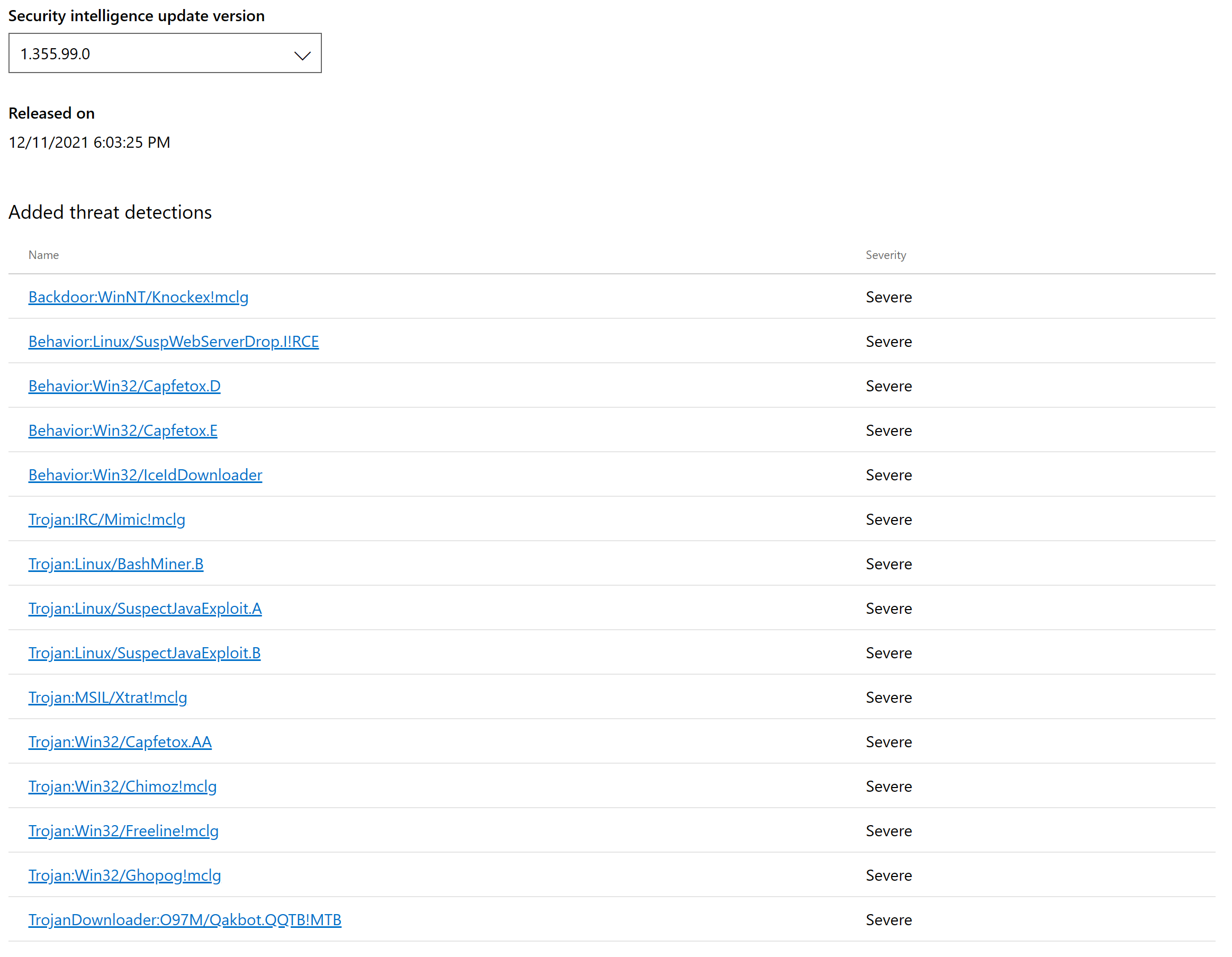
- 针对操作系统及IaaS VM安全层面,我们于昨晚发布了安全情报更新版本1.355.99.0 ,以抑制相关的漏洞攻击和恶意软件攻击行为。所有Windows系统内置的Microsoft Defender 反病毒组件、Microsoft Defender for Endpoint(Windows和Linux系统),以及与MDE集成的Microsoft Defender for Cloud中的Defender for Server 组件,均可以通过默认的自动更新获得本次更新。我们也持续的分析和调查本次事件相关的攻击行为,因此也在持续的更新我们的安全情报,在我写这封邮件时,最新的版本已经是1.355.128.0。
- 在Azure网络安全方面,
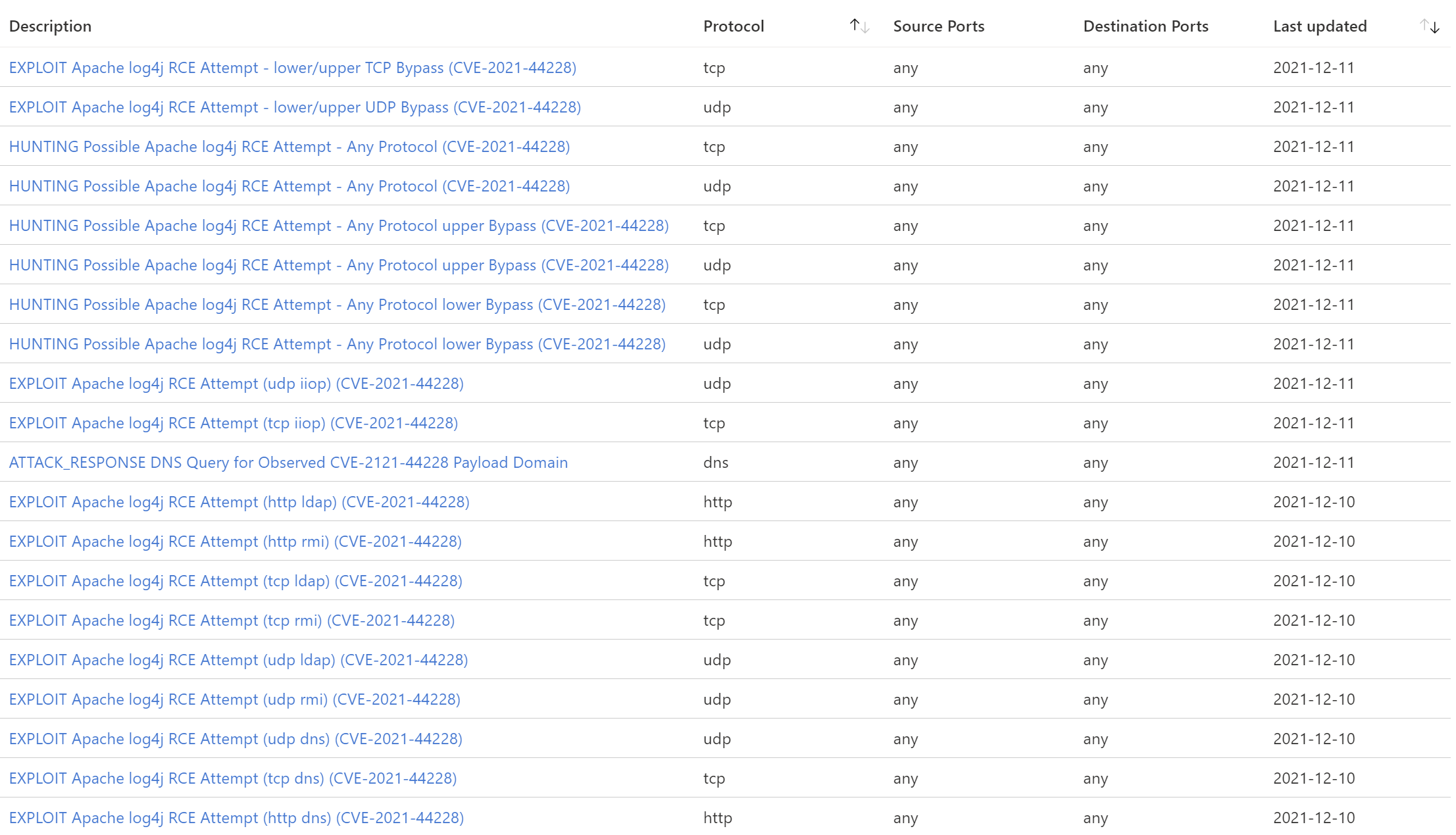
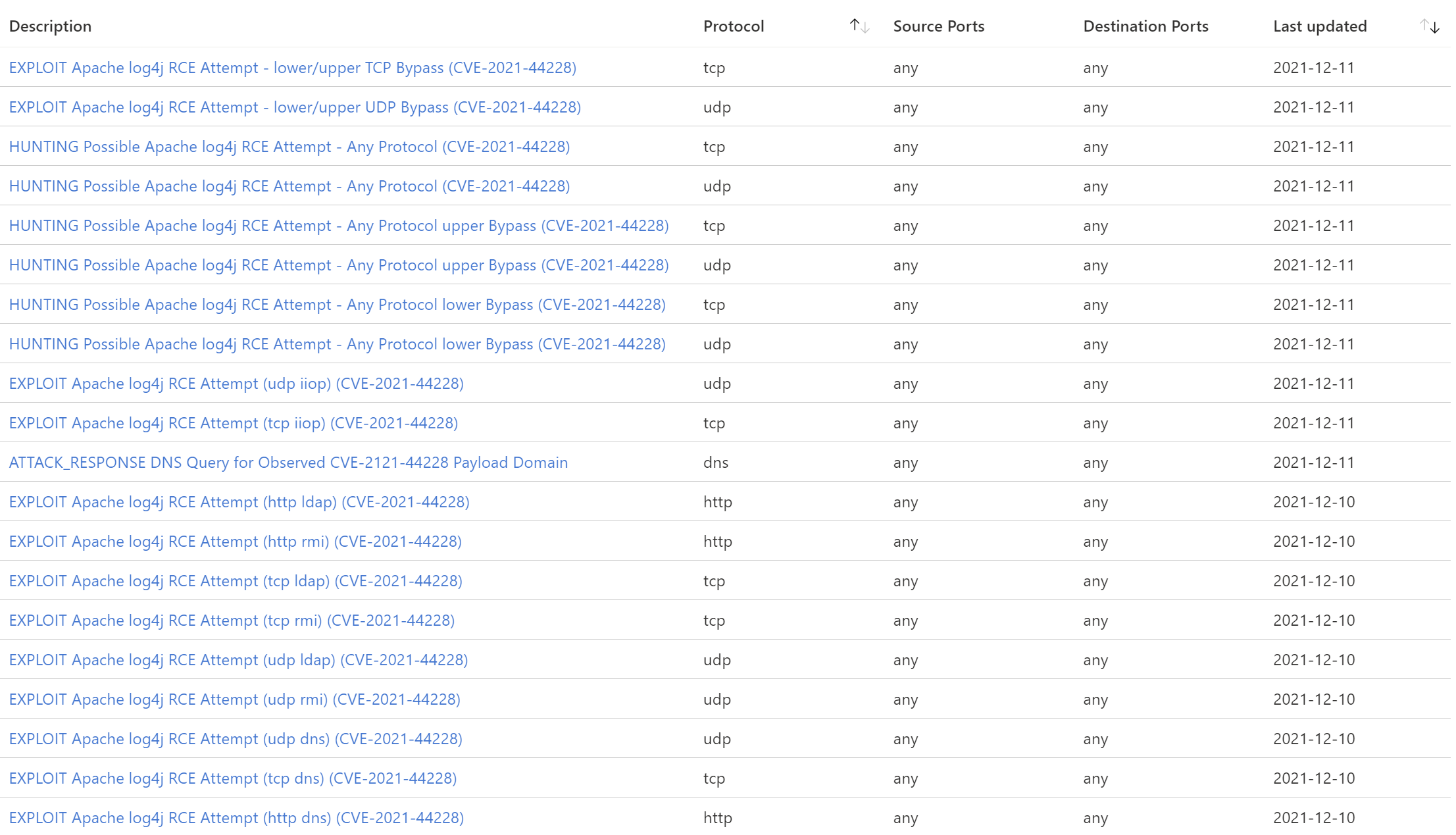
- 同样的,我们为 Azure Firewall Premium IDPS (Intrusion Detection and Prevention System) 功能发布了最新的安全情报更新,如下图所示,可以通过 Azure Firewall Premium IDPS 功能直接在网络层面拦截相关攻击行为,该功能为自动更新,无需额外操作。IDPS 策略模式建议设置为Alert and deny。
-
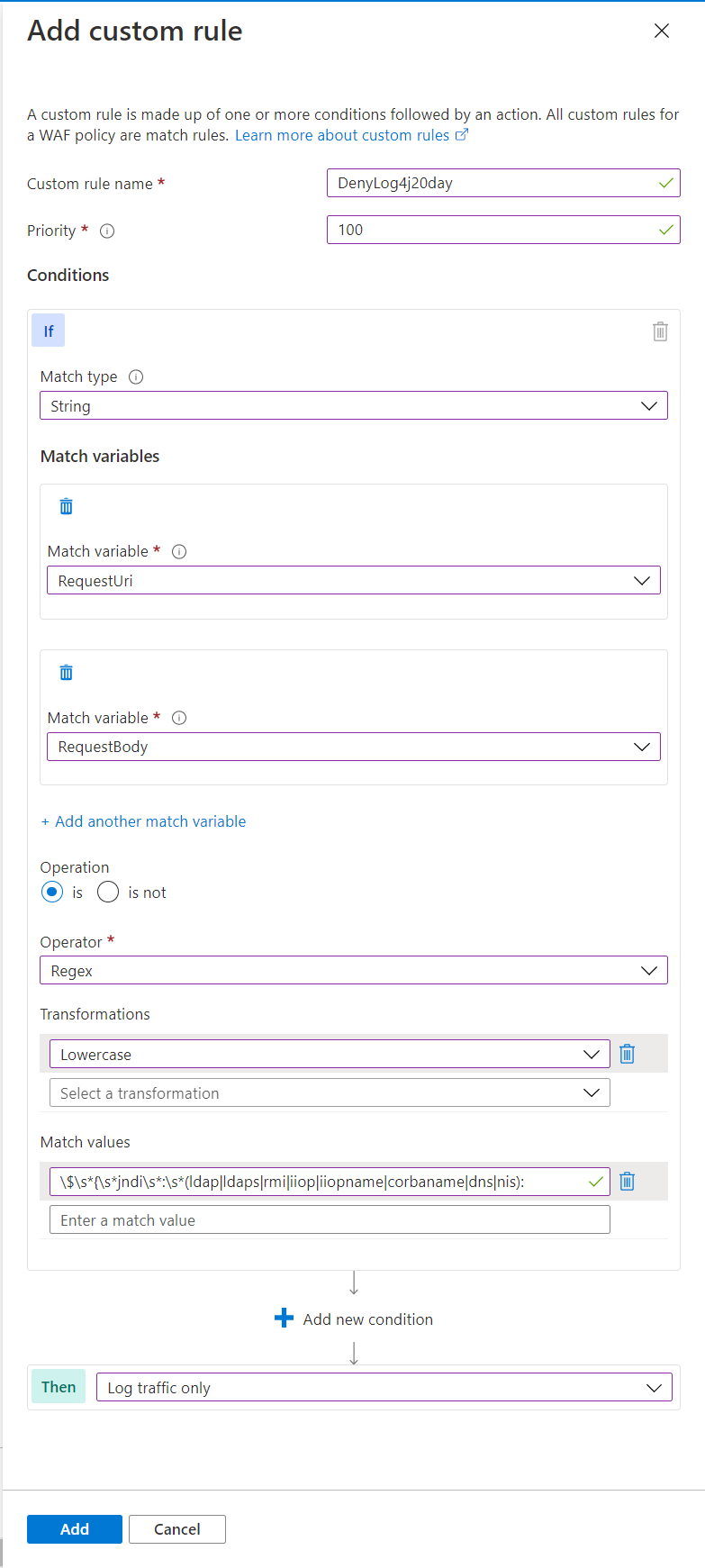
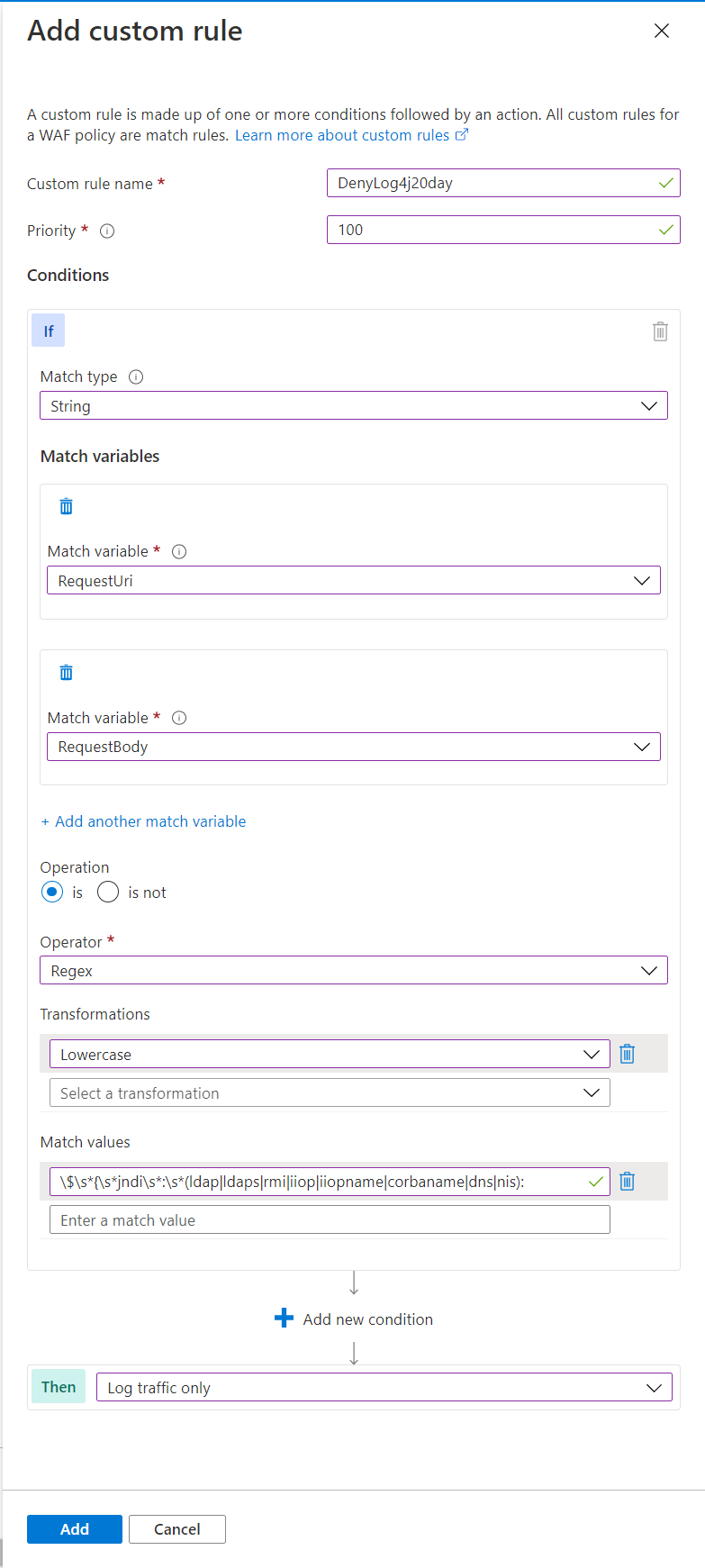
- 针对 Azure WAF,我们第一时间提供了快速抑制攻击行为的相关自定义检测和阻止规则,目前产品组正在评估和更新相关托管规则(Managed Rule Set)。
| • Custom rule name: DenyLog4j20day • Match Type: String • Match variable: RequestBody, RequestUri • Operation: Is • Operator: Regex • Transformations: Lowercase • Match Values: $s*{s*jndis*:s*(ldap|ldaps|rmi|iiop|iiopname|corbaname|dns|nis): • Then: Log traffic only – for test first |
|
- 在Azure安全监测与运营方面,
- 与其他恶意攻击行为一样,我们可以通过 Microsoft Defender for Cloud 来监测和警告相关恶意攻击行为,例如恶意的进程执行/文件下载/网络连接/C2连接等等。
因此后续建议包括:
- 请客户评估CVE-2021-44228 Log4j2 漏洞对自身所拥有的相关应用和系统的影响。更为详细的信息,可以参考:
CVE-2021-44228 Log4j2 漏洞
https://cve.mitre.org/cgi-bin/cvename.cgi?name=2021-44228
- 在操作系统和IaaS 方面,请客户确保在操作系统或者IaaS VM 层面,Microsoft Defender 反病毒组件或者Microsoft Defender for Endpoint 已启用自动更新;
- 在Azure网络安全方面,请客户部署并使用Azure Firewall Premium IDPS 功能,或在 Azure WAF 上部署相关检测或阻止策略(参考以上内容);
- 启用 Microsoft Defender for Cloud 的相关功能,以实现针对Azure环境和资源的安全监测与运营。
产品组相关公告可以参考:
Microsoft’s Response to CVE-2021-44228 Apache Log4j 2
https://msrc-blog.microsoft.com/2021/12/11/microsofts-response-to-cve-2021-44228-apache-log4j2/
Guidance for preventing, detecting, and hunting for CVE-2021-44228 Log4j 2 exploitation
https://www.microsoft.com/security/blog/2021/12/11/guidance-for-preventing-detecting-and-hunting-for-cve-2021-44228-log4j-2-exploitation/
English version:
Microsoft PG and Security team are actively engaged in this incident. Here is latest information for you:
- On Microsoft product security side, we are actively investigate on the effect of Log4j2 vulnerability to Microsoft product from 9 December, and no Microsoft product (Includes Azure Application Gateway, Azure Front Door, Azure WAF, Azure App Service (Windows and Linux), Azure App Service for Containers, Azure Functions) is affected so far, we are still in investigation due to complex product line in Microsoft and keep our customer updated.
- On OS and IaaS VM security side, We release security intelligence update version 1.355.99.0 on yesterday evening for Log4j2 related exploit and malicious activities, all built-in Microsoft Defender Anti-virus in Windows (and Server) OS, Microsoft Defender for Endpoint (For Windows and Linux OS), and Defender for Servers (For Windows and Linux OS) in Microsoft Defender for Cloud which integrated with MDE, will get this update if automatic update is enabled, and block Log4j2 vulnerability on OS level. After that release, we also continue to investigate related attack and release more security intelligence update – latest version is 1.355.128.0 when I writing this email.
- On Azure network security side,
- we also released security intelligence update for Azure Firewall premium IDPS (Intrusion Detection and Prevention System) feature. Here are the updates list, they are automatic updated and no other actions are need, just ensure IDPS mode is set to Alert or Alert and deny.
-
- For Azure WAF, we provided a custom rule for WAF to quick mitigate this vulnerability on WAF side. PG are also working for the Managed Rule Set.
| • Custom rule name: DenyLog4j20day • Match Type: String • Match variable: RequestBody, RequestUri • Operation: Is • Operator: Regex • Transformations: Lowercase • Match Values: $s*{s*jndis*:s*(ldap|ldaps|rmi|iiop|iiopname|corbaname|dns|nis): • Then: Log traffic only – for test first |
|
- On Azure security detection and operation side,
- Like other malicious activities, Microsoft Defender for Cloud also will help on detecting related attack behavious like malicious process execution/file download/network connection/C2 connection etc.
Follow-up actions:
- Ensure automatic update is enabled for Microsoft Defender Anti-virus and Microsoft Defender for Endpoint.
- Ensure Azure Firewall Premium IDPS is enabled and set mode to Alert or Alert and Deny, create custom rule on WAF for quick detection or mitigation.
- Enable Microsoft Defender for Cloud for security detection and operation on Azure environment and resources.
Here are some announcements from Microsoft, and we will keep it update in future:
Microsoft’s Response to CVE-2021-44228 Apache Log4j 2
https://msrc-blog.microsoft.com/2021/12/11/microsofts-response-to-cve-2021-44228-apache-log4j2/
Guidance for preventing, detecting, and hunting for CVE-2021-44228 Log4j 2 exploitation
https://www.microsoft.com/security/blog/2021/12/11/guidance-for-preventing-detecting-and-hunting-for-cve-2021-44228-log4j-2-exploitation/
最后
以上就是优雅狗最近收集整理的关于关于 CVE-2021-44228 Log4j2 漏洞的相关应对汇总说明(包含中英文客户公告)的全部内容,更多相关关于内容请搜索靠谱客的其他文章。








发表评论 取消回复