主机规划
10.10.100.94 master
10.10.100.93 slave
10.10.100.92 client
(一)环境:
名称 版本
CentOS CentOS release 6.7(Final)
Kerberos
krb5-server-1.10.3-57.el6.x86_64
krb5-workstation-1.10.3-57.el6.x86_64
krb5-libs-1.10.3-57.el6.x86_64
krb5-auth-dialog-0.13-5.el6.x86_64
名称 作用
10.10.100.95 Kerberos master
10.10.100.96 Kerberos slave
1、需要准备:
http://www.cloudera.com/content/www/zh-CN/documentation/enterprise/5-3-x/topics/cm_sg_s2_jce_policy.html
jdk7对应的策略文件下载地址:
http://www.oracle.com/technetwork/java/javase/downloads/jce-7-download-432124.html
jdk8:
http://www.oracle.com/technetwork/java/javase/downloads/index.html
2、安装kdc server 和client
#yum install krb5-server krb5-libs krb5-auth-dialog -y
#yum install krb5-workstation -y
yum -y remove krb5-devel
yum -y remove krb5-workstation
yum -y remove krb5-libs
yum -y remove krb5-auth-dialog
rpm -qa | grep krb5
(二)配置
1)主机名称配置
在master 和slave 服务器上添加主机名称及对应的域名
# vim /etc/hosts
10.10.100.95 kerberos.example.com kerberos
10.10.100.95 kdc.example.com kdc
10.10.100.96 kerberos2.example.com kerberos2
2)master配置---从初始化安装开始
vi /etc/krb5.conf
*******************************************************************************
[logging]
default = FILE:/var/log/krb5libs.log
kdc= FILE:/var/log/krb5kdc.log
admin_server = FILE:/var/log/kadmind.log
[libdefaults]
default_realm = EXAMPLE.COM
dns_lookup_realm = false
dns_lookup_kdc = false
ticket_lifetime = 24h
forwardable = yes
[realms]
EXAMPLE.COM = {
kdc= kerberos.example.com
kdc= kerberos2.example.com:88
admin_server = kerberos.example.com:749
default_domain = example.com
}
[domain_realm]
.example.com = EXAMPLE.COM
example.com = EXAMPLE.COM
[appdefaults]
pam= {
debug = false
ticket_lifetime = 36000
renew_lifetime = 36000
forwardable = true
krb4_convert = false
}
*******************************************************************************
vi /var/kerberos/krb5kdc/kdc.conf
*******************************************************************************
[kdcdefaults]
v4_mode = nopreauth
kdc_tcp_ports = 88
[realms]
EXAMPLE.COM = {
master_key_type = aes256-cts
acl_file = /var/kerberos/krb5kdc/kadm5.acl
dict_file = /usr/share/dict/words
admin_keytab = /var/kerberos/krb5kdc/kadm5.keytab
supported_enctypes = aes256-cts:normal aes128-cts:normaldes3-hmac-sha1:normal arcfour-mac:normal des-hmac-sha1:normaldes-cbc-md5:normal des-cbc-crc:normal des-cbc-crc:v4 des-cbc-crc:afs3
}
*******************************************************************************
export KRB5_CONFIG=/etc/krb5.conf
exportKRB5_KDC_PROFILE=/var/kerberos/krb5kdc/kdc.conf
******************************************************************************
3 )生成master服务器上的kdc database
[root@kerberos ~]# kdb5_util create -r EXAMPLE.COM -s
Loading random data
Initializing database'/var/kerberos/krb5kdc/principal' for realm 'EXAMPLE.COM',
master key name 'K/M@EXAMPLE.COM'
You will be prompted for the databaseMaster Password.
It is important that you NOT FORGET thispassword.
Enter KDC database master key:
Re-enter KDC database master key to verify:
密码:ngaa.com.cn@test
将在/var/kerberos/krb5kdc/目录下生成多个文件,
相关生成文件的说明为:
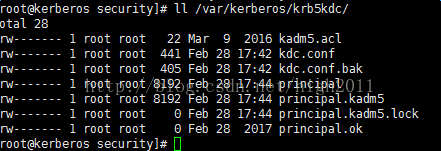
4)master服务器上,添加admin用户
[root@kerberos ~]# kadmin.local
Kadmin.local: addprinc admin/admin@EXAMPLE.COM
密码:admin@EXAMPLE.COM
5 )启动 kdc 服务 和 kadmin 服务
[root@kerberos ~]# servicekrb5kdc restart
[root@kerberos ~]# servicekadmin restart
添加开机启动: chkconfig krb5kdcon
chkconfig kadmin on
6)使用kinit 命令,测试admin账户是否生成成功(需要安装client端:
yum install krb5-workstation -y)
[root@kerberos ~]# kinit admin/admin@EXAMPLE.COM
密码:admin@EXAMPLE.COM
7 )安装slave KDC的相关配置
(7-1)创建host keytab 文件
在master服务器上
[root@kerberos ~]# kadmin.local
kadmin: addprinc -randkey host/kerberos.example.com #添加principal
kadmin:ktadd host/kerberos.example.com #生成keytab文件
kadmin: addprinc -randkey host/kerberos2.example.com #添加principal
kadmin:ktadd host/kerberos2.example.com #生成keytab文件
(7-2 )将master上的几个文件拷贝到从服务器,
文件: krb5.conf、kdc.conf、kadmin5.acl、master key stash file
[root@kerberos ~]# scp /etc/krb5.conf root@10.10.100.96:/etc
[root@kerberos ~]#
scp /var/kerberos/krb5kdc/kdc.confroot@10.10.100.96:/var/kerberos/krb5kdc/
[root@kerberos ~]#
scp /var/kerberos/krb5kdc/kadm5.aclroot@10.10.100.96:/var/kerberos/krb5kdc/
scp /var/kerberos/krb5kdc/.k5.EXAMPLE.COM root@10.10.100.96:/var/kerberos/krb5kdc/
.k5.EXAMPLE.COM
在slave服务器上(需要和master一样执行上面的操作:
安装server端和client端)
Slave上创建数据库
[root@kerberos ~]# kdb5_util create -r EXAMPLE.COM -s
Loading random data
Initializing database'/var/kerberos/krb5kdc/principal' for realm 'EXAMPLE.COM',
master key name 'K/M@EXAMPLE.COM'
You will be prompted for the databaseMaster Password.
It is important that you NOT FORGET thispassword.
Enter KDC database master key:
Re-enter KDC database master key to verify:
密码:ngaa.com.cn@test
添加规则:
[root@kerberos2 ~]# kadmin.local
kadmin: addprinc -randkey host/kerberos2.example.com #添加principal
kadmin: ktaddhost/kerberos2.example.com #生成keytab文件
(7-3 )在slave服务器上创建kpropd.acl文件
[root@kerberos2 ~]# touch /var/kerberos/krb5kdc/kpropd.acl
添加如下内容:
host/kerberos.example.com@EXAMPLE.COM
host/kerberos2.example.com@EXAMPLE.COM
(7-4)在slave上启动kpropd服务
[root@kerberos2 ~]# kpropd –S
和service krb5kdc start
至此,slave上的kdc服务还不能启动,因为无kdc的database数据
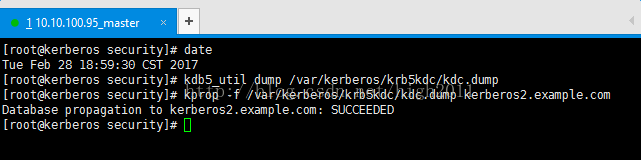
8)在master上将相关数据同步到slave上
[root@kerberos ~]# kdb5_util dump /var/kerberos/krb5kdc/kdc.dump
[root@kerberos~]#kprop -f /var/kerberos/krb5kdc/kdc.dumpkerberos2.example.com
成功后,会出现以下信息:
Database propagation to kerberos2.example.com: SUCCEEDED
以上命令,可以封装成一个bash,定时运行,即定时更新slave上的database。
(1)如果出现错误:
kprop: Client not found in Kerberosdatabase while getting initial ticket
解决:
在master上添加规则
kadmin: addprinc -randkey host/kerberos2.example.com #添加principal
kadmin:ktadd host/kerberos2.example.com #生成keytab文件
(2)如果出现错误:
[root@kerberos security]#
kprop -f /var/kerberos/krb5kdc/slave_datatrans kerberos2.example.com -P 749 -s -d
kprop: Server rejected authentication(during sendauth exchange) while authenticating to server
kprop: Decrypt integrity check failedsignalled from server
Error text from server: Decrypt integritycheck failed
更换命令:
[root@kerberos ~]# kdb5_util dump/var/kerberos/krb5kdc/kdc.dump
[root@kerberos~]#kprop -f/var/kerberos/krb5kdc/kdc.dump kerberos2.example.com
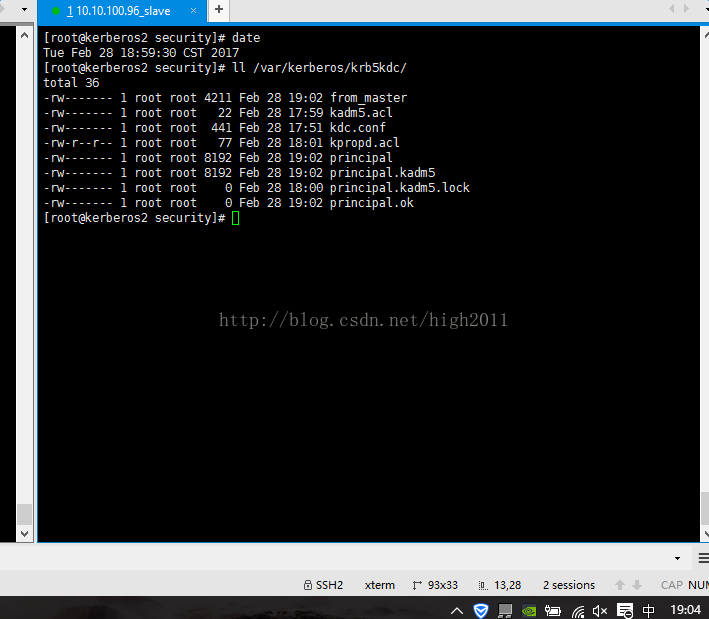
9)slave上/var/kerberos/krb5kdc/会多出一些文件,如:
from_master、principal、pricipal.kadm5、
principal.kadmin5.lock、 principal.ok
10)至此,可以启动slave上的kdc服务
#service krb5kdc restart
(三)测试主从是否生效(成功)
1)从第三台服务器,使用kinit获取ticket,正常情况下会从master上获取
2)关闭master上的kdc服务
3)再次从第三台服务器上,使用kinit 获取ticket,如果成功,说明生效。
也可以观察kdc的日志,在 /var/log/krb5kdc.log
注意:
需要有kdc client端
当有多台slave时,定时更新脚本可以这样:
#!/bin/sh
kdclist = "kerberos2.example.com kerberos3.example.com"
kdb5_util dump /var/kerberos/krb5kdc/slave_datatrans
for kdc in $kdclist
do
kprop -f /var/kerberos/krb5kdc/slave_datatrans $kdc
done
参考文档:
http://web.mit.edu/kerberos/krb5-latest/doc/admin/install_kdc.html
http://web.mit.edu/kerberos/krb5-current/doc/krb_admins/install_kdc.html
http://shanchao7932297.blog.163.com/blog/static/1363624201241725623761/
遇见问题参考:
http://research.imb.uq.edu.au/~l.rathbone/ldap/kerberos.shtml
最后
以上就是强健羽毛最近收集整理的关于[Kerberos基础]-- kdc集群主从搭建(kerberos相关)的全部内容,更多相关[Kerberos基础]--内容请搜索靠谱客的其他文章。




![[Kerberos基础]-- kdc集群主从搭建(kerberos相关)](https://www.shuijiaxian.com/files_image/reation/bcimg13.png)



发表评论 取消回复