全局句柄表
_HANDLE_TABLE
0: kd> dt _HANDLE_TABLE
nt!_HANDLE_TABLE
+0x000 TableCode : Uint8B
+0x008 QuotaProcess : Ptr64 _EPROCESS
+0x010 UniqueProcessId : Ptr64 Void
+0x018 HandleLock : _EX_PUSH_LOCK
+0x020 HandleTableList : _LIST_ENTRY
+0x030 HandleContentionEvent : _EX_PUSH_LOCK
+0x038 DebugInfo : Ptr64 _HANDLE_TRACE_DEBUG_INFO
+0x040 ExtraInfoPages : Int4B
+0x044 Flags : Uint4B
+0x044 StrictFIFO : Pos 0, 1 Bit
+0x048 FirstFreeHandle : Uint4B
+0x050 LastFreeHandleEntry : Ptr64 _HANDLE_TABLE_ENTRY
+0x058 HandleCount : Uint4B
+0x05c NextHandleNeedingPool : Uint4B
+0x060 HandleCountHighWatermark : Uint4B
dt _HANDLE_TABLE_ENTRY
0: kd> dt _HANDLE_TABLE_ENTRY
nt!_HANDLE_TABLE_ENTRY
+0x000 Object : Ptr64 Void
+0x000 ObAttributes : Uint4B
+0x000 InfoTable : Ptr64 _HANDLE_TABLE_ENTRY_INFO
+0x000 Value : Uint8B
+0x008 GrantedAccess : Uint4B
+0x008 GrantedAccessIndex : Uint2B
+0x00a CreatorBackTraceIndex : Uint2B
+0x008 NextFreeTableEntry : Uint4B
_OBJECT_HEADER
0: kd> dt _OBJECT_HEADER
nt!_OBJECT_HEADER
+0x000 PointerCount : Int8B
+0x008 HandleCount : Int8B
+0x008 NextToFree : Ptr64 Void
+0x010 Lock : _EX_PUSH_LOCK
+0x018 TypeIndex : UChar
+0x019 TraceFlags : UChar
+0x01a InfoMask : UChar
+0x01b Flags : UChar
+0x020 ObjectCreateInfo : Ptr64 _OBJECT_CREATE_INFORMATION
+0x020 QuotaBlockCharged : Ptr64 Void
+0x028 SecurityDescriptor : Ptr64 Void
+0x030 Body : _QUAD
通过ObGetObjectType函数可以获取ObTypeIndexTable地址
ObTypeIndexTable
0: kd> dt _OBJECT_TYPE
nt!_OBJECT_TYPE
+0x000 TypeList : _LIST_ENTRY
+0x010 Name : _UNICODE_STRING
+0x020 DefaultObject : Ptr64 Void
+0x028 Index : UChar
+0x02c TotalNumberOfObjects : Uint4B
+0x030 TotalNumberOfHandles : Uint4B
+0x034 HighWaterNumberOfObjects : Uint4B
+0x038 HighWaterNumberOfHandles : Uint4B
+0x040 TypeInfo : _OBJECT_TYPE_INITIALIZER
+0x0b0 TypeLock : _EX_PUSH_LOCK
+0x0b8 Key : Uint4B
+0x0c0 CallbackList : _LIST_ENTRY
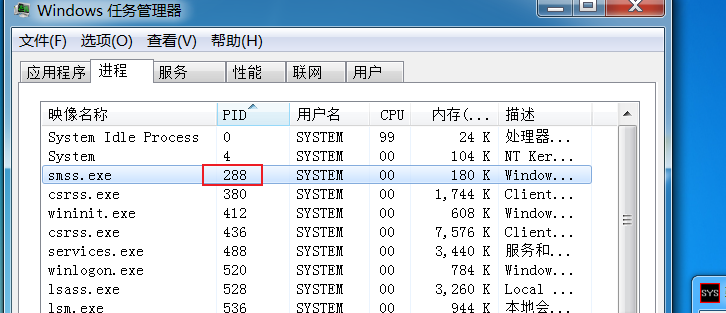
288 / 4 = 72 = 0x48 < 256(4K/16) 所以在第0张表的第0x48个位置
0: kd> dq PspCidTAble
fffff800`04070408 fffff8a0`00004880 00000000`00000000
fffff800`04070418 ffffffff`80000020 00000000`00000101
fffff800`04070428 ffffffff`80000298 ffffffff`80000024
fffff800`04070438 00000000`00000000 00000000`00000113
fffff800`04070448 00000000`00000000 00000000`00000000
fffff800`04070458 fffff800`03fcc7d0 00000000`00000000
fffff800`04070468 00000000`00000000 00000000`00000000
fffff800`04070478 00000000`00000000 00000000`00000008
0: kd> dt _HANDLE_TABLE fffff8a0`00004880
nt!_HANDLE_TABLE
+0x000 TableCode : 0xfffff8a0`01ce0001
+0x008 QuotaProcess : (null)
+0x010 UniqueProcessId : (null)
+0x018 HandleLock : _EX_PUSH_LOCK
+0x020 HandleTableList : _LIST_ENTRY [ 0xfffff8a0`000048a0 - 0xfffff8a0`000048a0 ]
+0x030 HandleContentionEvent : _EX_PUSH_LOCK
+0x038 DebugInfo : (null)
+0x040 ExtraInfoPages : 0n0
+0x044 Flags : 1
+0x044 StrictFIFO : 0y1
+0x048 FirstFreeHandle : 0xcd8
+0x050 LastFreeHandleEntry : 0xfffff8a0`03cb1ff0 _HANDLE_TABLE_ENTRY
+0x058 HandleCount : 0x273
+0x05c NextHandleNeedingPool : 0x1000
+0x060 HandleCountHighWatermark : 0x36e
//最后2位是属性 直接置0才能找地址
0: kd> dq 0xfffff8a0`01ce0000
fffff8a0`01ce0000 fffff8a0`00005000 fffff8a0`01ce2000
fffff8a0`01ce0010 fffff8a0`02d31000 fffff8a0`03cb1000
fffff8a0`01ce0020 00000000`00000000 00000000`00000000
fffff8a0`01ce0030 00000000`00000000 00000000`00000000
fffff8a0`01ce0040 00000000`00000000 00000000`00000000
fffff8a0`01ce0050 00000000`00000000 00000000`00000000
fffff8a0`01ce0060 00000000`00000000 00000000`00000000
fffff8a0`01ce0070 00000000`00000000 00000000`00000000
0: kd> dt _HANDLE_TABLE_ENTRY fffff8a0`00005000+0x10*1
nt!_HANDLE_TABLE_ENTRY
+0x000 Object : 0xfffffa80`18db6891 Void
+0x000 ObAttributes : 0x18db6891
+0x000 InfoTable : 0xfffffa80`18db6891 _HANDLE_TABLE_ENTRY_INFO
+0x000 Value : 0xfffffa80`18db6891
+0x008 GrantedAccess : 0
+0x008 GrantedAccessIndex : 0
+0x00a CreatorBackTraceIndex : 0
+0x008 NextFreeTableEntry : 0
0: kd> dt _HANDLE_TABLE_ENTRY fffff8a0`00005000+0x10*2
nt!_HANDLE_TABLE_ENTRY
+0x000 Object : 0xfffffa80`18db6301 Void
+0x000 ObAttributes : 0x18db6301
+0x000 InfoTable : 0xfffffa80`18db6301 _HANDLE_TABLE_ENTRY_INFO
+0x000 Value : 0xfffffa80`18db6301
+0x008 GrantedAccess : 0
+0x008 GrantedAccessIndex : 0
+0x00a CreatorBackTraceIndex : 0
+0x008 NextFreeTableEntry : 0
0: kd> !object 0xfffffa80`18db6300
Object: fffffa8018db6300 Type: (fffffa8018db6080) Thread
ObjectHeader: fffffa8018db62d0 (new version)
HandleCount: 0 PointerCount: 1
0: kd> dt _HANDLE_TABLE_ENTRY fffff8a0`00005000+0x10*3
nt!_HANDLE_TABLE_ENTRY
+0x000 Object : 0xfffffa80`18e22b51 Void
+0x000 ObAttributes : 0x18e22b51
+0x000 InfoTable : 0xfffffa80`18e22b51 _HANDLE_TABLE_ENTRY_INFO
+0x000 Value : 0xfffffa80`18e22b51
+0x008 GrantedAccess : 0
+0x008 GrantedAccessIndex : 0
+0x00a CreatorBackTraceIndex : 0
+0x008 NextFreeTableEntry : 0
0: kd> !object 0xfffffa80`18e22b50
Object: fffffa8018e22b50 Type: (fffffa8018db6080) Thread
ObjectHeader: fffffa8018e22b20 (new version)
HandleCount: 0 PointerCount: 1
0: kd> dt _HANDLE_TABLE_ENTRY fffff8a0`00005000+0x10*0x48
nt!_HANDLE_TABLE_ENTRY
+0x000 Object : 0xfffffa80`1a4f94e1 Void
+0x000 ObAttributes : 0x1a4f94e1
+0x000 InfoTable : 0xfffffa80`1a4f94e1 _HANDLE_TABLE_ENTRY_INFO
+0x000 Value : 0xfffffa80`1a4f94e1
+0x008 GrantedAccess : 0
+0x008 GrantedAccessIndex : 0
+0x00a CreatorBackTraceIndex : 0
+0x008 NextFreeTableEntry :
//最低2位属性位0
0: kd> !object 0xfffffa80`1a4f94e0
Object: fffffa801a4f94e0 Type: (fffffa8018d45910) Process
ObjectHeader: fffffa801a4f94b0 (new version)
HandleCount: 1 PointerCount: 23
0: kd> dt _EPROCESS 0xfffffa80`1a4f94e0
nt!_EPROCESS
+0x000 Pcb : _KPROCESS
+0x160 ProcessLock : _EX_PUSH_LOCK
+0x168 CreateTime : _LARGE_INTEGER 0x01d74577`307d5623
+0x170 ExitTime : _LARGE_INTEGER 0x0
+0x178 RundownProtect : _EX_RUNDOWN_REF
+0x180 UniqueProcessId : 0x00000000`00000120 Void
+0x188 ActiveProcessLinks : _LIST_ENTRY [ 0xfffffa80`1a3f92a8 - 0xfffffa80`18db6a18 ]
+0x198 ProcessQuotaUsage : [2] 0x5e0
+0x1a8 ProcessQuotaPeak : [2] 0xb70
+0x1b8 CommitCharge : 0x81
+0x1c0 QuotaBlock : 0xfffff800`0404e940 _EPROCESS_QUOTA_BLOCK
+0x1c8 CpuQuotaBlock : (null)
+0x1d0 PeakVirtualSize : 0x1186000
+0x1d8 VirtualSize : 0x3fe000
+0x1e0 SessionProcessLinks : _LIST_ENTRY [ 0x00000000`00000000 - 0x00000000`00000000 ]
+0x1f0 DebugPort : (null)
+0x1f8 ExceptionPortData : (null)
+0x1f8 ExceptionPortValue : 0
+0x1f8 ExceptionPortState : 0y000
+0x200 ObjectTable : 0xfffff8a0`002fba50 _HANDLE_TABLE
+0x208 Token : _EX_FAST_REF
+0x210 WorkingSetPage : 0x27093
+0x218 AddressCreationLock : _EX_PUSH_LOCK
+0x220 RotateInProgress : (null)
+0x228 ForkInProgress : (null)
+0x230 HardwareTrigger : 0
+0x238 PhysicalVadRoot : (null)
+0x240 CloneRoot : (null)
+0x248 NumberOfPrivatePages : 0x6d
+0x250 NumberOfLockedPages : 0
+0x258 Win32Process : (null)
+0x260 Job : (null)
+0x268 SectionObject : 0xfffff8a0`002f2d50 Void
+0x270 SectionBaseAddress : 0x00000000`48380000 Void
+0x278 Cookie : 0xec99f693
+0x27c UmsScheduledThreads : 0
+0x280 WorkingSetWatch : (null)
+0x288 Win32WindowStation : (null)
+0x290 InheritedFromUniqueProcessId : 0x00000000`00000004 Void
+0x298 LdtInformation : (null)
+0x2a0 Spare : (null)
+0x2a8 ConsoleHostProcess : 0
+0x2b0 DeviceMap : 0xfffff8a0`00008bc0 Void
+0x2b8 EtwDataSource : (null)
+0x2c0 FreeTebHint : 0x000007ff`fffdc000 Void
+0x2c8 FreeUmsTebHint : 0x00000001`00000000 Void
+0x2d0 PageDirectoryPte : _HARDWARE_PTE
+0x2d0 Filler : 0
+0x2d8 Session : (null)
+0x2e0 ImageFileName : [15] "smss.exe"
+0x2ef PriorityClass : 0x2 ''
+0x2f0 JobLinks : _LIST_ENTRY [ 0x00000000`00000000 - 0x00000000`00000000 ]
+0x300 LockedPagesList : (null)
+0x308 ThreadListHead : _LIST_ENTRY [ 0xfffffa80`1a36af78 - 0xfffffa80`1a49a8e8 ]
+0x318 SecurityPort : (null)
+0x320 Wow64Process : (null)
+0x328 ActiveThreads : 2
+0x32c ImagePathHash : 0x1dcd0eb1
+0x330 DefaultHardErrorProcessing : 1
+0x334 LastThreadExitStatus : 0n0
+0x338 Peb : 0x000007ff`fffd4000 _PEB
+0x340 PrefetchTrace : _EX_FAST_REF
+0x348 ReadOperationCount : _LARGE_INTEGER 0x0
+0x350 WriteOperationCount : _LARGE_INTEGER 0x0
+0x358 OtherOperationCount : _LARGE_INTEGER 0x5
+0x360 ReadTransferCount : _LARGE_INTEGER 0x0
+0x368 WriteTransferCount : _LARGE_INTEGER 0x0
+0x370 OtherTransferCount : _LARGE_INTEGER 0x54
+0x378 CommitChargeLimit : 0
+0x380 CommitChargePeak : 0x99
+0x388 AweInfo : (null)
+0x390 SeAuditProcessCreationInfo : _SE_AUDIT_PROCESS_CREATION_INFO
+0x398 Vm : _MMSUPPORT
+0x420 MmProcessLinks : _LIST_ENTRY [ 0xfffffa80`1a3f9540 - 0xfffffa80`18db6cb0 ]
+0x430 HighestUserAddress : 0x000007ff`ffff0000 Void
+0x438 ModifiedPageCount : 0x30
+0x43c Flags2 : 0xd000
+0x43c JobNotReallyActive : 0y0
+0x43c AccountingFolded : 0y0
+0x43c NewProcessReported : 0y0
+0x43c ExitProcessReported : 0y0
+0x43c ReportCommitChanges : 0y0
+0x43c LastReportMemory : 0y0
+0x43c ReportPhysicalPageChanges : 0y0
+0x43c HandleTableRundown : 0y0
+0x43c NeedsHandleRundown : 0y0
+0x43c RefTraceEnabled : 0y0
+0x43c NumaAware : 0y0
+0x43c ProtectedProcess : 0y0
+0x43c DefaultPagePriority : 0y101
+0x43c PrimaryTokenFrozen : 0y1
+0x43c ProcessVerifierTarget : 0y0
+0x43c StackRandomizationDisabled : 0y0
+0x43c AffinityPermanent : 0y0
+0x43c AffinityUpdateEnable : 0y0
+0x43c PropagateNode : 0y0
+0x43c ExplicitAffinity : 0y0
+0x43c Spare1 : 0y0
+0x43c ForceRelocateImages : 0y0
+0x43c DisallowStrippedImages : 0y0
+0x43c LowVaAccessible : 0y0
+0x440 Flags : 0x144c2841
+0x440 CreateReported : 0y1
+0x440 NoDebugInherit : 0y0
+0x440 ProcessExiting : 0y0
+0x440 ProcessDelete : 0y0
+0x440 Wow64SplitPages : 0y0
+0x440 VmDeleted : 0y0
+0x440 OutswapEnabled : 0y1
+0x440 Outswapped : 0y0
+0x440 ForkFailed : 0y0
+0x440 Wow64VaSpace4Gb : 0y0
+0x440 AddressSpaceInitialized : 0y10
+0x440 SetTimerResolution : 0y0
+0x440 BreakOnTermination : 0y1
+0x440 DeprioritizeViews : 0y0
+0x440 WriteWatch : 0y0
+0x440 ProcessInSession : 0y0
+0x440 OverrideAddressSpace : 0y0
+0x440 HasAddressSpace : 0y1
+0x440 LaunchPrefetched : 0y1
+0x440 InjectInpageErrors : 0y0
+0x440 VmTopDown : 0y0
+0x440 ImageNotifyDone : 0y1
+0x440 PdeUpdateNeeded : 0y0
+0x440 VdmAllowed : 0y0
+0x440 CrossSessionCreate : 0y0
+0x440 ProcessInserted : 0y1
+0x440 DefaultIoPriority : 0y010
+0x440 ProcessSelfDelete : 0y0
+0x440 SetTimerResolutionLink : 0y0
+0x444 ExitStatus : 0n259
+0x448 VadRoot : _MM_AVL_TABLE
+0x488 AlpcContext : _ALPC_PROCESS_CONTEXT
+0x4a8 TimerResolutionLink : _LIST_ENTRY [ 0x00000000`00000000 - 0x00000000`00000000 ]
+0x4b8 RequestedTimerResolution : 0
+0x4bc ActiveThreadsHighWatermark : 4
+0x4c0 SmallestTimerResolution : 0
+0x4c8 TimerResolutionStackRecord : (null)
0: kd> g
如果是win10 最后的HANDLE_TABLE_ENTRY 要把地址右移4个16进制(0x10)再&0xFFFFFFFFFFFFFFF0
#include <ntifs.h>
#define MAX_ENTRY_COUNT (0x1000/16) //256 一级表中的 HANDLE_TABLE_ENTRY个数
#define MAX_ADDR_COUNT (0x1000/8) //512 二级表和 三级表中的地址个数
//ImageFileName偏移
#define x64_offset_ImageFileName 0x2E0
#define x86_offset_ImageFileName 0x16C
EXTERN_C NTKERNELAPI PVOID NTAPI ObGetObjectType(IN PVOID pObject);
EXTERN_C NTKERNELAPI UCHAR* PsGetProcessImageFileName(IN PEPROCESS Process);
//x64
typedef struct _HANDLE_TABLE
{
ULONGLONG TableCode; //0x0
PVOID QuotaProcess; //0x8
VOID* UniqueProcessId; //0x10
ULONG64 HandleLock; //0x18
struct _LIST_ENTRY HandleTableList; //0x20
ULONG64 HandleContentionEvent; //0x30
PVOID DebugInfo; //0x38
LONG ExtraInfoPages; //0x40
union
{
ULONG Flags; //0x44
UCHAR StrictFIFO : 1; //0x44
};
ULONG FirstFreeHandle; //0x48
struct _HANDLE_TABLE_ENTRY* LastFreeHandleEntry; //0x50
ULONG HandleCount; //0x58
ULONG NextHandleNeedingPool; //0x5c
ULONG HandleCountHighWatermark; //0x60
}HANDLE_TABLE, *PHANDLE_TABLE;
typedef struct _HANDLE_TABLE_ENTRY
{
union
{
//86 64..
ULONG_PTR Object; //0x0
ULONG ObAttributes; //0x0
//86 64
struct _HANDLE_TABLE_ENTRY_INFO* InfoTable; //0x0
ULONG_PTR Value; //0x0
};
union
{
ULONG GrantedAccess; //0x8
struct
{
USHORT GrantedAccessIndex; //0x8
USHORT CreatorBackTraceIndex; //0xa
};
ULONG NextFreeTableEntry; //0x8
};
}HANDLE_TABLE_ENTRY, *PHANDLE_TABLE_ENTRY;
//判断多少个进程
ULONG_PTR ObjectCount = 0;
SIZE_T FindCidTableAddr()
{
SIZE_T CidTableAddr = 0;
PUCHAR startAddr = (PUCHAR)ObGetObjectType;
for (SIZE_T i = 0; i < 100; i++)
{
#ifdef _WIN64
if (*(startAddr + i) == 0x48 && *(startAddr + i + 1) == 0x8b && *(startAddr + i + 2) == 0x0d)
{
//0x48 8b 0d后面的地址f1e0edff小端序 0xffede0f1+它下一行的地址 然后第31位置0
CidTableAddr = (SIZE_T)(*(PULONG)(startAddr + i + 3) + (startAddr + i + 3 + 4)) & 0xFFFFFFFEFFFFFFFF;
break;
}
#elif _WIN32
if (*(startAddr + i) == 0x8b && *(startAddr + i + 1) == 0x3d)
{
//0x48 8b 0d后面的地址f1e0edff小端序 0xffede0f1+它下一行的地址 然后第31位置0
CidTableAddr = (SIZE_T)(*(PULONG)(startAddr + i + 2));
break;
}
#endif _WIN64
}
return CidTableAddr;
}
NTSTATUS Operation0(ULONG_PTR TableCode)
{
PHANDLE_TABLE_ENTRY HandleTableEntry = NULL;
ULONG Index = 0;
HandleTableEntry = (PHANDLE_TABLE_ENTRY)((ULONG_PTR*)(TableCode));
for (Index = 0; Index < (PAGE_SIZE / sizeof(HANDLE_TABLE_ENTRY)); Index++)
{
if (MmIsAddressValid((PVOID)HandleTableEntry))
{
PVOID ObjectBody = (PVOID)(*(ULONG_PTR*)HandleTableEntry & ~3);
if (MmIsAddressValid(ObjectBody))
{
#ifdef _WIN64
UCHAR Type = *((PUCHAR)((ULONG64)ObjectBody - 0x30 + 0x18));
#elif _WIN32
UCHAR Type = *((PUCHAR)((ULONG)ObjectBody - 0x18 + 0xC));
#endif // _WIN64
if (MmIsAddressValid(ObjectBody) && Type == 7) //这里应当判断对象是否合法
{
//打印数量以及ObjectBody的地址
ObjectCount++;
#ifdef _WIN64
DbgPrint("ObjectCount:%d Type:%X ObjectBody:%p ProcessName:%s r ", ObjectCount, Type, ObjectBody, (PULONG_PTR)((ULONG_PTR)ObjectBody + x64_offset_ImageFileName));
#else
DbgPrint("ObjectCount:%d Type:%X ObjectBody:%p ProcessName:%s r ", ObjectCount, Type, ObjectBody, (PULONG_PTR)((ULONG_PTR)ObjectBody + x86_offset_ImageFileName));
#endif // _WIN64
}
}
}
HandleTableEntry++; //结构体指针++ 越过当前这个结构体
}
return STATUS_SUCCESS;
}
NTSTATUS EnumProcessByHandle()
{
PHANDLE_TABLE_ENTRY TableLevel1, *TableLevel2, **TableLevel3;
DbgBreakPoint();
ULONG_PTR TableCode = *(ULONG_PTR*)(*(ULONG_PTR*)(FindCidTableAddr()));
if (!TableCode)
{
DbgPrint("获取CidTable失败!");
}
ULONG_PTR TableLevel = TableCode & 3;
TableCode = TableCode & (~3);
switch (TableLevel)
{
case 0:
{
Operation0(TableCode);
break;
}
case 1:
{
TableLevel2 = TableCode;
SIZE_T i = 0;
while (TableLevel2[i])
{
Operation0(TableLevel2[i]);
i++;
}
break;
}
}
}
NTSTATUS DriverUnload(PDRIVER_OBJECT pDriver)
{
DbgPrint("Driver Unload!n");
return STATUS_SUCCESS;
}
NTSTATUS DriverEntry(PDRIVER_OBJECT pDriver, PUNICODE_STRING pRegpath)
{
EnumProcessByHandle();
pDriver->DriverUnload = DriverUnload;
return STATUS_SUCCESS;
}
最后
以上就是苹果汉堡最近收集整理的关于x64 Global HANDLE 全局句柄表全局句柄表的全部内容,更多相关x64内容请搜索靠谱客的其他文章。
本图文内容来源于网友提供,作为学习参考使用,或来自网络收集整理,版权属于原作者所有。








发表评论 取消回复