之前写过Windows10 CMD 下 SSH 远程 Linux,实现 CMD/Powershell ssh 远程登录Linux。
是不是可以Linux ssh 到 windows呢?
查看 openssh 程序目录有没有sshd ,发现没有,
这时就需要另一个组件 OpenSSH-Win32或OpenSSH-Win64
下载地址:https://github.com/PowerShell/Win32-OpenSSH/releases
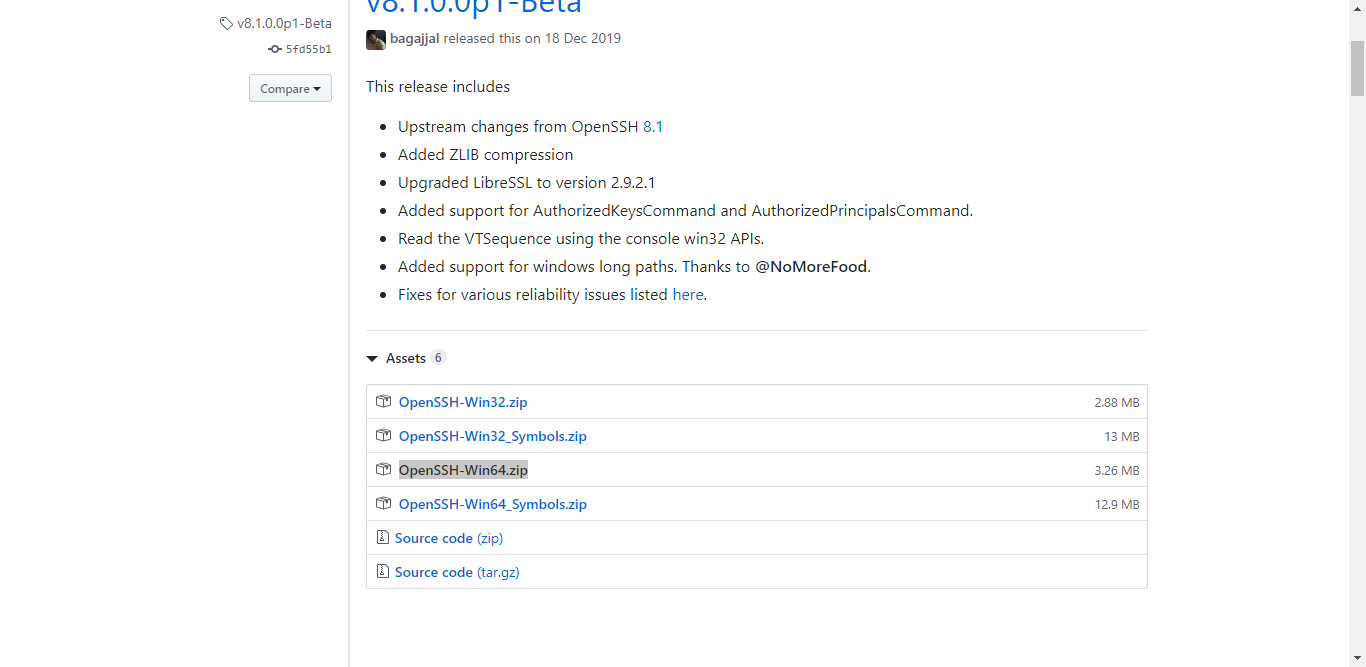
下载完成后安装:
把 OpenSSH-Win64.zip解压到 C:Program Files
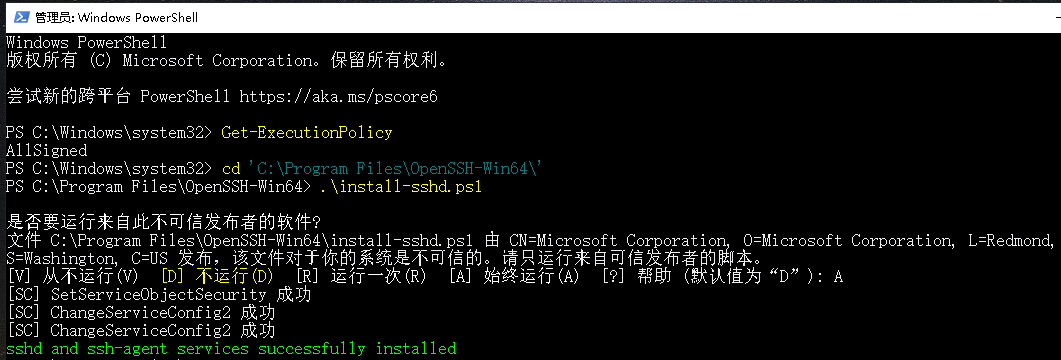
执行以下命令安装
1. 使用PowerShell,您必须确保Get-ExecutionPolicy不受限制。我们建议使用“Bypass”绕过策略来安装东西,或者使用“ AllSigned”以提高安全性。
2. 进入程序目录,运行install-sshd.ps1 脚本进行安装
3. 查看服务是否运行,进程里有sshd进程,说明sshd服务已启动。
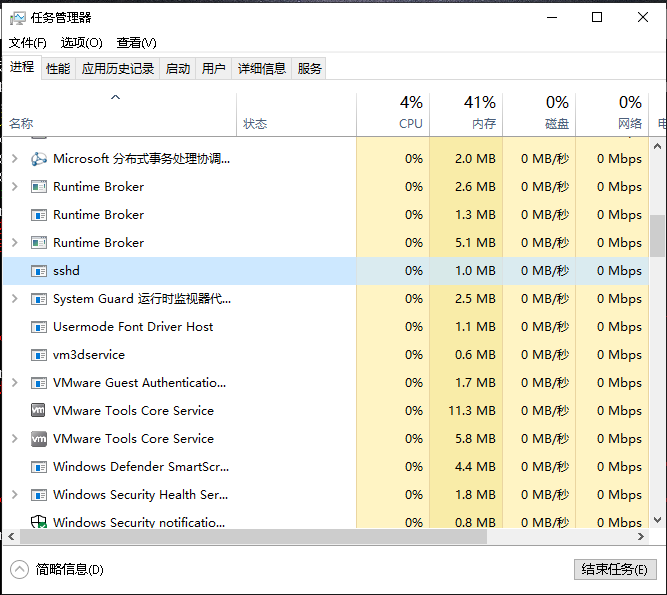
4. 配置sshd 服务,授权ssh远程访问 ,配置C:ProgramDatasshsshd_config文件
# This is the sshd server system-wide configuration file. See
# sshd_config(5) for more information.
# The strategy used for options in the default sshd_config shipped with
# OpenSSH is to specify options with their default value where
# possible, but leave them commented. Uncommented options override the
# default value.
Port 22
#AddressFamily any
#ListenAddress 0.0.0.0
#ListenAddress ::
#HostKey __PROGRAMDATA__/ssh/ssh_host_rsa_key
#HostKey __PROGRAMDATA__/ssh/ssh_host_dsa_key
#HostKey __PROGRAMDATA__/ssh/ssh_host_ecdsa_key
#HostKey __PROGRAMDATA__/ssh/ssh_host_ed25519_key
# Ciphers and keying
#RekeyLimit default none
# Logging
#SyslogFacility AUTH
#LogLevel INFO
# Authentication:
#LoginGraceTime 2m
#PermitRootLogin prohibit-password
#StrictModes yes
StrictModes no
#MaxAuthTries 6
#MaxSessions 10
PubkeyAuthentication yes
# The default is to check both .ssh/authorized_keys and .ssh/authorized_keys2
# but this is overridden so installations will only check .ssh/authorized_keys
AuthorizedKeysFile .ssh/authorized_keys
#AuthorizedPrincipalsFile none
# For this to work you will also need host keys in %programData%/ssh/ssh_known_hosts
#HostbasedAuthentication no
# Change to yes if you don't trust ~/.ssh/known_hosts for
# HostbasedAuthentication
#IgnoreUserKnownHosts no
# Don't read the user's ~/.rhosts and ~/.shosts files
#IgnoreRhosts yes
# To disable tunneled clear text passwords, change to no here!
PasswordAuthentication yes
PermitEmptyPasswords no
# GSSAPI options
#GSSAPIAuthentication no
#AllowAgentForwarding yes
#AllowTcpForwarding yes
#GatewayPorts no
#PermitTTY yes
#PrintMotd yes
#PrintLastLog yes
#TCPKeepAlive yes
#UseLogin no
#PermitUserEnvironment no
#ClientAliveInterval 0
#ClientAliveCountMax 3
#UseDNS no
#PidFile /var/run/sshd.pid
#MaxStartups 10:30:100
#PermitTunnel no
#ChrootDirectory none
#VersionAddendum none
# no default banner path
#Banner none
# override default of no subsystems
Subsystem sftp sftp-server.exe
# Example of overriding settings on a per-user basis
#Match User anoncvs
# AllowTcpForwarding no
# PermitTTY no
# ForceCommand cvs server
Match Group administrators
AuthorizedKeysFile __PROGRAMDATA__/ssh/administrators_authorized_keys
重启sshd服务,若重启失败,可以手动结束sshd进程,然后启动sshd服务。
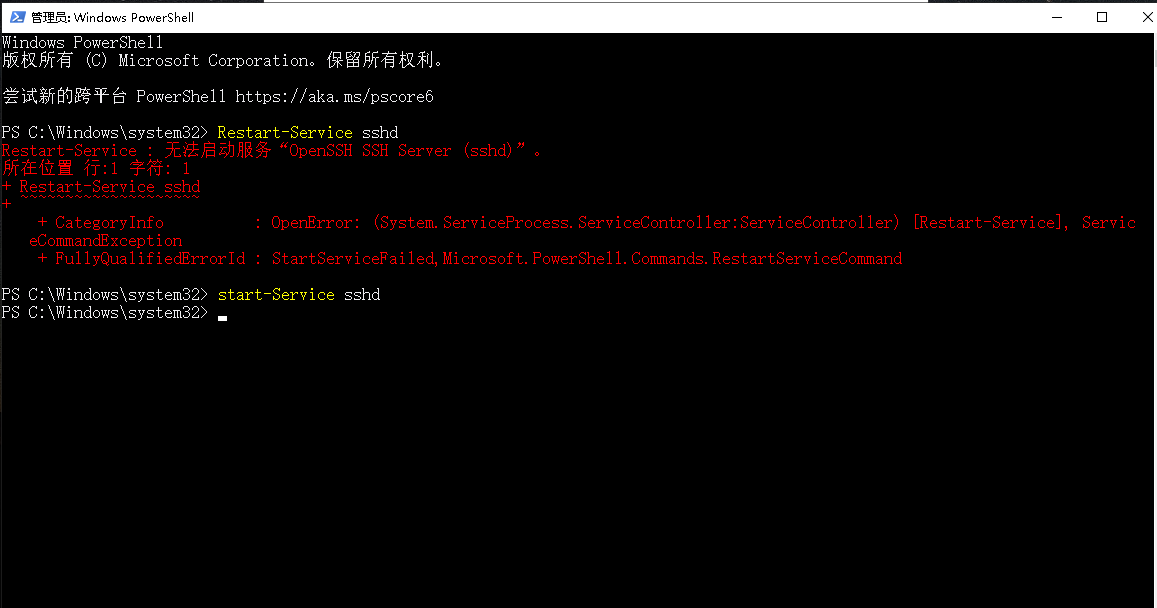
使用MobaXterm ssh 远程 windows,连接超时,推断是防火墙造成访问异常
关闭防火墙再次尝试
再次尝试,连接成功
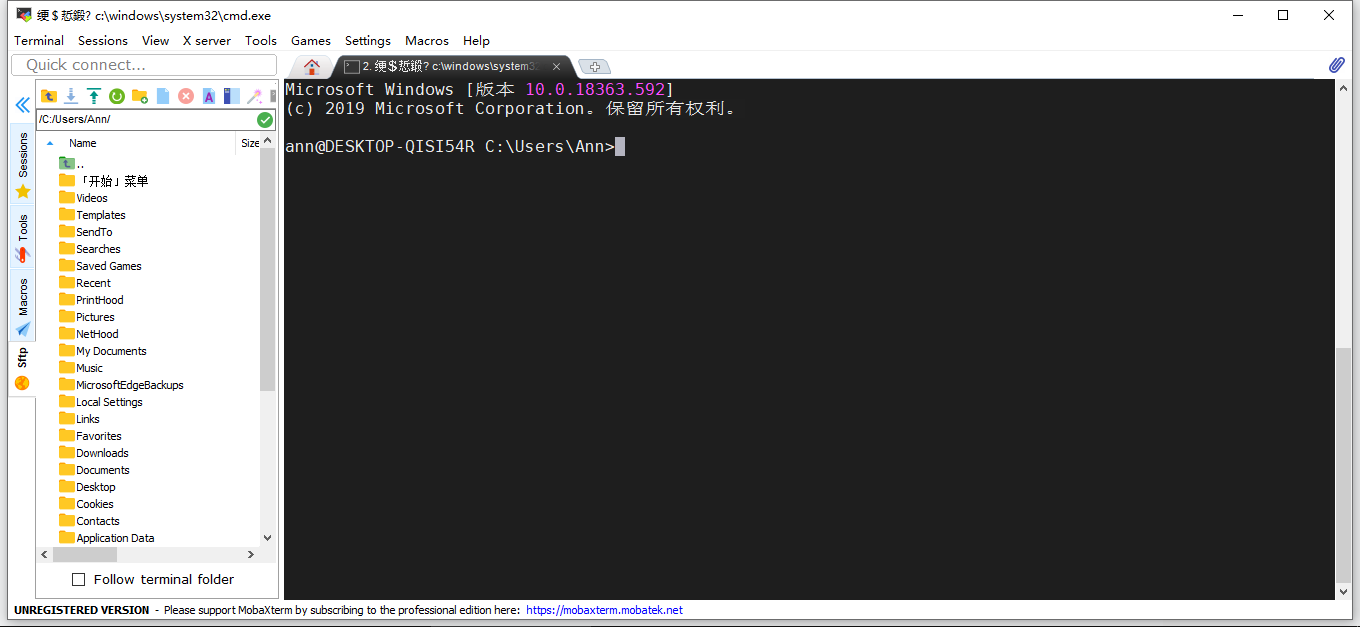
查看配置规则,
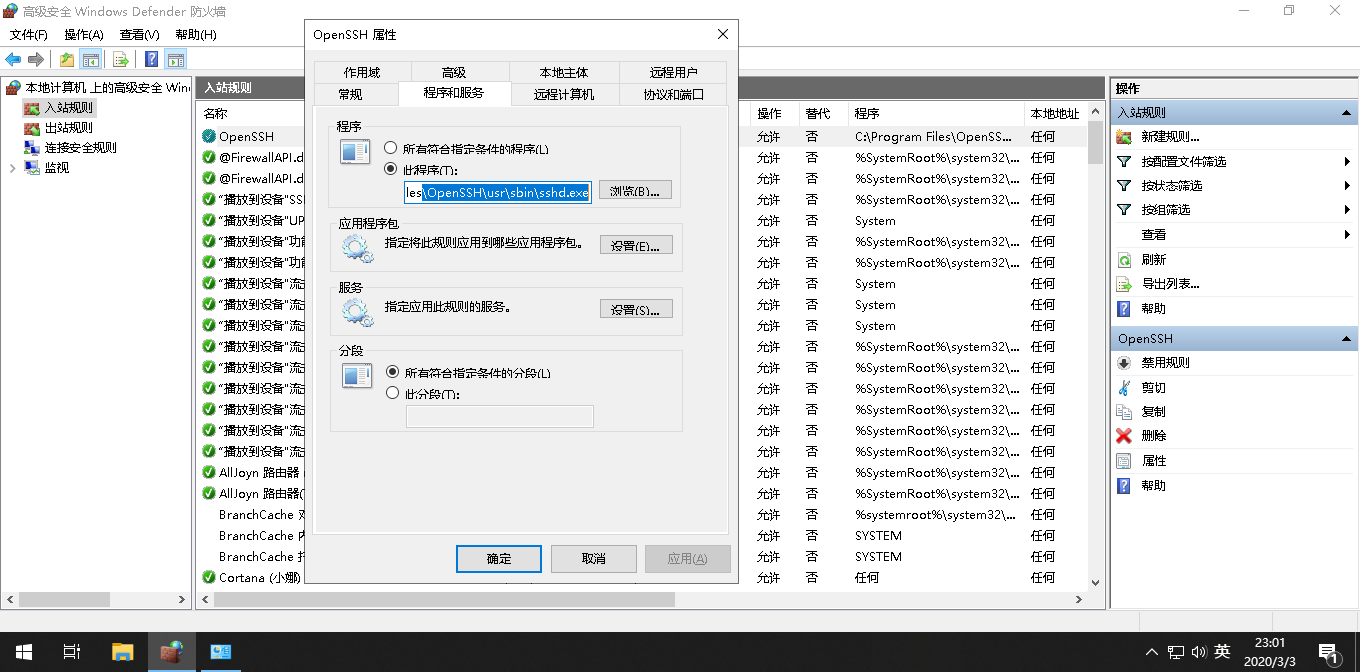
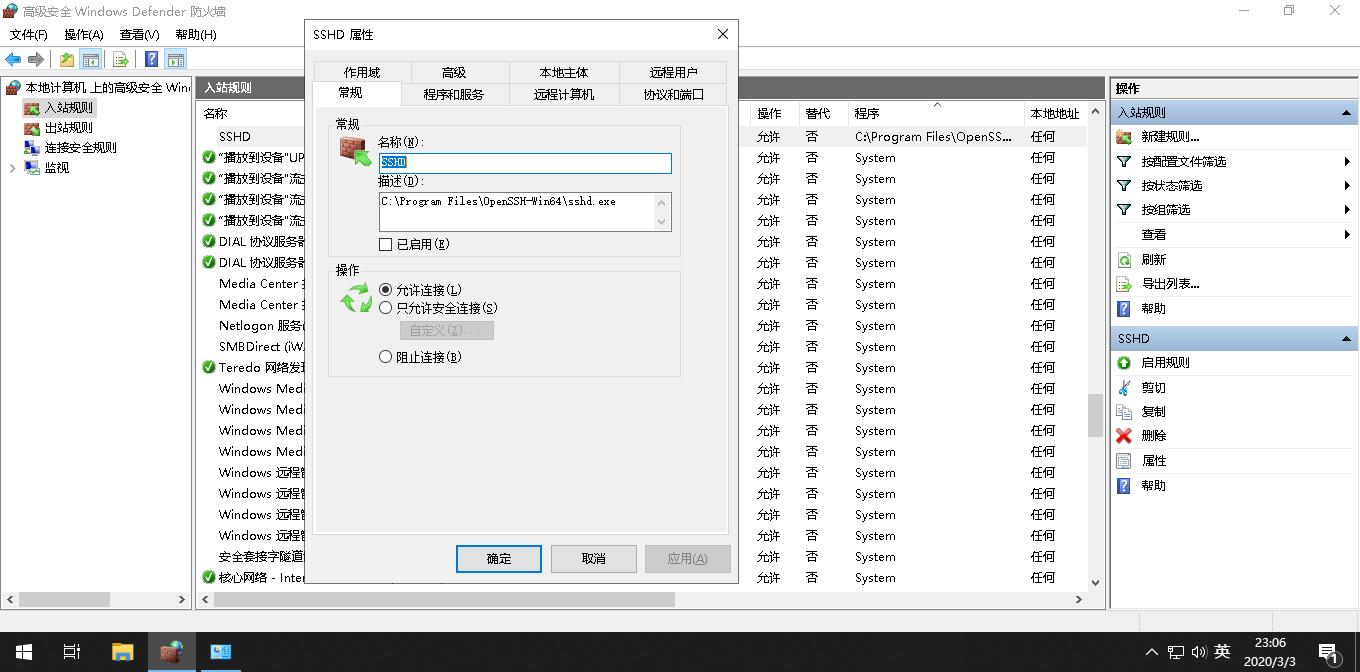
规则OpenSSH是之前Windows10 CMD 下 SSH 远程 Linux中安装的服务,不是我们目标服务,这里新加一条规则名为SSHD指向的程序是C:Program FilesOpenSSH-Win64sshd.exe, 通过协议TCP端口22,其他是默认配置(可以参照OpenSSH)。
然后开启防火墙,可以正常访问了。
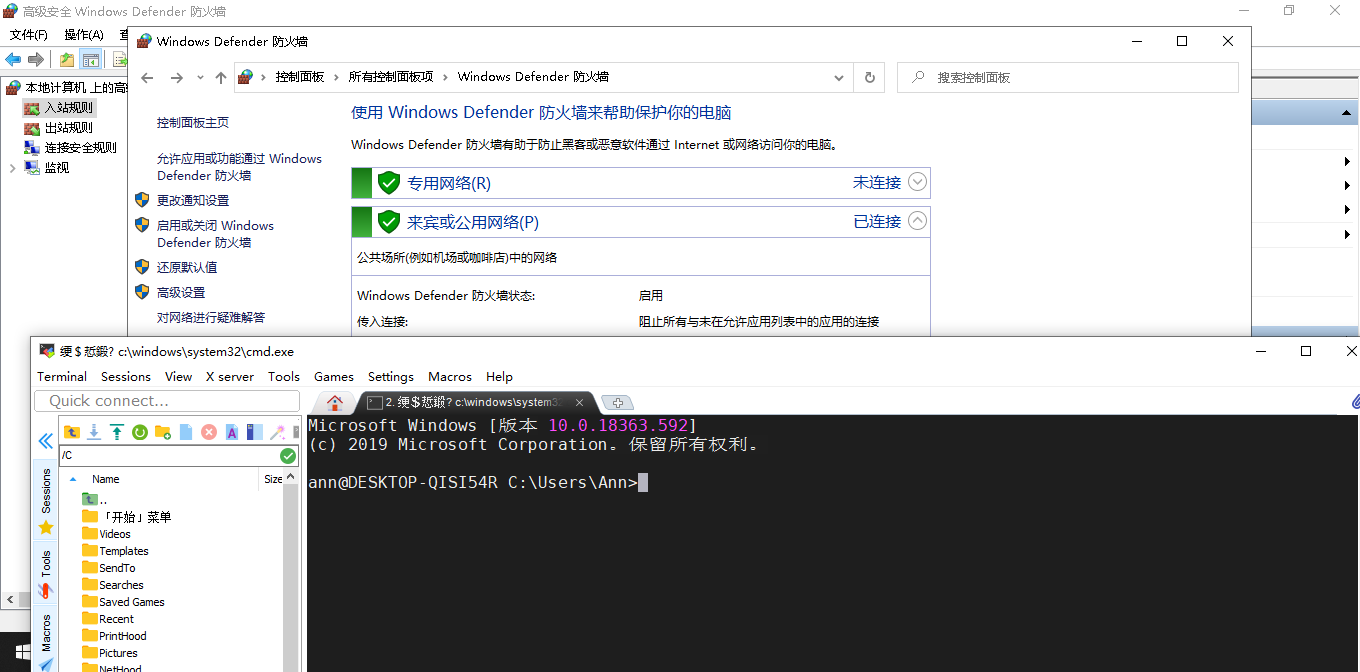
由于先安装的OpenSSH,后安装的 OpenSSH-Win64,这两者有什么不同,这里没有充分测试,有待后期补充,有知道的小伙伴请留言。
最后
以上就是野性小馒头最近收集整理的关于Windows Powershell 安装 SSHD 服务 支持ssh远程访问的全部内容,更多相关Windows内容请搜索靠谱客的其他文章。








发表评论 取消回复