拓扑

FW1地址配置
[USG6000V1]in g0/0/0
[USG6000V1-GigabitEthernet0/0/0]undo ip binding vpn-instance default
Info: All IPv4 related configurations on this interface are removed!
Info: All IPv6 related configurations on this interface are removed!
[USG6000V1-GigabitEthernet0/0/0]ip address 1.1.1.1 30
[USG6000V1-GigabitEthernet0/0/0]qu
[USG6000V1]interface Eth-Trunk 1.100
[USG6000V1-Eth-Trunk1.100]ip address 192.168.1.1 24
[USG6000V1-Eth-Trunk1.100]vlan-type dot1q 100
[USG6000V1-Eth-Trunk1.100]qu
[USG6000V1]interface Eth-Trunk 1.200
[USG6000V1-Eth-Trunk1.200]ip address 192.168.2.1 24
[USG6000V1-Eth-Trunk1.200]vlan-type dot1q 200
[USG6000V1-Eth-Trunk1.200]qu
[USG6000V1]interface Eth-Trunk 1
[USG6000V1-Eth-Trunk1]qu
[USG6000V1]interface g1/0/0
[USG6000V1-GigabitEthernet1/0/0]e
[USG6000V1-GigabitEthernet1/0/0]eth-trunk 1
[USG6000V1-GigabitEthernet1/0/0]in g1/0/1
[USG6000V1-GigabitEthernet1/0/1]eth-trunk 1
FW1安全域配置
[USG6000V1]firewall zone trust
[USG6000V1-zone-trust]undo add interface g0/0/0
[USG6000V1-zone-trust]add interface Eth-Trunk
[USG6000V1-zone-trust]add interface Eth-Trunk 1.100
[USG6000V1-zone-trust]add interface Eth-Trunk 1.200
[USG6000V1-zone-trust]qu
[USG6000V1]firewall zone dmz
[USG6000V1-zone-dmz]add interface g0/0/0
[USG6000V1-zone-dmz]qu
[USG6000V1]security-policy
[USG6000V1-policy-security] rule name local-trust
[USG6000V1-policy-security-rule-local-trust]source-zone local
[USG6000V1-policy-security-rule-local-trust]destination-zone trust
[USG6000V1-policy-security-rule-local-trust]action permit
[USG6000V1-policy-security-rule-local-trust]qu
[USG6000V1-policy-security]
[USG6000V1-policy-security]rule name trust-local
[USG6000V1-policy-security-rule-trust-local]source-zone trust
[USG6000V1-policy-security-rule-trust-local]destination-zone local
[USG6000V1-policy-security-rule-trust-local]action permit
[USG6000V1-policy-security-rule-trust-local]qu
[USG6000V1-policy-security]rule name
[USG6000V1-policy-security]rule name local-dmz
[USG6000V1-policy-security-rule-local-dmz]source-zone local
[USG6000V1-policy-security-rule-local-dmz]destination-zone dmz
[USG6000V1-policy-security-rule-local-dmz]action permit
[USG6000V1-policy-security-rule-local-dmz]qu
[USG6000V1-policy-security]rule name
[USG6000V1-policy-security]rule name dmz-local
[USG6000V1-policy-security-rule-dmz-local]source-zone dmz
[USG6000V1-policy-security-rule-dmz-local]source-zone dmz
[USG6000V1-policy-security-rule-dmz-local]destination-zone local
[USG6000V1-policy-security-rule-dmz-local]action permit
FW2的初始配置和FW1几乎一样,不过多赘述
FW1、FW2VRRP配置
[USG6000V1]interface Eth-Trunk 1.100
[USG6000V1-Eth-Trunk1.100]vrrp vrid 100 virtual-ip 192.168.1.3 active
[USG6000V1]interface Eth-Trunk 1.200
[USG6000V1-Eth-Trunk1.200]vrrp vrid 200 virtual-ip 192.168.2.3 standby
[USG6000V1]interface Eth-Trunk 1.100
[USG6000V1-Eth-Trunk1.100]vrrp vrid 100 virtual-ip 192.168.1.3 24 standby
[USG6000V1]interface Eth-Trunk 1.200
[USG6000V1-Eth-Trunk1.200]vrrp vrid 200 virtual-ip 192.168.2.3 active
这里采用FW1为组100的主,FW2为组200的主,这样做如果是普通的VRRP是没问题的,但是如果配置了hrp就会出现问题,hrp会出现双主现象。
FW1 和FW2 的HRP状态

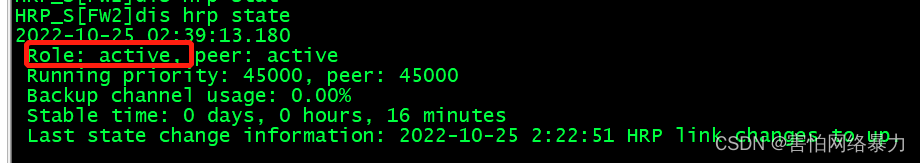
虽然状态是normal,但是两边的角色都是active,并且hrp的hello报文收发都是正常的,会话也是正常的,但是在实际项目中,为了避免对业务造成影响,建议把一台防火墙作为所有组的主,另一台作为备。

修改之后,FW2的hrp状态变为standby
HRP_M[FW1]interface Eth-Trunk 1.200 (+B)
HRP_M[FW1-Eth-Trunk1.200]undo vrrp vrid 200 virtual-ip 192.168.2.3
HRP_M[FW1-Eth-Trunk1.200]vrrp vrid 200 virtual-ip 192.168.2.3 active
HRP_S[FW2]interface Eth-Trunk 1.200
HRP_S[W2-Eth-Trunk1.200]undo vrrp vrid 200 virtual-ip 192.168.2.3
HRP_S[FW2-Eth-Trunk1.200]vrrp vrid 200 virtual-ip 192.168.2.3 standby


结论
我们规划主用设备(业务主和配置主)所有VRRP备份组状态都配置为active,备用设备(业务备和配置备)所有VRRP备份组状态都配置为standby。VRRP备份组状态(配置)决定双机热备HRP中的主用设备和备用设备,这个结论未在华为产品手册中找到,是根据现网实施和模拟实验的推论。**
最后
以上就是哭泣小鸭子最近收集整理的关于防火墙双机设备(旁挂组网),HRP双主原因的全部内容,更多相关防火墙双机设备(旁挂组网)内容请搜索靠谱客的其他文章。
本图文内容来源于网友提供,作为学习参考使用,或来自网络收集整理,版权属于原作者所有。








发表评论 取消回复