location规则
location是nginx的精华,nginx就是通过拦截到的请求去对配置好的location块(location block)进行请求代理的。
location是用来具体配置代理路径的,具体格式如下:
location [=|~|~*|^~|@] /uri/ { … }
语法规则:
= 开头表示精确匹配
^~ 开头表示uri以某个常规字符串开头,理解为匹配 url路径即可。nginx不对url做编码,因此请求
为/static/20%/aa,可以被规则^~ /static/ /aa匹配到(注意是空格)。
~ 开头表示区分大小写的正则匹配
~* 开头表示不区分大小写的正则匹配
!~ 区分大小写不匹配正则
!~* 不区分大小写不匹配正则
/ 通用匹配,任何请求都会匹配到。
Localtion的匹配规则的优先级
首先匹配 =
其次匹配 ^~
其次是按文件中顺序的正则匹配,
最后是交给 / 通用匹配。
当有匹配成功时候,停止匹配,按当前匹配规则处理请求。
#第三个规则就是通用规则,用来转发动态请求到后端应用服务器
#非静态文件请求就默认是动态请求,自己根据实际把握
实例:
若是用源码安装的nginx测试,则需要添加echo模块
模块:https://github.com/openresty/echo-nginx-module
[root@nginx1 ~]# ls
v0.61.tar.gz
[root@nginx1 ~]# tar xf v0.61.tar.gz -C /usr/local/src/
[root@nginx1 ~]# systemctl stop nginx
[root@nginx1 ~]# nginx -V
nginx version: nginx/1.15.0
built by gcc 4.8.5 20150623 (Red Hat 4.8.5-36) (GCC)
built with OpenSSL 1.0.2k-fips 26 Jan 2017
TLS SNI support enabled
configure arguments: --prefix=/opt/data/nginx --with-http_stub_status_module --with-http_ssl_module --with-stream
[root@nginx1 ~]# cd /usr/local/srcnginx-1.15.0/
[root@nginx1 nginx-1.15.0]# ./configure --prefix=/opt/data/nginx --with-http_stub_status_module --with-http_ssl_module --with-stream --add-module=/usr/local/src/echo-nginx-module-0.61
[root@nginx1 nginx-1.15.0]# echo $?
0
[root@nginx1 nginx-1.15.0]# make # 不要make install
[root@nginx1 nginx-1.15.0]# echo $?
0
[root@nginx1 nginx-1.15.0]# cp objs/nginx /opt/data/nginx/sbin/nginx
[root@nginx1 nginx-1.15.0]# systemctl start nginx
配置文件:
[root@nginx1 ~]# cd /opt/data/nginx/conf/conf.d
[root@nginx1 conf.d]# vim test1.conf
server {
listen 192.168.10.21:80;
server_name www.test1.com;
access_log /opt/data/nginx/data/test1/log/access.log combined;
#location / {
# root /opt/data/nginx/data/test1/basic;
# index index.html index.htm;
#}
location / {
echo "/";
}
location =/ {
echo "=/";
}
location =/nginx {
echo "nginx";
}
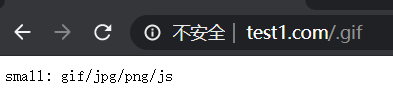
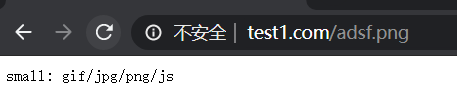
location ~ .(gif|jpg|png|css|js)$ {
echo "small: gif/jpg/png/js";
}
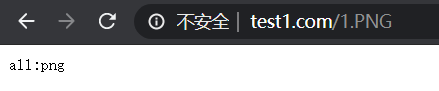
location ~* .png$ {
echo "all:png";
}
location ^~ /abc/ {
echo "abc";
}
}
[root@nginx1 conf.d]# systemctl restart nginx测试:可以配置主机hosts文件:C:WindowsSystem32driversetchosts
(1)输出www.test1.com,精确匹配,因为url默认后面带一个/
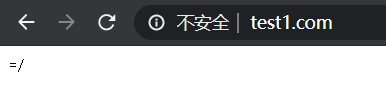
(2)输入www.test1.com/123匹配到的是/,此时匹配时先跳过/,依次向下匹配,最终没有匹配到,则会匹配/
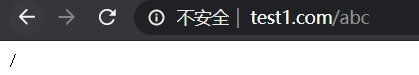
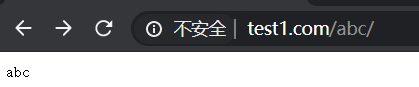
(3)输入www.test1.com/abc/ 匹配到 ^~ /abc/ 。注意:此处abc后不加/则默认匹配到/,区分大小写匹配正则
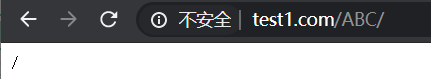
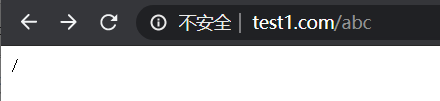
(4)输入www.test1.com/.gif,区分大小写匹配
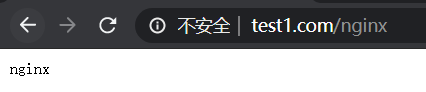
(5)输出www.test1.com/nginx
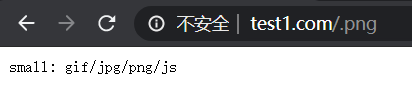
(6)输入www.test.com/.png

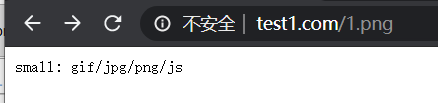
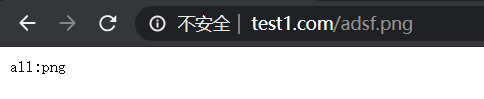
注意: ~ .(gif|jpg|png|css|js)$ 和 ~* .png$ 优先级是一样的,此时看配置文件的先后顺序,在前的匹配。
如把配置文件中的两项调换位置后重启服务
2. 地址重写
location [/|=/|...] {
rewrite old new [permanent|redirect];
break|last;# 可以不写
}
old:需要被替换的URL或URI或字符串
new:需要用来替换的URL或URI或字符串
break:本条规则匹配完成后,终止匹配,不在向下进行
last:表示完成rewrite。
permanent == 301 :返回301--> 永久重定向
redirect == 302 :返回302 -->临时重定向
注:permanent和redirect的区别是返回的不同方式的重定向;一般状态下对于客户端没有影响。
对于搜索引擎:
对于301:搜索引擎会把老地址的相关信息带到新地址,同时在搜索引擎中彻底废掉老地址。
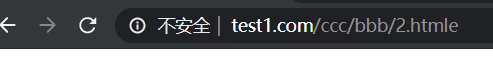
对于302:搜索引擎有时会查看老地址和新地址哪个更加直观,然后决定显示那个。所以有时候会出现页面不跳转,URL劫持的现象。有时候老地址相关参数会在新地址中用到,可以用()和$方式来解决。(1)'http://www.test1.com/abc/a/1.html ---> http://www.test1.com/ccc/bbb/2.html'
[root@nginx1 data]# vim /etc/nginx/conf.d/test1.conf
server {
listen 192.168.10.21:80;
server_name www.test1.com;
access_log /opt/data/nginx/data/test1/log/access.log combined;
location /abc/1.html {
rewrite .* /ccc/bbb/2.html permanent;
}
}验证:访问www.test1.com/abc/a/1.html
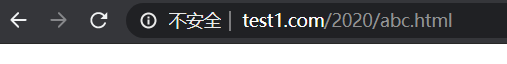
(2)http://www.test1.com/2015/abc.html --> http://www.test1.com/2020/abc.html
server {
listen 192.168.10.21:80;
server_name www.test1.com;
access_log /opt/data/nginx/data/test1/log/access.log combined;
location /2015 {
rewrite ^/2015/(.*)$ /2020/$1 permanent;
}
}验证:访问www.test1.com/2015/abc.html
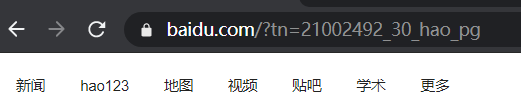
(3)http://www.test1.com/aaa/1.html --> http://www.baidu.com
server {
listen 192.168.10.21:80;
server_name www.test1.com;
access_log /opt/data/nginx/data/test1/log/access.log combined;
location /aaa/1.html {
rewrite .* http://www.baidu.com permanent;
}
}验证:访问www.test1.com/aaa/1.html
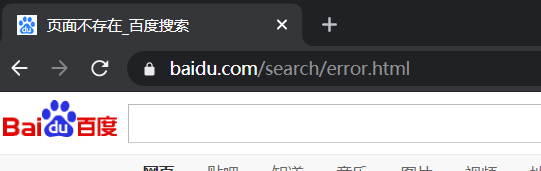
(4)http://www.test1com/ccc/1.html ---> http://www.baidu.com/ccc/1.html
server {
listen 192.168.10.21:80;
server_name www.test1.com;
access_log /opt/data/nginx/data/test1/log/access.log combined;
location ~ /ccc/1.html {
rewrite ^/(.*)$ http://www.baidu.com/$1;
}
}
# location可以写成上面和下面的都可以 ,任选其一
location ~ /ccc/1.html {
rewrite .* http://www.baidu.com$request_uri permanent;
}验证:访问www.test1.com/ccc/1.html
(5)http://www.test1.com/ccc ---> http://www.test1.com/ccc/
location / {
if ( -d $request_filename ) {
rewrite ^(.*)([^/])$ http://$host$1$2/ permanent;
}
}
# 若服务器上存在请求的uri目录,就改写验证:访问www.test1.com/cc
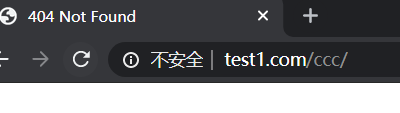
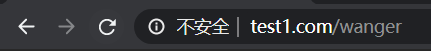
(6)http://www.test1.com/login/wanger.html ===》 http://www.test1.com/reg/login.php?user=wanger
location /login {
rewrite ^/login/(.*).html$ /reg/login.php?user=$1 permanent;
}验证:访问www.test1.com/login/wanger
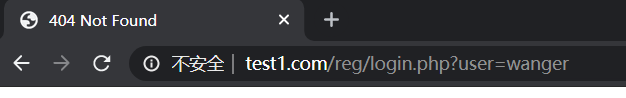
(7)http://www.test1.cam/uplook/11-22-33.html --> http://www.test1.com/uplook/11/22/33.html
location /uplook {
rewrite ^(.*)-(.*)-(.*)$ $1/$2/$3 permanent;
}
# 或者 rewrite ^/uplook/([0-9]+)-([0-9]+)-([0-9]+).html /uplook/$1/$2/$3.html permanent;验证:访问www.test1.com/uplock/11-22-33.html
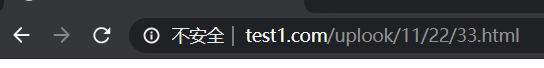
(8)http://wanger.test1.com --> http://www.test1.com/wanger
需要添加域名解析;此处需要了解一个DNS泛解析:www.test1.com ---> 实际上com后面还有一个. 在域名解析过程中,先去查找最后一个. 然后再查找com,在查找test1 ,最后查找www
location / {
if ( $host ~* "^(.*).test1.com$" ) {
echo $host;
set $user $1;
rewrite .* http://www.test1.com/$user permanent;
}
}此时访问wanger.test1.com时,结果www.test1.com/wanger
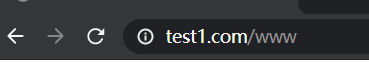
因为 跳转后会再次匹配,此时set $user $1 已经变成了www;只需要再次判断即可
server {
listen 192.168.10.21:80;
#server_name www.test1.com;
access_log /opt/data/nginx/data/test1/log/access.log combined;
location / {
if ( $host ~* www.test1.com ){
break;
}
if ( $host ~* "^(.*).test1.com$" ) {
echo $host;
set $user $1;
rewrite .* http://www.test1.com/$user permanent;
}
}
}
(9) 80端口 ---》 443端口
server {
listen 192.168.10.21:80;
server_name www.test1.com test1.com;
return 301 https://www.test1.com$request_uri;
}
server {
listen 192.168.10.21:443;
server_name www.test1.com
ssl on; # 开启模块
ssl_certificate /usr/local/nginx/cert.pem; #证书
ssl_certificate_key /usr/local/nginx/cert.key; # 密钥
}
若走公网,则需要买证书,此为测试,用命令生成一个证书即可,只限于测试。
[root@nginx1 nginx]# cat /etc/redhat-release
CentOS Linux release 7.6.1810 (Core)
[root@nginx1 nginx]# uname -r
3.10.0-957.el7.x86_64
[root@nginx1 nginx]# nginx -V
nginx version: nginx/1.15.0
built by gcc 4.8.5 20150623 (Red Hat 4.8.5-36) (GCC)
built with OpenSSL 1.0.2k-fips 26 Jan 2017
TLS SNI support enabled
configure arguments: --prefix=/opt/data/nginx --with-http_stub_status_module --with-http_ssl_module --with-stream --add-module=/usr/local/src/echo-nginx-module-0.61
[root@nginx1 nginx]# cd /etc/pki/CA/
# 此证书是基于appache生成的。若没有此目录则需要安装http服务。
[root@nginx1 CA]# ls
certs crl newcerts private
# 生成私钥
[root@nginx1 CA]# openssl genrsa -out private/cakey.pem 2048
Generating RSA private key, 2048 bit long modulus
.....+++
..+++
e is 65537 (0x10001)
# 生成签名证书
[root@nginx1 CA]# openssl req -new -x509 -key private/cakey.pem -out cacert.pem -days 365 #指定过期时间365天
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN #country
State or Province Name (full name) []:bigqin #省份
Locality Name (eg, city) [Default City]:SL #城市
Organization Name (eg, company) [Default Company Ltd]:2020 #公司
Organizational Unit Name (eg, section) []:test # 部门
Common Name (eg, your name or your server's hostname) []:192.168.10.21 #服务器名字或者ip
Email Address []:2020@test #邮箱
# 生成索引
[root@nginx1 CA]# touch index.txt
# 生成序列号文件
[root@nginx1 CA]# echo 01 > serial
[root@nginx1 CA]# cd /opt/data/nginx/
[root@nginx1 nginx]# mkdir cert
[root@nginx1 nginx]# cd cert/
[root@nginx1 certs]# (umask 077; openssl genrsa -out nginx.key 2048)
Generating RSA private key, 2048 bit long modulus
...................................................................................+++
........................................+++
e is 65537 (0x10001)
[root@nginx1 cert]# openssl req -new -key nginx.key -out nginx.csr
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN #country
State or Province Name (full name) []:bigqin #省份
Locality Name (eg, city) [Default City]:SL # 城市
Organization Name (eg, company) [Default Company Ltd]:2020 # 公司
Organizational Unit Name (eg, section) []:test #单位
Common Name (eg, your name or your server's hostname) []: #此处要和服务器名字相同或者IP
Email Address []:2020@test # 邮箱地址
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
[root@nginx1 cert]# ls
nginx.csr nginx.key
[root@nginx1 certs]# openssl ca -in nginx.csr -out /opt/data/nginx/certs/nginx.crt
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 1 (0x1)
Validity
Not Before: Jul 29 16:05:08 2020 GMT
Not After : Jul 29 16:05:08 2021 GMT
Subject:
countryName = CN
stateOrProvinceName = bigqin
organizationName = 2020
organizationalUnitName = test
commonName = 192.168.10.21
emailAddress = 2020@test
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
C2:86:8F:7B:89:88:BC:8F:E5:1E:0A:17:B6:B1:6E:95:B7:E9:39:DF
X509v3 Authority Key Identifier:
keyid:A6:BD:5B:49:DF:10:5A:C6:A9:0C:35:EA:D5:B7:47:60:F4:64:4B:AC
Certificate is to be certified until Jul 29 16:05:08 2021 GMT (365 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Update配置完成,配置服务文件
[root@nginx1 ~]# cd /opt/data/nginx/conf/conf.d
[root@nginx1 conf.d]# vim test1.conf
server {
listen 192.168.10.21:80;
server_name www.test1.com test1.com;
return 301 https://www.test1.com$request_uri;
}
server {
listen 192.168.10.21:443;
server_name www.test1.com
ssl on;
ssl_certificate /opt/data/nginx/certs/nginx.crt; #此时要和刚才生成的证书对应上
ssl_certificate_key /opt/data/nginx/certs/nginx.key;
}
[root@nginx1 ~]# nginx -t
nginx: the configuration file /opt/data/nginx/conf/nginx.conf syntax is ok
nginx: configuration file /opt/data/nginx/conf/nginx.conf test is successful
[root@nginx1 ~]# systemctl restart nginx
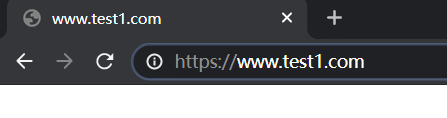
[root@nginx1 ~]# netstat -tunalp
tcp 0 0 192.168.10.21:443 0.0.0.0:* LISTEN 20127/nginx: master验证:访问www.test1.com --> 自动跳转为https://www.test1.com
(10)404 ---> err.html
server {
listen 192.168.10.21:80;
server_name www.test1.com;
access_log /opt/data/nginx/data/test1/log/access.log combined;
location / {
root /opt/data/nginx/data/test1/basic;
if ( !-e $request_filename ){
rewrite .* /err.html permanent;
}
}
}
[root@nginx1 conf.d]# ll /opt/data/nginx/data/test1/basic/
总用量 8
-rw-r--r--. 1 root root 46 7月 30 08:56 err.html
-rw-r--r--. 1 root root 34 7月 28 21:56 index.html
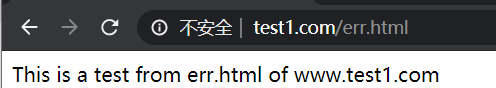
[root@nginx1 conf.d]# cat /opt/data/nginx/data/test1/basic/err.html
This is a test from err.html of www.test1.com验证:访问www.test1.com/abc时,自动跳转
最后
以上就是震动魔镜最近收集整理的关于Nginx的location规则及地址重写location规则2. 地址重写的全部内容,更多相关Nginx内容请搜索靠谱客的其他文章。








发表评论 取消回复